Can iPhones get viruses? Though rare, iPhones can get viruses and other malware, especially if the phone is jailbroken or if the victim is targeted in a high-value spear phishing attack. For normal iPhone users, a malware infection is an unlikely event.
Is the iPhone virus warning real?
Apple Security Alert is a fake pop-up message which states that your iOS device was hacked and that your personal information is at risk. Users can get this alert by visiting a suspicious website or get redirected if they have a potentially unwanted program (PUP) installed on their Mac or iPhone.
Can iPhones get viruses from websites?
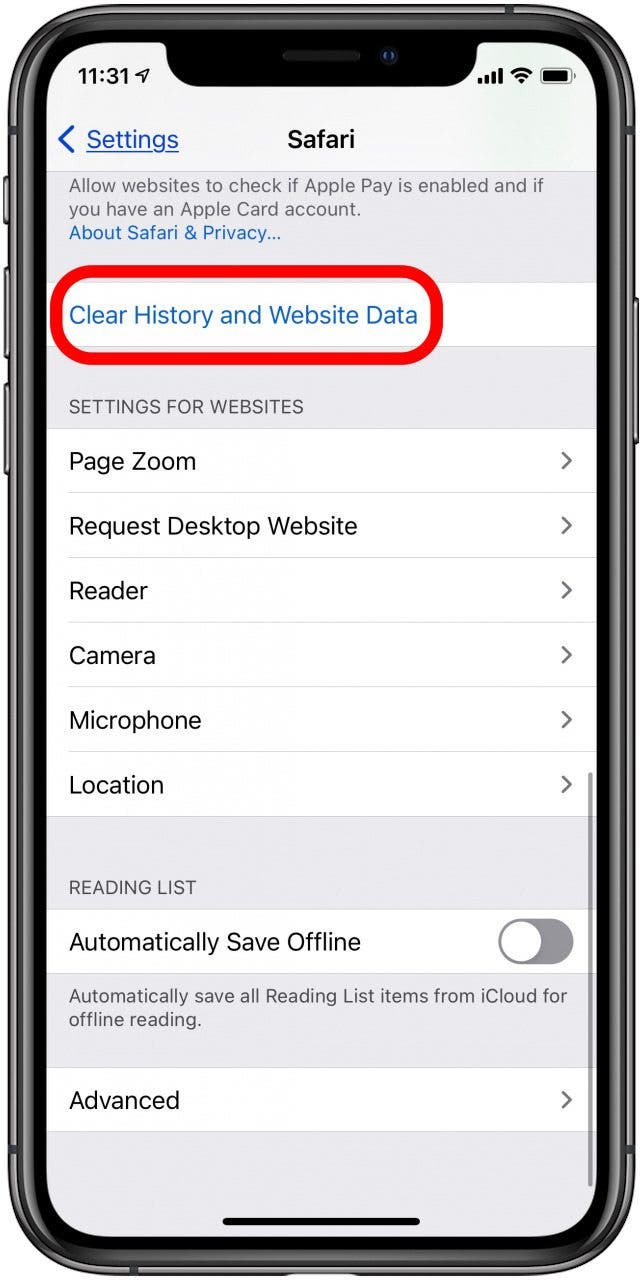
Viruses can live in your browser history or website data, especially if you revisit a suspect website on your phone often. Viruses can re-inject files onto your phone, perhaps doing more damage. Here’s how to reset your website history and data: Open the Settings app on your iPhone.
Can iPhones get viruses from websites?
Viruses can live in your browser history or website data, especially if you revisit a suspect website on your phone often. Viruses can re-inject files onto your phone, perhaps doing more damage. Here’s how to reset your website history and data: Open the Settings app on your iPhone.
Why did I get a message saying my iPhone has a virus?
If you get a virus warning in a pop-up, the first thing to remember is that Apple doesn’t send out messages like these; don’t tap on it or call any numbers listed on the fake alert. Don’t even tap on the pop-up to close it!
Why do I get pop ups saying my iPhone has a virus?
In fact, a virus pop-up like this was once created by scammers to acquire iCloud accounts or credit card information from the victims. The purpose of these scam alerts is to scare people that something would seriously go wrong with their iPhones if they don’t comply with the requisites.
