If the root account has an empty password, your MySQL installation is unprotected: Anyone can connect to the MySQL server as root without a password and be granted all privileges.
How do I bypass MySQL password?
Login to the MySQL shell as root. Access the MySQL shell by typing the following command and enter your MySQL root user password when prompted: mysql -u root -p. Set the MySQL user password. Verify the new password.
Does MySQL have a default password?
The default user for MySQL is root and by default it has no password. If you set a password for MySQL and you can’t recall it, you can always reset it and choose another one.
How do I log into MySQL database?
Enter mysql.exe -uroot -p , and MySQL will launch using the root user. MySQL will prompt you for your password. Enter the password from the user account you specified with the –u tag, and you’ll connect to the MySQL server.
How do I find MySQL user ID and password?
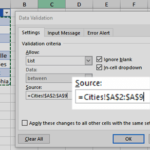
So for example, to show MySQL users’ username, password and host, we’ll modify the sql query to accordingly as such: mysql> select user, password, host from mysql. user; The above sql query will present you with a list of users and their respective user name, password and database host.
What is the purpose of a password key?
A physical key serves as a backup to your password for verifying your identity. The right type of key can work with your computer and mobile phone, through a physical or wireless connection.
What is the reason for using password?
Passwords provide the first line of defense against unauthorized access to your computer and personal information. The stronger your password, the more protected your computer will be from hackers and malicious software.
What is the purpose of hashing a password?
Hashing turns your password (or any other piece of data) into a short string of letters and/or numbers using an encryption algorithm. If a website is hacked, cyber criminals don’t get access to your password. Instead, they just get access to the encrypted “hash” created by your password.
What is the purpose of a password vault?
A password vault, password manager or password locker is a program that stores usernames and passwords for multiple applications securely, and in an encrypted format. Users can access the vault via a single “master” password. The vault then provides the password for the account they need to access.
How do I connect to a MySQL user?
If you want to login as a different user on MySQL, you need to use “mysql -u -p command”.
How do I log into root without password?
you can also do “sudo su” which will give you the root shell without the password. where “user” is your real user name. then all commands that you need to run as root can be preceded with “sudo” and it will run with root privileges. you can also do “sudo su” which will give you the root shell without the password.
What is the default password for root?
The default password is “unitrends1”. It is highly recommended that you change this password from the default. Leaving the root account’s password at the default will cause the Unitrends interface to automatically log in when accessing the system.
How secure is MySQL?
MySQL protects sensitive data access by way of encryption. This can be done either by obscuring the container the data is held in or encrypting the data itself. Some MySQL Enterprise encryption tools include: Asymmetric Public Key Encryption/Decryption.
Do people still use MySQL?
MySQL Community Edition is the most widely used free database in the industry. Also, its commercial version is used extensively in the industry.
Is it safe to use MySQL?
MySQL offers encryption using the Secure Sockets Layer (SSL) protocol, data masking, authentication plugins, and other layers of security to protect data integrity. The MySQL Enterprise package also includes firewall protection against cyberattacks.
Is a security key the same as a password?
Is a network security key the same as a password? Yes – they essentially perform the same function. Each ISP and manufacturer will use slightly different phrasing, so even if you find the sticker on your router, you might not know what you’re looking at.
How do I find my security key?
Finding Your Hotspot Network Security Key on Android Step 1: In settings, go to Connections > Mobile Hotspot and Tethering. Step 2: Tap Mobile Hotspot. Step 3: Tap Password. Step 4: Select Show Password if there’s an option.
What is the difference between a private key and a password?
The password allows the encryption and the reverse process, decryption, of data. Using encryption, your private key is changed into an encrypted form that is unusable to anyone without the correct password. With the correct password, the original data containing your private key can be restored.
How do I stop asking for my password?
To do that, first, tap on the three vertical dots in the browser’s top-right corner. Then, access Settings. Next, press on Passwords. On the Passwords page, tap on the Save passwords option to turn off its switch.
Are passwords still necessary?
A password verifies the identity of an individual, since only the correct person would know the correct password. Requiring a password limits access to files and infrastructure, allowing multiple people with different levels of access to use the same systems.
Do hackers use hashing?
Storing your passwords in cleartext is a bad idea because if your server gets hacked, all your user passwords are immediately visible to the attacker. To protect a database of passwords in the event of a breach, businesses often employ one-way encryption using hashing to make passwords harder to use.
Can hash value be hacked?
However, when a hacker steals hashed passwords in a database, they can reverse engineer the hashes to get the real passwords by using a database of words they think might be the password. If any of the hashes match what the hacker has in the database, they now know the original password.