Once a scammer has a person on the phone, the scammer often asks to remotely access the person’s computer. Once inside, the scammer can download malware, steal passwords, or try to sell unnecessary services or products—including products that are available elsewhere for free—for non-existent problems.
Can you tell if someone has hacked your computer?
Frequent pop-up windows, especially the ones that encourage you to visit unusual sites, or download antivirus or other software. Changes to your home page. Mass emails being sent from your email account. Frequent crashes or unusually slow computer performance.
Can hackers access your computer?
Many people set up unique passwords for their computer or phone, but neglect to do so for their Internet router or other smart device. Unknown to the user, hackers can easily gain access to these devices, and use them to flood websites with so much traffic the site goes down or hack into your network.
What is the first thing you do when you get hacked?
Step 1: Change your passwords This is important because hackers are looking for any point of entry into a larger network, and may gain access through a weak password. On accounts or devices that contain sensitive information, make sure your password is strong, unique—and not easily guessable.
What happens when a hacker gets into your computer?
The hacker could be across the street or across the country. No matter where they are, they can copy photos from your computer onto theirs, or delete your tax records. They can steal your personal data or delete the programs you have on your computer. Worse yet, they can download more viruses.
Is someone spying on my computer?
To open the Activity Monitor, hit Command + Spacebar to open Spotlight Search. Then, type Activity Monitor and press Enter. Check over the list for anything you don’t recognize. To close out a program or process, double click, then hit Quit.
Can someone remotely access my computer when it’s off?
Without appropriate security software installed, such as anti-malware tools like Auslogics Anti-Malware, it is possible for hackers to access the computer remotely even if it is turned off.
Who is the No 1 hacker in world?
Kevin Mitnick is the world’s authority on hacking, social engineering, and security awareness training. In fact, the world’s most used computer-based end-user security awareness training suite bears his name. Kevin’s keynote presentations are one part magic show, one part education, and all parts entertaining.
Can you Unhack your phone?
If you’ve recently sideloaded apps on Android, they might be to blame for the hack. Therefore, to unhack your phone, delete all recently-downloaded apps from it.
What happens if a scammer has your email?
What will scammers do with your email address? Once a scammer gets your email address, they’ll use it to benefit themselves in any way possible. Many will send you spam email, with the hope of collecting private information such as credit card numbers.
Does changing password stop hackers?
Yes, changing your password will prevent hackers from accessing your account. Updating your account password at the first sign of an attack limits damage. Changing your password regularly also improves security. Stolen credentials in data breaches are often old.
Does shutting down computer stop hackers?
In general, the answer is no, you cannot hack into a computer that’s been turned off. Unless two conditions are met, the PC cannot be restarted and hacked from outside, even if you leave it connected to the internet and to power.
Can WIFI be hacked?
Brute-force hacking your Wi-Fi password: Hackers can try hundreds of different password combinations to gain access to your router’s internal settings. If your Wi-Fi password is cracked, hackers will change the password and lock you out of your home Wi-Fi.
Can WIFI be hacked remotely?
Yes, it’s absolutely possible for your home network to get hacked. There are a couple of ways hackers can gain access to your network. One common method is to guess the password. It sounds simple, but routers often come with a preset default password that the manufacturer uses for all devices.
What do I dial to see if my phone has been hacked?
Use the code *#21# to see if hackers track your phone with malicious intent. You can also use this code to verify if your calls, messages, or other data are being diverted. It also shows your diverted information’s status and the number to which the information is transferred.prieš 4 dienas
Can a computer be hacked without Internet?
Can an Offline Computer be Hacked? Technically — as of right now — the answer is no. If you never connect your computer, you are 100 percent safe from hackers on the internet. There is no way someone can hack and retrieve, alter or monitor information without physical access.
Open task manager by right-clicking on the taskbar and choosing Task Manager. If there’s a suspicious process, that’s the monitoring app. Question: Can my company see what I do on my computer? Answer: Your company can see your device activities and track them if they provide you with that computer.
