Memory integrity is a feature of core isolation. By turning on the Memory integrity setting, you can help prevent malicious code from accessing high-security processes in the event of an attack.
Should memory integrity be on or off?
Memory integrity is a feature of core isolation. By turning on the Memory integrity setting, you can help prevent malicious code from accessing high-security processes in the event of an attack.
What do you use to protect your computer answer?
Use an anti-malware app – Installing an anti-malware app and keeping it up to date can help defend your PC against viruses and other malware (malicious software). Microsoft Defender is free anti-malware software included with Windows, and it’s kept updated automatically through Windows Update.
How do hackers get into your computer?
Computer systems can be hacked in various ways, including via viruses and other malware. So if you visit compromised websites or use unsecured Wi-Fi networks, especially without strong antivirus protection, the risk that you may be hacked can increase markedly.
Is memory protection necessary?
Need of Memory protection: Memory protection prevents a process from accessing unallocated memory in OS as it stops the software from seizing control of an excessive amount of memory and may cause damage that will impact other software which is currently being used or may create a loss of saved data.
Why is memory protection needed?
The main purpose of memory protection is to prevent a process from accessing memory that has not been allocated to it. This prevents a bug or malware within a process from affecting other processes, or the operating system itself.
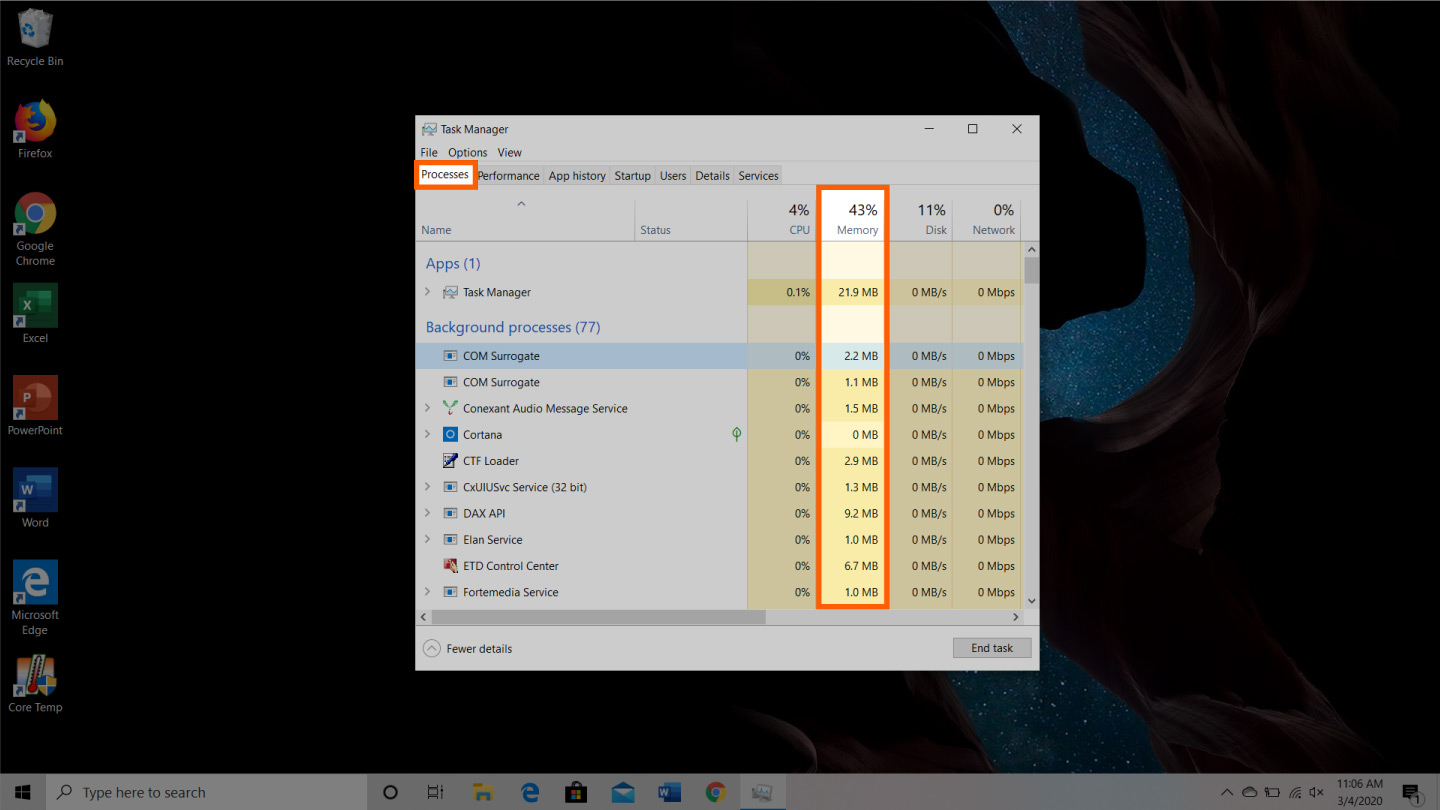
What happens when memory usage is high?
