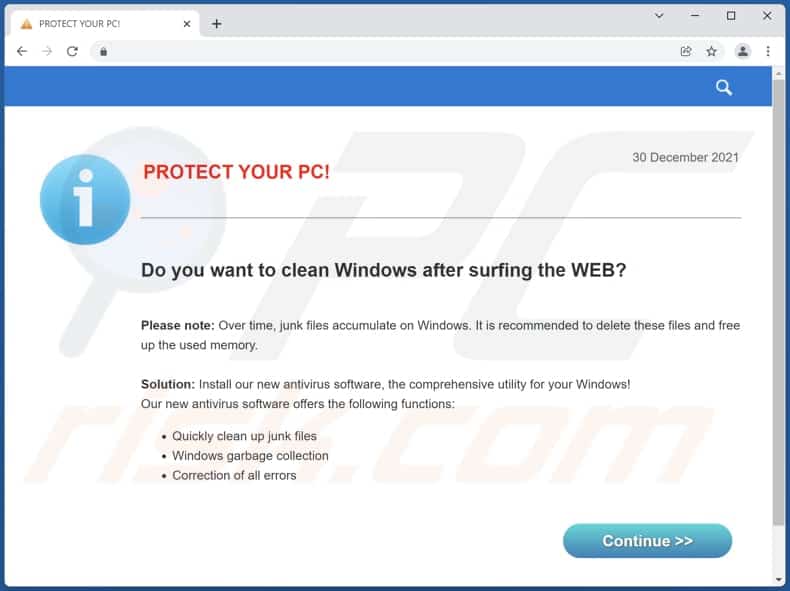
In a remote access scam, a scammer attempts to persuade you into giving them remote control over your personal computer, which allows the scammer to con money out of you and steal your private information.
Can scammer access my computer remotely?
In a remote access scam, a scammer attempts to persuade you into giving them remote control over your personal computer, which allows the scammer to con money out of you and steal your private information.
Can scammer access my computer remotely?
In a remote access scam, a scammer attempts to persuade you into giving them remote control over your personal computer, which allows the scammer to con money out of you and steal your private information.
Can someone remotely access my computer without my knowledge?
There are two ways someone can access your computer without your consent. Either a family member or work college is physically logging in to your computer or phone when you are not around, or someone is accessing your computer remotely.
Can a hacker take control of my computer?
Your computer can be used to attack other computers. Sometimes hackers will take over a computer, sometimes thousands of them, to launch an attack on a website they’ve targeted.
How can you identify a scammer?
you don’t know contacts you out of the blue. you’ve never met in person asks for money. asks you to pay for something or to give them money through unusual payment methods such as gift cards, wire transfers or cryptocurrencies. asks you to pay for something in advance — especially through an unusual payment method.
What happens if a scammer has your email?
What will scammers do with your email address? Once a scammer gets your email address, they’ll use it to benefit themselves in any way possible. Many will send you spam email, with the hope of collecting private information such as credit card numbers.
What do I do if I give my personal information to a scammer?
Notify the Federal Trade Commission (FTC) that you have been phished. The FTC is the nation’s consumer protection agency. The FTC’s Bureau of Consumer Protection works for the consumer to prevent fraud, deception and unfair business practices in the marketplace.
What can you do if you get scammed online?
Report a scam that happened with an online seller or a payment transfer system to the company’s fraud department. If you used your credit card or bank account to pay a scammer, report it to the card issuer or bank. Also report scams to the major credit reporting agencies.
Can a scammer use TeamViewer?
Stay safe! Unfortunately, there have been some instances of malicious use of our software, “TeamViewer”. Scammers attempt to sell their services via phone by claiming that your device is infected by malware. TeamViewer Germany GmbH is a legitimate software development company.
What can a scammer do with AnyDesk?
AnyDesk is used legitimately by millions of IT professionals worldwide, to remotely connect to their clients’ devices to help with technical issues. However, scammers can try to misuse AnyDesk (or any other remote access software) to connect to your computer and steal data, access codes, and even money.
Can someone take over your phone remotely?
remotely. Skilled hackers can take over a hacked smartphone and do everything from making overseas phone calls, sending texts, and using your phone’s browser to shop on the Internet. Since they’re not paying your smartphone bill, they don’t care about exceeding your data limits.
Can scammer access my computer remotely?
In a remote access scam, a scammer attempts to persuade you into giving them remote control over your personal computer, which allows the scammer to con money out of you and steal your private information.
Does shutting down computer stop hackers?
In general, the answer is no, you cannot hack into a computer that’s been turned off. Unless two conditions are met, the PC cannot be restarted and hacked from outside, even if you leave it connected to the internet and to power.
How do u know if your computer has been hacked?
Frequent pop-up windows, especially the ones that encourage you to visit unusual sites, or download antivirus or other software. Changes to your home page. Mass emails being sent from your email account. Frequent crashes or unusually slow computer performance.
Can scammer be caught?
What can a scammer do with my picture?
Information fraudsters could get from your photos A photo posted on your birthday, for example, would provide them with your date of birth, whereas a photo of a new house could potentially give them details of where you live.
What makes someone a scammer?
Other scammers, Plante says, have antisocial tendencies, like sociopathy, that drive their behavior. In this case, scammers believe that not only do societal rules not apply to them, they also have no empathy for other people. “They feel like if folks are cheated, then it’s their own fault.
What happens if you call back a spam number?
“It’s a telephone scam technique where your phone rings once and then stops, in hopes that you will call the number back. If you do call back, it goes to a high-cost international number, meaning you will be charged for that call, and the scammer will make money.”
Can someone hack my bank account with my email address?
It’s also possible hackers could use your email account to gain access to your bank account or credit card information, draining funds from an account, or racking up charges. They might even use your email and password to sign up for online sites and services, sticking you with monthly fees in the process.
What is the first thing you do when you get hacked?
Step 1: Change your passwords This is important because hackers are looking for any point of entry into a larger network, and may gain access through a weak password. On accounts or devices that contain sensitive information, make sure your password is strong, unique—and not easily guessable.
What information does a scammer need?
Scammers can steal your identity by obtaining your personal financial information online, at the door or over the phone. What they want are account numbers, passwords, Social Security numbers, and other confidential information that they can use to loot your checking account or run up bills on your credit cards.