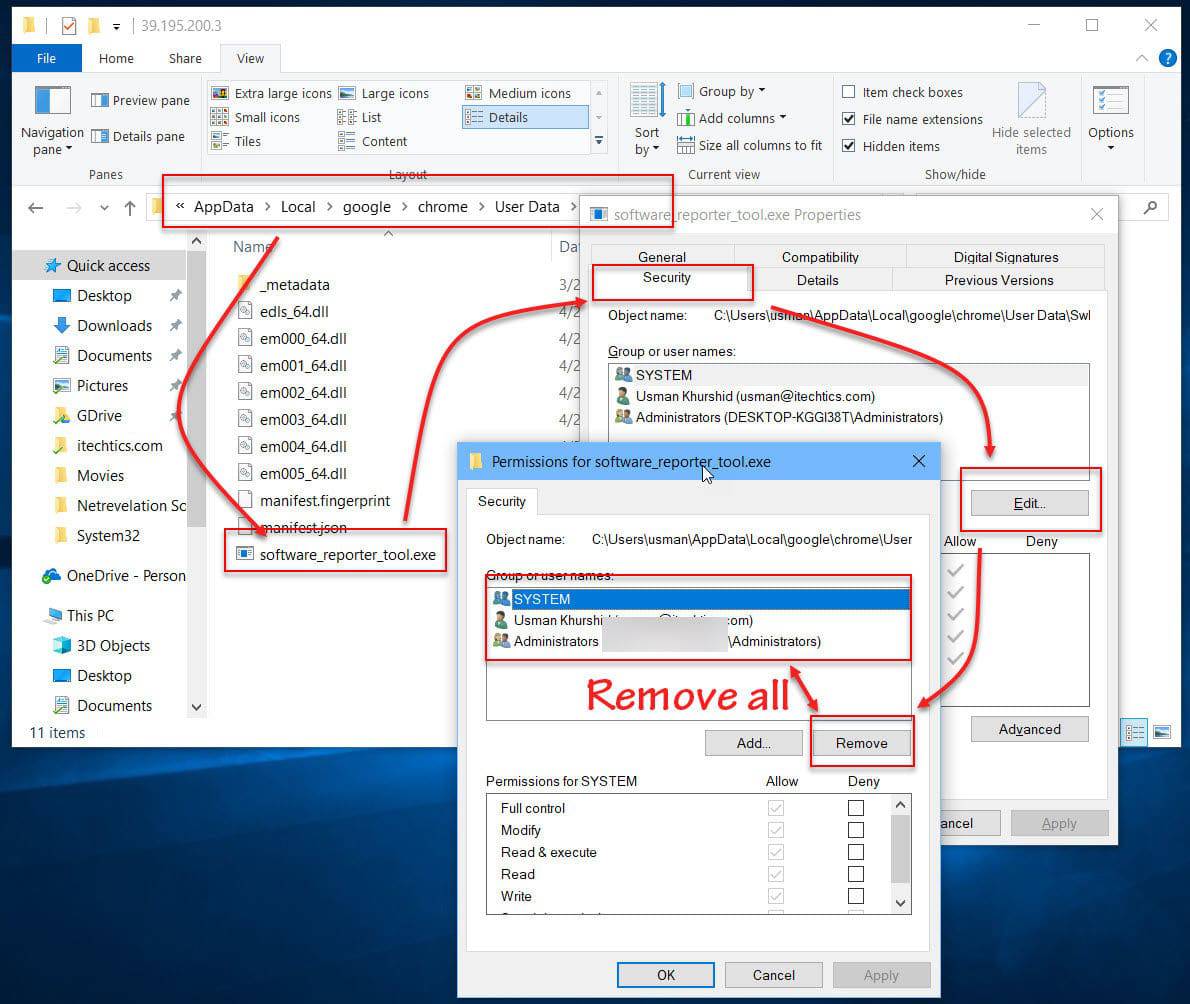
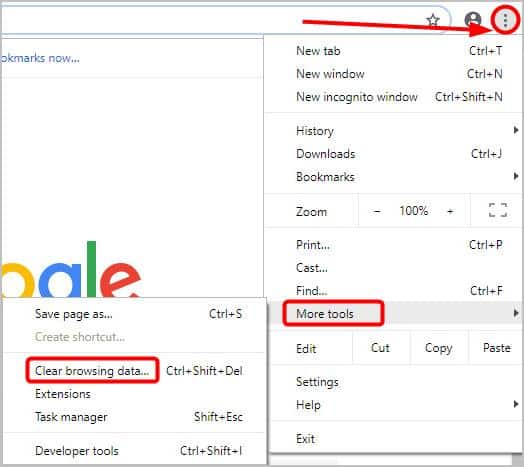
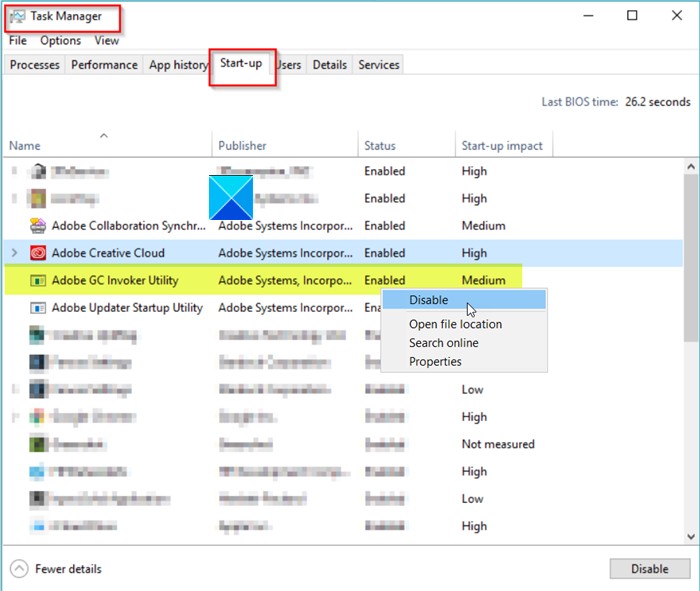
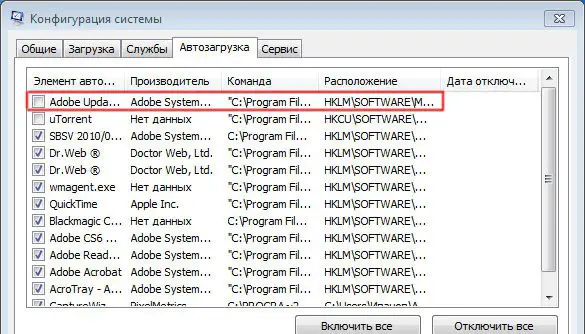
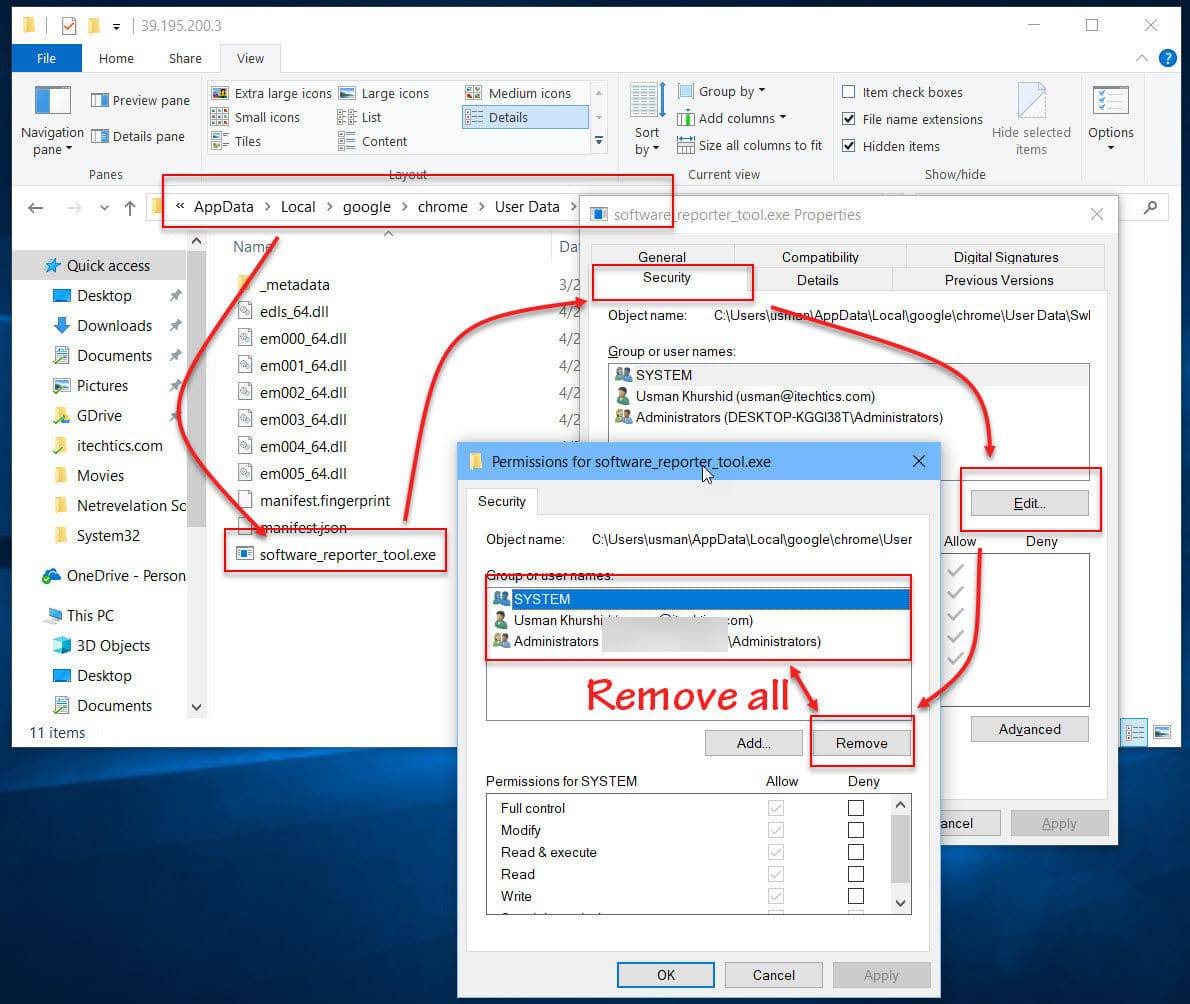
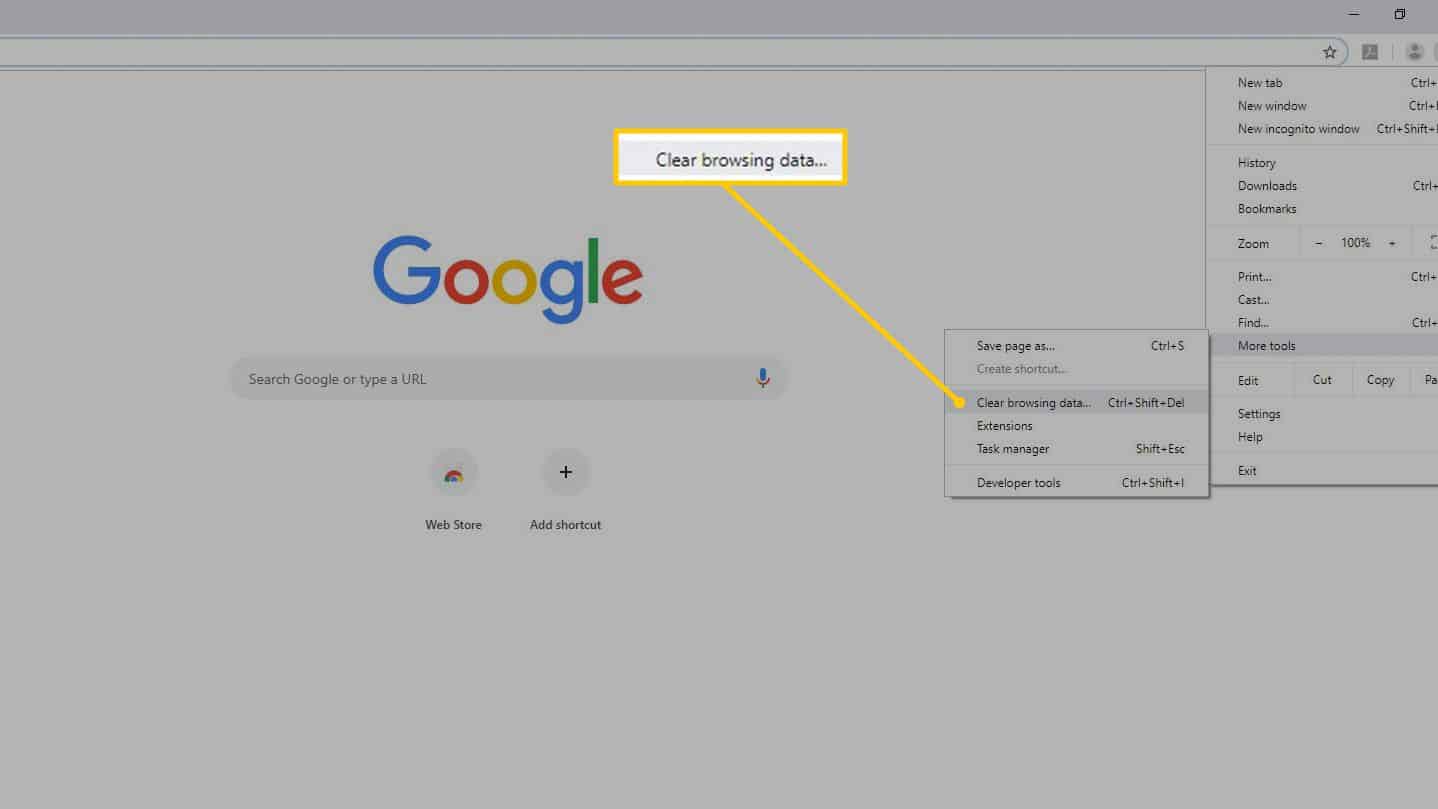
Is it safe to disable the software reporter tool of chrome?
No. Software Reporter Tool is a legitimate application part of Chrome’s Clean-up program. It is a lightweight app that collects data related to third-party programs or add-ons installed on your PC with the Chrome browser. Chrome features a built-in Clean Up tool that can find harmful software on your PC and remove it.Using the Chrome Software Reporter tool isn’t harmful …