Should you cover the camera on your laptop?
Cybercriminals can access these cameras, and because of their positions — facing your living room, kitchen, or office — they can expose your privacy and sensitive conversations. That’s why it’s a good idea to cover up your webcam or take other steps to improve your internet security.
Can your computer be tracked?
Monitoring a computer is really easy for hackers. They can use a small piece of software called a keylogger. This software will note all your keystrokes and mouse movements. It will also take screenshots of your screen and send them to the hacker.
How can I tell who is remoted into my computer?
Click the Tools tab. In the Windows Tools section, click Remote Control. Click. against the name of a computer to view its remote-control history.
Can WIFI be hacked?
Brute-force hacking your Wi-Fi password: Hackers can try hundreds of different password combinations to gain access to your router’s internal settings. If your Wi-Fi password is cracked, hackers will change the password and lock you out of your home Wi-Fi.
Should I worry if someone has my IP address?
No, you shouldn’t worry if someone has your IP address. If someone has your IP address, they could send you spam or restrict your access to certain services. In extreme cases, a hacker might be able to impersonate you. However, all you need to do to fix the problem is change your IP address.
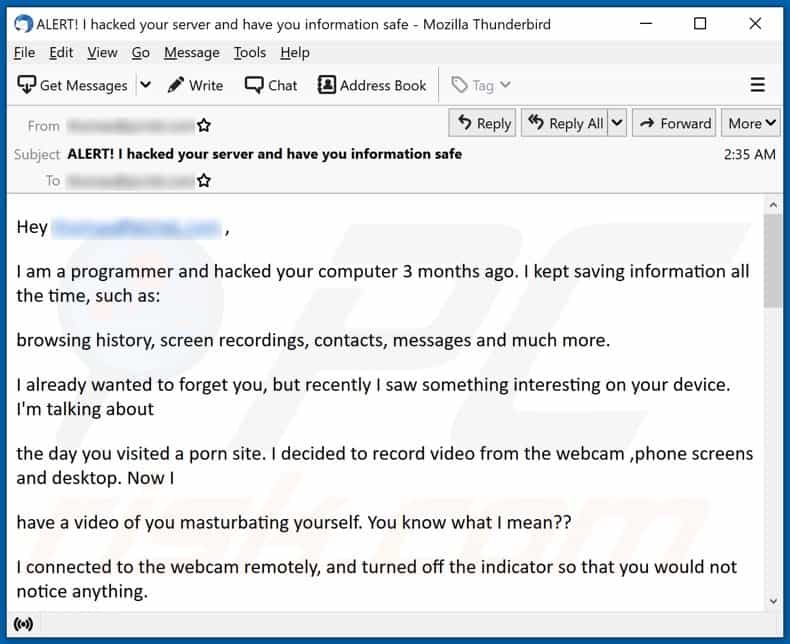
Can scammers hack your computer by calling on the phone?
Scammers Hacking Victims’ Computers by Calling on the Phone. A new scam involves hacking a victim’s computer by calling on the phone. Con artists are using old-fashioned technology to gain access to consumers’ newfangled technology.
Can hackers hijack your computer camera?
Hackers target vulnerable and unpatched computers, stealing sensitive information from the user. You can lose your hard-earned money, your sense of security, and even your privacy. After all, some of these criminals can also hijack your computer’s camera.
What should I do if my computer is being used by hackers?
Besides their getting money from you for doing nothing of any value, if you let them into your computer, who knows what damage they did there or what confidential information they stole. 1. Do a clean reinstallation of Windows.
How can a computer be hacked remotely?
Some malware open access to the device, so the hackers can access it remotely. Or, the malware could be a keylogger, and in this case, even having HTTPS or a VPN will not help. A keylogger will record the keys pressed on the keyboard, and if it happens to be a credit card number, then the hacker will have it.