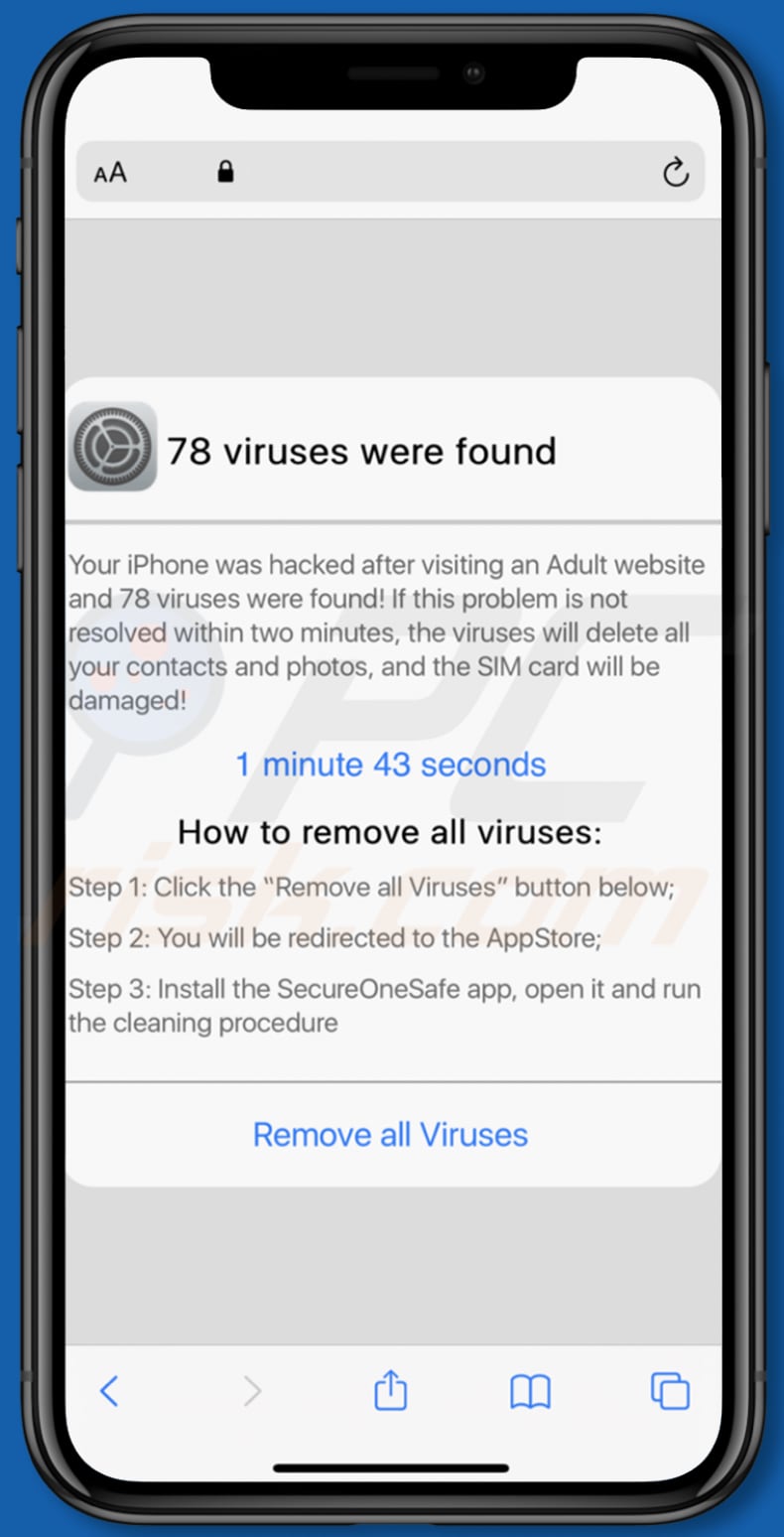
iPhones can get hacked from websites, which is why it’s best to use antivirus software to scan for malicious sites.
Can an iPhone get hacked from a website?
Just like on your computer, your iPhone can be hacked by clicking on a suspicious website or link. If a website looks or feels “off” check the logos, the spelling, or the URL.
Can your phone be hacked just by visiting a website?
The short answer to it is “yes”, in principle you can. As is often the case, however, the short answer only tells part of the story. The whole story helps to shed a lot more light on internet security.
