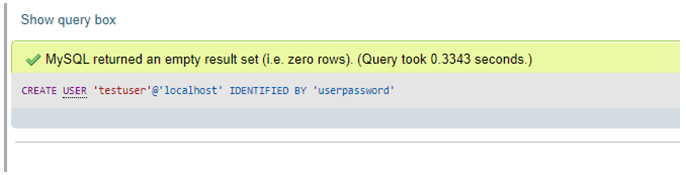
In MySQL, the user permissions are granted to the MySQL user account which determines operations that can be performed in the server. These user permissions may differ in the levels of privileges in which they are applied for several query executions.
How is user security implemented in MySQL?
MySQL security works by limiting both the users who have access to a database and what they are allowed to do once they have access.
How do I show user permissions in MySQL?
If the user account you are logged in as has SELECT privileges on the internal mysql database, you can see the privileges granted to other user accounts. To show the privileges of other accounts, use the following format: SHOW GRANTS FOR ‘
How are permissions implemented in MySQL Mcq?
Explanation: MySQL uses security based on Access Control Lists (ACLs) for all connections, queries and other operations that users can attempt to perform. There is support for SSL encrypted connections. 2. The mysql client writes a record of executed statements to a history file on Unix.
How do I change permissions in MySQL?
You can’t currently change a user’s privileges in the control panel, so to do so you need to use a command-line MySQL client like mysql . After you create a user in the cluster, connect to the cluster as doadmin or another admin user.
How do I grant grants in MySQL?
The WITH GRANT OPTION clause gives the user the ability to give to other users any privileges the user has at the specified privilege level. To grant the GRANT OPTION privilege to an account without otherwise changing its privileges, do this: GRANT USAGE ON *.
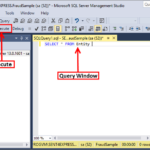
How do I give permission to database in SQL Server?
Security – Logins, then double click on Login and you’ll get Login Properties window. Go to User Mapping Tab and select the database on which you want to give permission. Under ‘Database role membership for’ section, check ‘db_datawriter’ checkbox as shown below. Click Ok and you’re done.
Which of the following is available in MySQL Mcq?
The correct answer to the question “Which of the following is available in MySQL” is option (D). Create Database. Because MySQL is an open-sourced RDBMS or Relational Database Management System.
How do you grant permission to access a database?
On the Database Tools tab, in the Administer group, click Users and Permissions. Click one of the following commands: User and Group Permissions Use this to grant or revoke user or group permissions, or to change the owner of database objects.
How do I grant permission to select a user in SQL Server?
1 Answer. For the existing view, you can go to the Properties of the view in SSMS, add users in the Permissions, and then grant select permission in the permissions list. Or use the following statement to grant user permissions: GRANT SELECT ON OBJECT::[schema].
What are the three ways of implementing a security control?
There are three primary areas or classifications of security controls. These include management security, operational security, and physical security controls.
What are three types of security policies?
A: Three types of security policies in common use are program policies, issue-specific policies, and system-specific policies.
Why do we implement security policies?
Why are security policies important? Security policies are important because they protect an organizations’ assets, both physical and digital. They identify all company assets and all threats to those assets.
What is the purpose of implementing a security policy?
The aim of IT security policies is to address security threats and implement strategies to mitigate IT security vulnerabilities, as well as defining how to recover when a network intrusion occurs. Furthermore, the policies provide guidelines to employees on what to do and what not to do.
What are the four 4 elements of data security?
Protection, Detection, Verification & Reaction. These are the essential principles for effective security on any site, whether it’s a small independent business with a single site, or a large multinational corporation with hundreds of locations.
What are the two 2 types of user privileges?
System privileges—A system privilege gives a user the ability to perform a particular action, or to perform an action on any schema objects of a particular type. Object privileges—An objectprivilege gives a user the ability to perform a particular action on a specific schema object.
What are the two types of privileges?
Administrator privileges control creation of objects and system administration. Object privileges control access to specific database objects.
What is process privilege in MySQL?
The PROCESS privilege controls access to information about threads executing within the server (that is, information about statements being executed by sessions). Thread information available using the SHOW PROCESSLIST statement, the mysqladmin processlist command, the INFORMATION_SCHEMA.
How do I change permissions on a database?
Right-click the database server and click Permissions. Choose the user from the list. Check the Server administrator check box to grant the user server administrator privileges. Uncheck the Server administrator check box to revoke the user server administrator privileges.
What is chmod 777 and chmod 775 and chmod 755?
777 – all can read/write/execute (full access). 755 – owner can read/write/execute, group/others can read/execute. 644 – owner can read/write, group/others can read only.
How do I give a user a grant in MySQL?
To accommodate granting rights to users from arbitrary hosts, MySQL supports specifying the user value in the form ‘ user_name ‘@’ host_name ‘ . You can specify wildcards in the host name. For example, ‘ user_name ‘@’%. example.com’ applies to user_name for any host in the example.com domain, and ‘ user_name ‘@’198.51.
What are permissions in database?
Permissions are the types of access granted to specific securables. At the server level, permissions are assigned to SQL Server logins and server roles. At the database level, they are assigned to database users and database roles.