In some cases, hackers can even open the ports themselves in order to access the targeted computer. Hackers also use port scanners to conduct tests for open ports on Personal Computers that are connected to the web.
Why do hackers look for open ports?
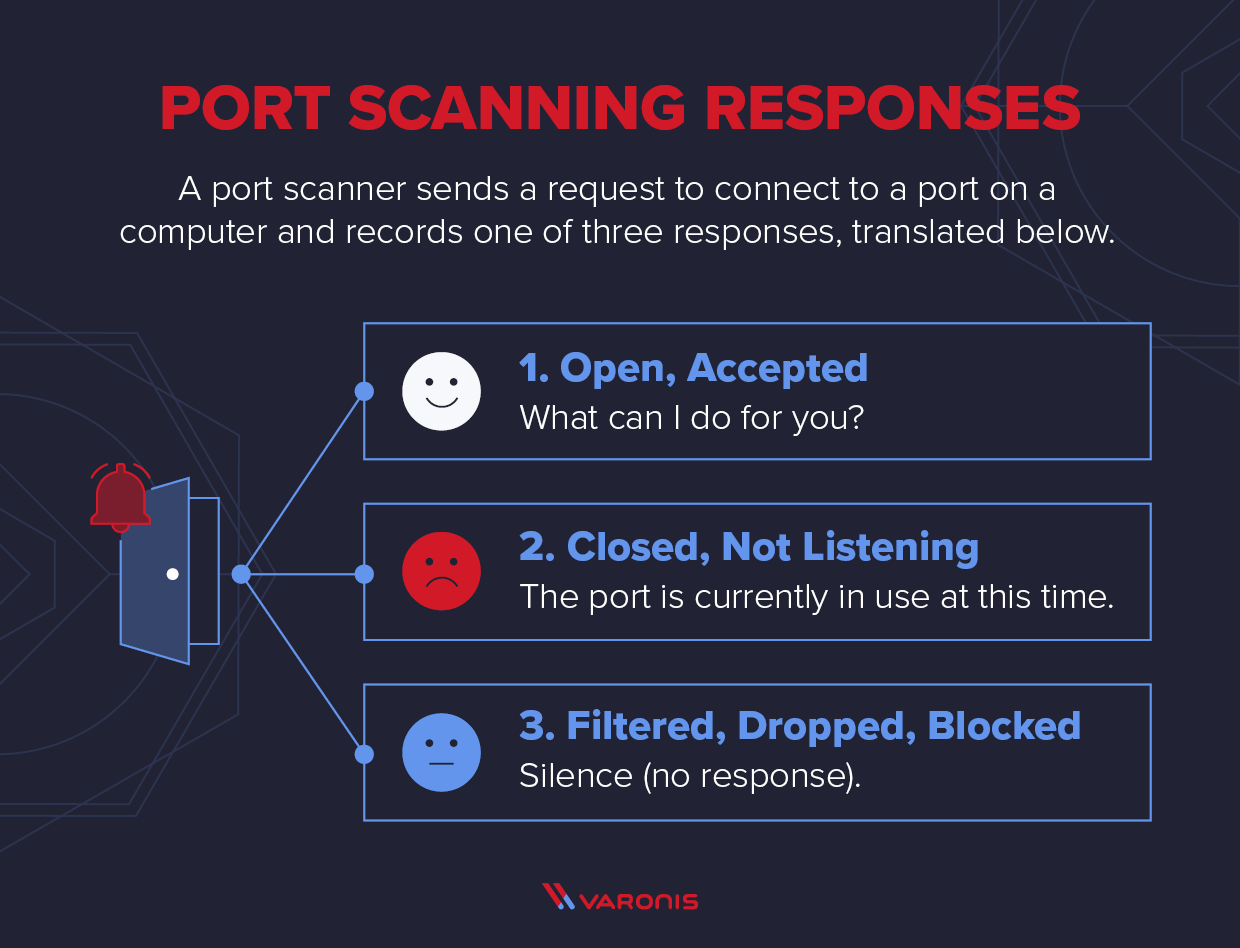
During a port scan, hackers send a message to each port, one at a time. The response they receive from each port determines whether it’s being used and reveals potential weaknesses. Security techs can routinely conduct port scanning for network inventory and to expose possible security vulnerabilities.
What ports do hackers look for?
