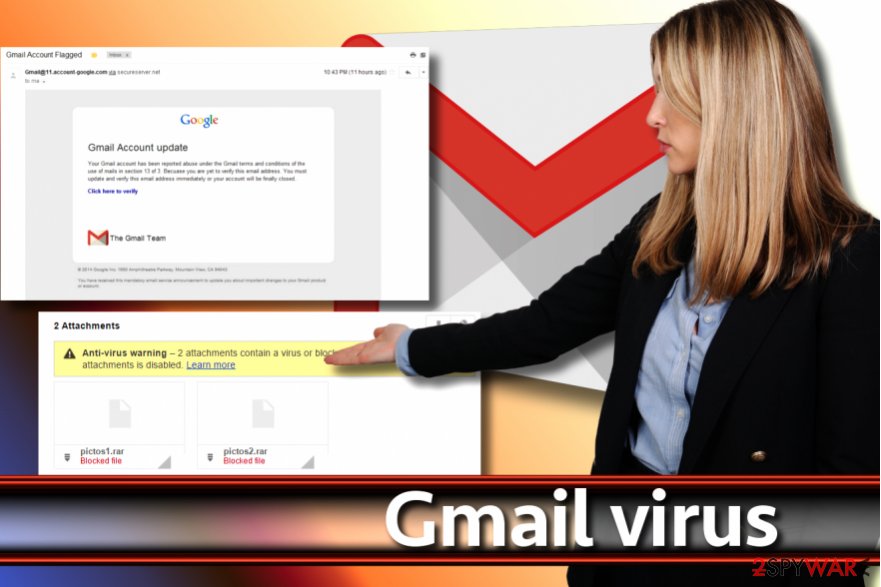
Email attachments can include malicious software that might be missed by traditional antivirus programs. To identify these threats, Gmail can scan or run attachments in a virtual environment called Security Sandbox. Attachments identified as threats are sent to the recipient’s Spam folder.
Does Gmail check for malware?
Google Gmail uses undisclosed virus detection software or a suite of virus detection applications to scan all incoming email. The virus detection process blocks email when it finds a virus or detects a prohibited file type.
How secure is Gmail from viruses?
Gmail’s default settings provide fairly robust security. The data that users see can see in Gmail are actually encrypted with the industry-standard 128 bit encryption. Google transmits Gmail data to its users via transport layer security 1.1, also an industry standard.
Does Gmail check for malware?
Google Gmail uses undisclosed virus detection software or a suite of virus detection applications to scan all incoming email. The virus detection process blocks email when it finds a virus or detects a prohibited file type.
How do I turn off Gmail virus scan?
1] Disable the Virus Scan feature in Chrome Click on the Advanced button to navigate to the Privacy and security section. Select the option for Sync and Google services. Toggle the option for Safe Browsing to be off. Restart your browser and your issue should be resolved.
Is Gmail safer than Outlook?
Gmail is much more secure out of the box Both Gmail and Outlook both offer more or less the same security features: multi-factor authentication, encryption in transit, spam, phishing, and malware detection.
What is the safest email service?
ProtonMail ProtonMail is the most well-known secure email provider. It’s open source, based in Switzerland, and provides end-to-end asymmetric encryption.
Does Gmail check for malware?
Google Gmail uses undisclosed virus detection software or a suite of virus detection applications to scan all incoming email. The virus detection process blocks email when it finds a virus or detects a prohibited file type.
Are the Google virus warnings real?
Google Security Alert/Warning is a fake alert issued by malicious websites. Like all social engineering, it’s designed to trick users into making an unsafe decision online. Chrome and Android devices have security alerts, but they aren’t labeled “Google Security Alert”.
Can a virus be sent through email?
Email viruses often spread by causing the malicious message to be sent to everyone in the original victim’s address book. Simply put, an email virus is a malicious code or a link to malicious code sent via email. The virus has the ability to replicate itself so it can quickly spread from one device to another.
How do you ignore a virus detection?
Go to Start > Settings > Update & Security > Windows Security > Virus & threat protection. Under Virus & threat protection settings, select Manage settings, and then under Exclusions, select Add or remove exclusions. Select Add an exclusion, and then select from files, folders, file types, or process.
How do I enable Google antivirus?
Go to Google Chrome’s settings by clicking the More button (the vertical ellipsis in the top right corner of the window). Click More Tools. Select Extensions in the menu that appears. Choose the antivirus browser extension.
Why do companies use Outlook instead of Gmail?
Outlook provides multiple ways to track down what users are looking for, whether its search, folders, categories, sort emails in inbox, search folders, etc. With Gmail, users do not have a way to sort email by size, date or sender and are stuck with just one thing – search!
Should I use Gmail or Outlook?
If you want a streamlined email experience, with a clean interface, then Gmail is the right choice for you. If you want a feature-rich email client that has a bit more of a learning curve, but has more options to make your email work for you, then Outlook is the way to go.
Is Hotmail safer than Gmail?
Gmail is less secure since it analyzes users’ emails to send ads. Hotmail can be considered more secure, as users’ emails are not scanned to send ads. Encryption Protocol: SSL and TLS are both supported as encryption protocols in Gmail.
Is Gmail safe for banking?
If you are wondering whether your Gmail account is secure from hackers, then the answer is yes, but only to a certain extent. Gmail is encrypted with TLS, Transport Layer Security, while transferring your data and it protects your emails at rest with industry-standard 128-bit encryption.
Is Gmail safe to use?
Your information is protected by world-class security, monitoring things like suspicious logins and unauthorized activity. You can always control your privacy settings in your Google Account. For general information about privacy on Gmail, keep reading this article.
Should you delete phishing emails?
If you receive any unwanted email, the best approach in almost every case is to delete it immediately. It is often clear from the Subject line that a message is junk, so you may not even need to open the message to read it.
What type of emails can contain malware?
Types of email viruses. Email viruses can take many different forms: Email spam. Email spam, also known as unwanted or unsolicited email, usually spreads malware through links in the message.
Can a virus be sent through email?
Email viruses contain malicious code sent through email messages. People can get an email virus by clicking on a link or opening an attachment infected with the virus. Email is the main entry for bad actors to get into an organization and cause a data breach.
Should I delete my email if it was hacked?
If you have been hacked several times and your email provider isn’t mitigating the amount of spam you are receiving, then consider starting afresh but don’t delete your email address! Many experts do warn against deleting email accounts as most email providers will recycle your old email address.
Can I check if my email has been hacked?
Keep an eye on your email address Enter your email address, and HaveIBeenPwned will check to see if it’s been compromised in a data breach. If it has, you’ll see a list of sites that have exposed your data and what exactly was leaked.