Can iPhones be hacked easily?
A common way hackers can get to your iPhone is through malware links and scammy emails. You click a link in an email and unbeknownst to you, the link installs software that gives the hacker access to your iPhone. A good rule of thumb is to only open things (links, messages, emails) from sources you trust.
Can an iPhone get hacked from a website?
Just like on your computer, your iPhone can be hacked by clicking on a suspicious website or link. If a website looks or feels “off” check the logos, the spelling, or the URL.
Can iPhone get hacked through safari?
Apple Users’ Data Exposed? (Do This Urgently) Apple’s security mechanism is considered as impenetrable, and completely safe, secured. But this time, Apple may have missed a critical update, and failed to gauge the danger.
Can iPhones get viruses from websites?
Viruses can live in your browser history or website data, especially if you revisit a suspect website on your phone often. Viruses can re-inject files onto your phone, perhaps doing more damage. Here’s how to reset your website history and data: Open the Settings app on your iPhone.
What happens if you visit an unsecure website?
Insecure websites are vulnerable to cyberthreats, including malware and cyberattacks. If your site falls victim to a cyberattack, it can impact the site’s functioning, prevent visitors from accessing it, or compromise your customers’ personal information.
Can you Unhack your phone?
If you’ve recently sideloaded apps on Android, they might be to blame for the hack. Therefore, to unhack your phone, delete all recently-downloaded apps from it.
Can I scan my iPhone for malware?
It is not possible for an iOS app to scan for malware. Fortunately, the risk of getting malware on an iOS device is low and Apple has a stringent review process regarding app admission into the App Store. Devices we work on: Devices running iOS version 14or higher with an active Internet connection.
Can an iPhone get hacked from a website?
Just like on your computer, your iPhone can be hacked by clicking on a suspicious website or link. If a website looks or feels “off” check the logos, the spelling, or the URL.
Can websites steal your information on iPhone?
iPhones can get hacked from websites, which is why it’s best to use antivirus software to scan for malicious sites. Can an iPhone be hacked remotely? An iPhone can be hacked remotely through iOS vulnerabilities.
Does Apple notify you if your iPhone was hacked?
If Apple detects evidence of a state-sponsored attack, the targeted user will get a Threat Notification on the top of the page when signed into appleid.apple.com. Apple will also send an email and iMessage notification to the account associated with the user’s Apple ID.
Is Safari safer than chrome on iPhone?
Both browsers are pretty similar in security, but Chrome has a slight edge thanks to a host of customizable security extensions. The Safari password management trumps Chrome, though, and is invaluable for users of Apple devices.
What if I accidentally clicked on a suspicious link on my iPhone?
Disconnect from the internet immediately. This is to isolate your machine from infecting other devices and to cut off access to your machine from the hacker. This may help contain the malware infection. If you are on a wired connection, unplug. If you are on a Wi-Fi connection, disconnect from the Wi-fi in settings.
Can hackers see you through your phone camera?
On top of that, popular app developers aren’t immune to accusations of watching you through your phone’s camera. Generally, however, a stalker would need to install spyware on your device in order to compromise it. Hackers can gain access to your phone physically, through apps, media files, and even emojis.
Does Apple have a virus scan?
macOS includes built-in antivirus technology called XProtect for the signature-based detection and removal of malware. The system uses YARA signatures, a tool used to conduct signature-based detection of malware, which Apple updates regularly.
Does resetting iPhone remove virus?
No virus can survive on the iPhone through a factory reset, so you should take the phone to an Apple store for servicing.
Does Apple notify you if you have a virus?
Does Apple security send virus warnings? No, Apple security doesn’t notify about already installed malware on your device.
How can I check to see if a website is safe?
Fortunately, there are two quick checks to help you be certain: Look at the uniform resource locator (URL) of the website. A secure URL should begin with “https” rather than “http.” The “s” in “https” stands for secure, which indicates that the site is using a Secure Sockets Layer (SSL) Certificate.
What does a malicious website look like?
Telltale signs of a malicious website For example: The website automatically asks you to run software or download a file when you’re not expecting to do so. The website tells you that your device is infected with malware or that your browser extensions or software are out-of-date.
Can someone hack your phone just by knowing your number?
But is it actually true that someone could hack my phone only by knowing my number? Quite simply – no, it isn’t.