What if I accidentally clicked on a suspicious link on my iPhone?
Disconnect from the internet immediately. This is to isolate your machine from infecting other devices and to cut off access to your machine from the hacker. This may help contain the malware infection. If you are on a wired connection, unplug. If you are on a Wi-Fi connection, disconnect from the Wi-fi in settings.
Can your iPhone get hacked by clicking on a link?
2. Avoid clicking suspicious links. Just like on your computer, your iPhone can be hacked by clicking on a suspicious website or link. If a website looks or feels “off” check the logos, the spelling, or the URL.
Does Apple have a virus scan?
macOS includes built-in antivirus technology called XProtect for the signature-based detection and removal of malware. The system uses YARA signatures, a tool used to conduct signature-based detection of malware, which Apple updates regularly.
Can an iPhone be hacked by visiting a website?
iPhones can get hacked from websites, which is why it’s best to use antivirus software to scan for malicious sites.
Can an iPhone get a Trojan virus?
Malicious software includes Trojan horses, viruses, and spyware programs. Although viruses are uncommon on the iPhone, it’s possible to get infected with an iPhone Trojan or spyware that can expose your phone’s activity to a third party. Keeping your iOS up to date can greatly reduce the chances of this happening.
Can iPhones get viruses from websites?
Viruses can live in your browser history or website data, especially if you revisit a suspect website on your phone often. Viruses can re-inject files onto your phone, perhaps doing more damage. Here’s how to reset your website history and data: Open the Settings app on your iPhone.
Is the virus warning on my phone real?
The Virus Warning Pop-Up on Android In most cases, Android users only see a fake virus warning pop-up when using the web browser to visit a malicious website. The pop-up window warns you that your Android is infected with a virus and invites you to tap a button to run a scan and remove the software from your device.
Can you Unhack your phone?
If you’ve recently sideloaded apps on Android, they might be to blame for the hack. Therefore, to unhack your phone, delete all recently-downloaded apps from it.
Can you check to see if your phone is hacked?
Use the code *#21# to see if hackers track your phone with malicious intent. You can also use this code to verify if your calls, messages, or other data are being diverted. It also shows your diverted information’s status and the number to which the information is transferred.prieš 7 dienas
Can someone else access my iPhone?
If your iPhone backs everything up to your iCloud account, then someone can spy on your activity by accessing your iCloud account from any web browser. They would need your Apple ID username and password in order to do this, so if you know that a third party has that information, there are a few steps you should take.
Can I scan my iPhone for malware?
It is not possible for an iOS app to scan for malware. Fortunately, the risk of getting malware on an iOS device is low and Apple has a stringent review process regarding app admission into the App Store. Devices we work on: Devices running iOS version 14or higher with an active Internet connection.
Does iPhone have built in antivirus?
You’ve been conditioned to believe every device needs the best antivirus software, but that isn’t true for Apple’s iPhones and iPads. While many security companies offer products that support the iPhone, they’re not really antivirus software; Apple has made sure that you don’t need it. Why?
Do you need virus protection on an iPhone?
Fortunately for Apple iPhone users, most of those apps are unnecessary. While iPhones can get viruses, they’re exceedingly rare. That’s because of the Apple iPhone security protections puts in place.
Can my iPhone be hacked through WIFI?
Unfortunately yes, your phone can be hacked via Wi-Fi. Hackers know how to hack into your phone (especially over public Wi-Fi networks) like any other physical device, regardless of whether you’re using an iPhone or an Android phone.
What do I dial to see if my phone has been hacked?
Use the code *#21# to see if hackers track your phone with malicious intent. You can also use this code to verify if your calls, messages, or other data are being diverted. It also shows your diverted information’s status and the number to which the information is transferred.prieš 7 dienas
Does resetting iPhone remove malware?
Answer: Resetting the phone or clearing all the data will most probably remove any spyware, malware, or virus available on your device. But it should be the last option. First, try deleting unwanted apps and the apps that ask for access to your personal information, then try restoring your device to a previous backup.