Though the number of commonly hacked ports has constantly grown in the past years, it is important to keep in mind that most attackers are looking first in probing ports 22 [SSH] and 80 [HTTP]. For instance, port 22 [SSH] is a common port constantly probed by hackers on the Internet using brute force attacks.
How do attackers use open ports?
Attackers use open ports to find potential exploits. To run an exploit, the attacker needs to find a vulnerability. To find a vulnerability, the attacker needs to fingerprint all services that run on a machine, including what protocols it uses, which programs implement them, and ideally the versions of those programs.
Can port 443 be hacked?
No. “Port 443” can not be hacked. Neither can any other port.
What do hackers want when they hack?
Some common reasons for hacking include basic bragging rights, curiosity, revenge, boredom, challenge, theft for financial gain, sabotage, vandalism, corporate espionage, blackmail, and extortion. Hackers are known to regularly cite these reasons to explain their behavior.
What do most hackers want?
Stolen personal information is fuel for identity theft Many online services require users to fill in personal details such as full name, home address and credit card number. Criminals steal this data from online accounts to commit identity theft, such as using the victim’s credit card or taking loans in their name.
Is port 443 a security risk?
With port 443, the connection is much more secure as the information is encrypted through SSL/TLS (secure sockets layer/transport layer security). With port 80, all information is transferred in plaintext and available to anyone to see. Port 443 is the global standard port for HTTPS traffic.
Is a port open if it is listening?
So, opening a port means making it available to the outside if an application is listening. If it isn’t, it will show as “closed” on nmap scans.
What ports should never be open?
Ports 80, 443, 8080 and 8443 (HTTP and HTTPS) They’re especially vulnerable to cross-site scripting, SQL injections, cross-site request forgeries and DDoS attacks.
Why are open ports vulnerable?
Security Risks Linked to Ports Numerous incidents have demonstrated that open ports are most vulnerable to attack when the services listening to them are unpatched or insufficiently protected or misconfigured, which can lead to compromised systems and networks.
Can closed ports be hacked?
In theory – yes, your computer can still be hacked even, if all TCP and UDP ports are closed and you don’t have any malware running on it. However, odds of getting your computer hacked, if all ports are closed, is way lower compared to a system where a web server is listening on publicly accessible port.
What are hackers scared of?
Getting hacked. Hackers and crackers are extremely paranoid about their online activities; it would be the ultimate embarrassment to get hacked themselves.
Do hackers use coding to hack?
Access Hardware: Hackers use C programming to access and manipulate system resources and hardware components such as the RAM. Security professionals mostly use C when they are required to manipulate system resources and hardware. C also helps penetration testers write programming scripts.vor 6 Tagen
Can hackers look at your screen?
Hackers can gain access to your computer monitor — a cybersecurity expert shows us how easy it is.
Can a hacker see you through your screen?
On top of that, popular app developers aren’t immune to accusations of watching you through your phone’s camera. Generally, however, a stalker would need to install spyware on your device in order to compromise it. Hackers can gain access to your phone physically, through apps, media files, and even emojis.
Do hackers ever get caught?
Due to the sophisticated tactics that hackers use to cover their tracks, it’s extremely difficult to catch them and bring them to justice. Only 5% of cybercriminals are apprehended for their crimes which demonstrates just how challenging it is for law enforcement agencies to arrest and prosecute these offenders.
Is port 22 always secure?
As such, Port 22 is subject to countless, unauthorized login attempts by hackers who are attempting to access unsecured servers. A highly effective deterrent is to simply turn off Port 22 and run the service on a seemingly random port above 1024 (and up to 65535).
What ports are safe to open?
Most ports are safe. At this writing, any port in the 5000s, 7000s and 9000s is safe.
What is the most secure port?
Port 22 is SSH (Secure Shell), port 80 is the standard port for HTTP (Hypertext Transfer Protocol) web traffic, and port 443 is HTTPS (Hypertext Transfer Protocol Secure)—the more secure web traffic protocol.
What ports are listening?
The Listening Ports section of the Network tab gives you information about the services and processes on your system that are waiting to service network requests. These services are listening on either a TCP or a User Datagram Protocol (udp) port.
Do hackers use nmap?
Nmap can be used by hackers to gain access to uncontrolled ports on a system. All a hacker would need to do to successfully get into a targeted system would be to run Nmap on that system, look for vulnerabilities, and figure out how to exploit them. Hackers aren’t the only people who use the software platform, however.