If you set an expiration date, on the specified date, AWS KMS deletes the key material from the KMS key, making the KMS key unusable. To use the KMS key in cryptographic operations again, you must reimport the same key material.
How long do KMS keys last?
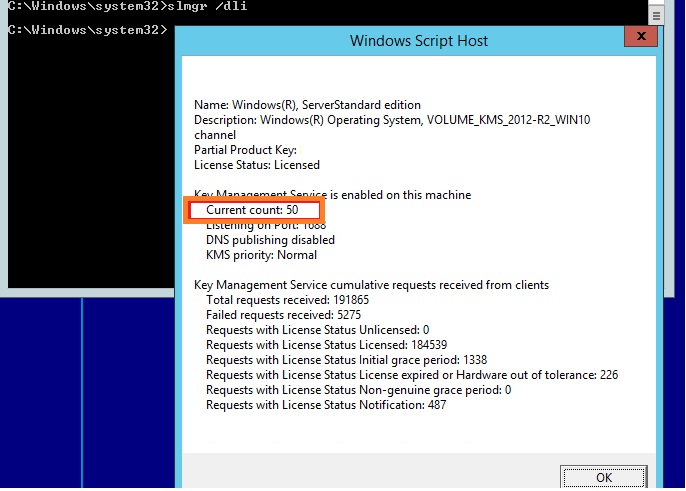
KMS activations are valid for 180 days (the activation validity interval). To remain activated, KMS client computers must renew their activation by connecting to the KMS host at least once every 180 days. By default, KMS client computers attempt to renew their activation every 7 days.
Do AWS KMS keys expire?
Keys generated by AWS KMS do not have an expiration time and cannot be deleted immediately; there is a mandatory 7 to 30 day wait period.
Can KMS keys be deleted?
Deleting an AWS KMS key is destructive and potentially dangerous. It deletes the key material and all metadata associated with the KMS key and is irreversible. After a KMS key is deleted, you can no longer decrypt the data that was encrypted under that KMS key, which means that data becomes unrecoverable.
How often are KMS keys rotated?
AWS KMS automatically rotates AWS managed keys every year (approximately 365 days).
Is KMS activation permanent?
KMS activations are valid for 180 days, a period known as the activation validity interval. KMS clients must renew their activation by connecting to the KMS host at least once every 180 days to stay activated.
How long is KMS activation?
Any Windows client that configured to use ‘KMS Client Channel’ will be activated against the new KMS host automatically within 2 hours (as this is the ‘KMS Activation Interval’ default value).
Can KMS keys be automatically rotated?
Considerations for asymmetric keys Cloud KMS does not support automatic rotation for asymmetric keys, because additional steps are required before you can use the new asymmetric key version.
What is AWS KMS key?
AWS Key Management Service (KMS) is an Amazon Web Services product that allows administrators to create, delete and control keys that encrypt data stored in AWS databases and products.
How often should AWS access keys be rotated?
Access keys give IAM users the ability to connect to Amazon EC2 instances. Therefore rotating these regularly (for example, every 90 days) is one of the key steps in protecting your resources from unauthorized access.
How does Google KMS work?
Cloud KMS lets you import your own cryptographic keys in case you need to use keys that you generate yourself. You can choose to use keys generated by Cloud KMS with other Google Cloud services. Such keys are known as customer-managed encryption keys (CMEK).
How do I remove a KMS alias?
To change the alias of a KMS key, use DeleteAlias to delete the current alias and CreateAlias to create a new alias. To associate an existing alias with a different KMS key, call UpdateAlias .
How do I disable AWS KMS key?
In the navigation pane, choose Customer managed keys. Select the check box for the KMS keys that you want to enable or disable. To enable a KMS key, choose Key actions, Enable. To disable a KMS key, choose Key actions, Disable.
How often should encryption keys be changed?
Encryption keys have a lifetime. Cryptographic key updates for keys that approach the end of their cryptologic period shall be defined by the appropriate application vendor or key owner and based on industry best practices and guidelines, according to PCI DSS Requirement 3.6. 4.
What is a KMS backing key?
This backing key is the fundamental cryptographic element that is used when the encryption process is taking place. During the rotation, older backing keys are retained to decrypt data that was encrypted prior to this rotation.
How frequently should a cryptographic key be changed?
This means that your cryptoperiod is six months, so the key should be rotated twice a year.
How do you check if KMS key is being used?
If you have created a CloudTrail trail in the region where your KMS keyis located, you can examine your CloudTrail log files to view a history of all AWS KMS API activity for a particular KMS key. If you don’t have a trail, you can still view recent events in your CloudTrail event history.
What is the difference between KMS and CloudHSM?
The difference between KMS and CloudHSM is that you control your keys with CloudHSM. CloudHSM gives a single-tenant multi-AZ cluster, and it’s exclusive to you. KMS is multitenant; however, it uses HSMs within, but those are distributed over customer accounts, so it’s not exclusive only for you.
Is KMS key region specific?
AWS managed keys, the KMS keys that AWS services create in your account for you, are always single-Region keys. You cannot convert an existing single-Region key to a multi-Region key.
Where is KMS key used?
A KMS default master key is used by an AWS service such as RDS, EBS, Lambda, Elastic Transcoder, Redshift, SES, SQS, CloudWatch, EFS, S3 or Workspaces when no other key is defined to encrypt a resource for that service. The default key cannot be modified to ensure its availability, durability and security.
Is KMS activator a virus?
Originally Answered: Is KMS Activator is a Virus Program (malware)? No, KMS Auto is not a Virus file but it is simply a activator file. It just activator or unlock the full version of application.
What happens when KMS activation expires?
After each successful connection, the expiration is extended out to the full 180 days. What happens if Windows cannot reactivatethelicense? If a Windows computer has not been able to reestablish communication to the KMS server after 180 days, the machine will become unlicensed.