Can a JavaScript file be malicious?
Attackers frequently send malicious JavaScript files through bogus emails. It’s easy to block these files from reaching a hapless user.
Is JavaScript a threat?
Like nearly any programming language, JavaScript is not without its share of potential security exposures. Exploiting JavaScript vulnerabilities can manipulate data, redirect sessions, modify and steal data, and much more.
Should you allow JavaScript?
Should you enable JavaScript or not? For most users, JavaScript is pretty safe. If you’re doing something that makes you particularly concerned about security, you can turn JavaScript off, then easily turn it back on. But to get the most out of the modern web, it’s best to leave it on.
How can JavaScript be used maliciously?
One of the most insidious uses of JavaScript occurs in the form of cross-site scripting (XSS). Simply put, XSS is a vulnerability that allows hackers to embed malicious JavaScript code into an otherwise legitimate website, which is ultimately executed in the browser of a user who visits the site.
Why is JavaScript more susceptible to theft?
Since JavaScript code isn’t compiled into native code, apps built with this language are even more susceptible to code theft than traditional mobile apps.
Should you avoid JavaScript?
You should not avoid using JS and jQuery in your website, but you should avoid using them for validation purposes or business-logic purposes. These should be done in the back-end of the website, not in the UI level.
Why is JavaScript a security risk?
JavaScript is vulnerable because it is easy for hackers and other threat actors to input query strings into forms to access, steal, or contaminate protected data. JavaScript is the standard for the processing of personal information in client-side websites and applications.
Is JavaScript more secure?
From a security perspective, JavaScript is fourth on the list of the most vulnerable languages – only behind Java, PHP, and C. For this reason, developers must remain proactive and defensive in securing their JavaScript applications to keep the web safe.
Why JavaScript is used for security purpose?
One of the most common JavaScript security vulnerabilities is Cross-Site Scripting (XSS). Cross-Site Scripting vulnerabilities enable attackers to manipulate websites to return malicious scripts to visitors. These malicious scripts then execute on the client side in a manner determined by the attacker.
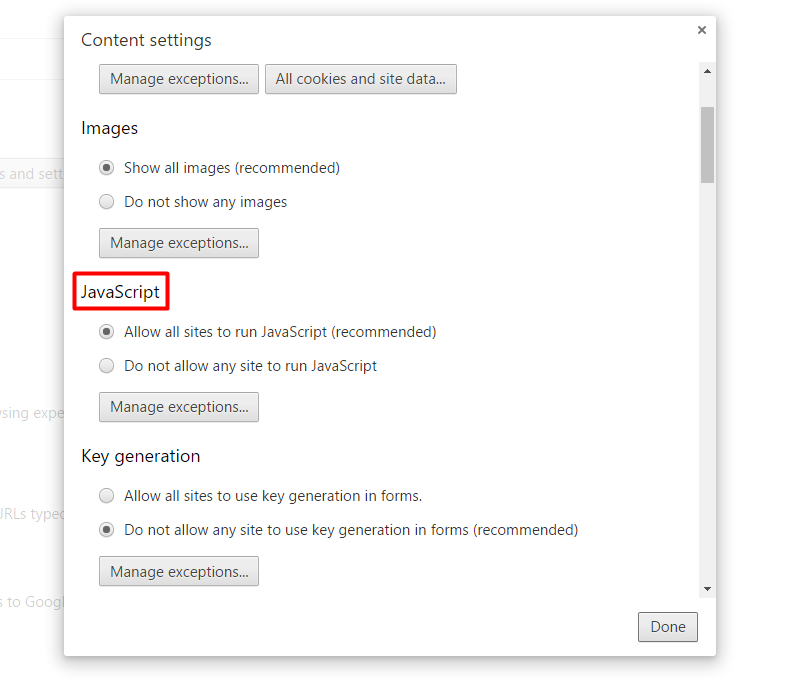
Can I turn off JavaScript?
Press Control+Shift+P or Command+Shift+P (Mac) to open the Command Menu. Start typing javascript , select Disable JavaScript, and then press Enter to run the command. JavaScript is now disabled. The yellow warning icon next to Sources reminds you that JavaScript is disabled.
Is JavaScript disabled in Chrome?
On Google Chrome, JavaScript is enabled by default, but you can verify if it works through the Settings menu. To reveal the Settings menu, simply click on three tiny black dots at the top-right corner of your Chrome window.
Why do I need JavaScript?
JavaScript has become integral to the Internet experience as developers build increased interaction and complexity into their applications. Search engines, ecommerce, content management systems, responsive design, social media and phone apps would not be possible without it.
Why do people block JavaScript?
Disabling Javascript can be quite beneficial as it allows you to improve your online activity and browsing speed. Security: The biggest issue with JavaScript is suspicious webpages. Furthermore, client browsers can insert malicious code that directly affects your computer.
Do I need JavaScript on my phone?
If your Android phone’s Web browser is configured to disable JavaScript, you’re going to have an impaired Web viewing experience. Android phone Web browsers support the ability to toggle JavaScript. JavaScript compatibility is essential to viewing a magnitude of websites on the Internet.
Do hackers use JavaScript?
JavaScript. Web Hacking: Currently, JavaScript is one of the best programming languages for hacking web applications. Understanding JavaScript allows hackers to discover vulnerabilities and carry web exploitation since most of the applications on the web use JavaScript or its libraries.
Is Java a secure language?
At its core, the Java language itself is type-safe and provides automatic garbage collection, enhancing the robustness of application code. A secure class loading and verification mechanism ensures that only legitimate Java code is executed.
What are the main uses of JavaScript?
JavaScript is frequently used to create in-browser games. Developers use JavaScript to create 2D and 3D puzzles, role-playing games, racing games, platform games, and more. Creating a simple browser game can be a great way to start practicing your JavaScript skills as a beginner.
Is Java safer than JavaScript?
Which is more secure Java or JavaScript?
Java was developed long after C, in an environment where threat consciousness was much higher, so it’s no surprise that Java is far more secure.
What is JavaScript injection?
A JavaScript injection attack is a type of attack in which a threat actor injects malicious code directly into the client-side JavasScript. This allows the threat actor to manipulate the website or web application and collect sensitive data, such as personally identifiable information (PII) or payment information.
Does JavaScript help you protect data or does it only expose vulnerabilities?
In short, JavaScript client-side applications are not 100% safe. The main reason is that there is no full control of the client-side as it is executed in the browser. Those with advanced skills can have access to critical information on the frontend and expose vulnerabilities.
How dangerous is a JavaScript virus?
In this sense, a Javascript virus is as dangerous as any other virus. Also, for web applications, JavaScript is one of the main attack vectors in techniques such as cross-site scripting (XSS) and cross-site request forgery (CSRF) because it’s rather easy to write for web.
Can anyone familiar with JavaScript confirm this is a virus?
Anyone familiar with javascript can confirm that it is a virus or not? It most certainly is malware. It uses JavaScript with ActiveX * and VBScript to download and execute a stage two payload that does something else. Although it is written in JavaScript, it is not executed in the browser.
How do malicious JavaScript files infect a computer?
The malicious JavaScript files are downloaded on your system. They are executed through your browser, triggering the malware infection. The infected JavaScript files silently redirect your Internet traffic to an exploit server. The exploit kit used in the attack (hosted on the exploit server)…
How is JavaScript used to spread malware?
There are 8 main ways in which JavaScript is used to spread malware in current cyber attacks: 1. Malicious JavaScript code injections in legitimate websites – used to redirect users to malware-laden websites or to exploit servers that trigger malware infections.