If the computer has high memory usages problem, it will freeze (especially when a large program like a game is running). Sometimes, it will result in “Your computer is low on memory” error popping up. In addition, computer users can also evaluate high memory usage Windows 10 on Task Manager.
What is meant by memory integrity is off?
Core Isolation Memory Integrity should be on in Windows 10 & 11 by default, and you want it enabled if possible. However, if it is disabled and you can’t enable it, that means you have an incompatible driver. You should see a list of any incompatible drivers in this situation.
Why is my memory integrity turned off?
Core isolation – Memory integrity issues are pretty common in Windows, unfortunately. These problems often occur due to incompatibility issues or when drivers are affected, outdated, damaged, and conflicts with the needed processes on the machine.
Should I enable or disable memory compression?
Now you know what memory compression is, why it is important, and how you can enable and, if you need to, disable it. However, we advise against disabling memory compression since it gives your RAM more room to play. It helps you avoid a majority of the problems that you can encounter when your physical memory is full.
Can you tell if someone has hacked your computer?
Signs that you’ve been hacked include degradation of system performance, odd cursor, and text and the appearance of software you didn’t install. It is possible to prevent most hacking by using complex passwords, installing anti-virus software, and keeping current on your operating system software. Awareness is crucial.
What is the first thing you do when you get hacked?
Step 1: Change your passwords This is important because hackers are looking for any point of entry into a larger network, and may gain access through a weak password. On accounts or devices that contain sensitive information, make sure your password is strong, unique—and not easily guessable.
Can someone hack your computer if it’s off?
However, you would be glad to know that the general answer to this question is “no.” If your computer is turned off, it cannot be booted and hacked even if you leave it connected to the power source and the Internet.
Which antivirus is free forever?
Best Free Antivirus for: Windows: Avira. Mac: Avira. Android: Bitdefender.
Which antivirus is completely free?
Avast Free Antivirus really is free — you’ll never need to pay for it and it’ll provide you with essential online security and protection. If you’re looking for more security and privacy features, our Avast Premium Security software is the right product for you.
What is a really good free antivirus?
Free antiviruses like Bitdefender, Avira, and TotalAV are pretty good, and they can offer some decent protection. But free antivirus software doesn’t come with all of the extra features needed for complete online protection — features that are only offered by premium antiviruses.
What are three hazards with using a computer?
Summary. Working at a computer can cause back, neck and shoulder pains, headache, eyestrain and overuse injuries of the arms and hands.
Does Windows have memory protection?
In addition, Windows provides memory protection by using the virtual memory hardware. The implementation of this protection varies with the processor, for example, code pages in the address space of a process can be marked read-only and protected from modification by user-mode threads.
What is CPU and memory protection?
A memory protection unit (MPU), is a computer hardware unit that provides memory protection. It is usually implemented as part of the central processing unit (CPU). MPU is a trimmed down version of memory management unit (MMU) providing only memory protection support.
What is protection storage?
What is storage protection? Security on z/OS. Mainframe hardware has a storage protection function, which is normally used to prevent unauthorized alteration of storage. Storage protection is also used to prevent unauthorized reading of storage areas, although z/OS® protects only small areas of storage this way.
How is memory protection achieved in protected mode?
There are also other memory protection mechanisms that can be used in protected mode. When the computer is powered on, it starts in real mode but only to initiate the operating system, which sets up the protected mode by enabling the Protection Enabled PE bit in the control register CR0 [1].
What is strategic memory protection?
In this article, we focus on individuals’ desire to engage in what we call strategic memory protection, that is, behaviors that people think will allow them to protect their ability to remember those experiences that they want to look back on later.