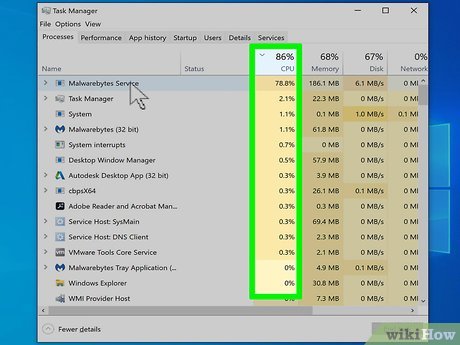
You can use the Windows Task Manager on your computer to assess whether any programs have been opened on your computer without your knowledge. If you see programs in use that you did not execute, this is a strong indication that remote access has occurred.
Can you tell if someone is remotely accessing your computer?
You can use the Windows Task Manager on your computer to assess whether any programs have been opened on your computer without your knowledge. If you see programs in use that you did not execute, this is a strong indication that remote access has occurred.
How do I know if someone is using TeamViewer on my computer?
Best Answer Just click in your TeamViewer on Extras –> Open Logfiles. In the same folder, there should be a file called connections_incoming. txt. In this file, you find the information you are looking for.
Can someone remotely access my computer without Internet?
Can an Offline Computer be Hacked? Technically — as of right now — the answer is no. If you never connect your computer, you are 100 percent safe from hackers on the internet. There is no way someone can hack and retrieve, alter or monitor information without physical access.
Can someone see you through your computer screen?
Someone could be watching you through your webcam, without you even realising. We don’t mean to unduly alarm you, but unsecured cameras on your computer could provide a malicious hacker with a direct window into your life.
Can someone listen to you through your computer?
Anything you do on your work computer can be monitored or recorded by your employer. This includes the websites you browse, things you write in personal emails or chat, or when you use a work phone or Skype-type service to make a personal call.
Can someone use TeamViewer to access my computer without me knowing?
In general, it is only possible to access your computer if you share your TeamViewer ID and the associated password with another person. Without knowing the ID and password, it is not possible for others to access your computer.
Can TeamViewer be detected?
You can detect TeamViewer usage by collecting traffic logs (e.g. from the Firewall). Once the logs are collected, you can use for the TeamViewer port (5983), or for TCP/443 requests to IPs with PTR records resolving to *.
Does turning off computer stop remote access?
Exception to the Rule: Allowing Remote Access Generally speaking, hacking a turned-off computer is not possible in a home environment. However, it may happen in shared networks such as an office environment. There are features that allow you to remotely turn on and boot a computer.
What prevents someone from connecting to your computer remotely using your public IP?
If the firewall port is exposed to the public, it will allow any IP address to connect to it. Anyone located from different parts of the world can try to brute force their way into your computer. The computer can be infected with malware, ransomware, or data theft.
Can you tell if someone is remotely accessing your computer?
You can use the Windows Task Manager on your computer to assess whether any programs have been opened on your computer without your knowledge. If you see programs in use that you did not execute, this is a strong indication that remote access has occurred.
How do I know if my IP is being tracked?
The Netstat command works best when you have as few applications opened as possible, preferably just one Internet browser. The Netstat generates a list of Internet Protocol (IP) addresses that your computer is sending information to.
Can my boss watch me on camera all day?
Conclusion: Your Boss Can Legally Monitor Any Activity on a Work Computer or A Work Network. As you now know, your boss can monitor almost anything you do during the day – whether you’re working remotely or have returned to the office.
Can your company spy on your computer camera?
Employers can legally monitor almost anything an employee does at work as long as the reason for monitoring is important enough to the business. Employers may install video cameras, read postal mail and e-mail, monitor phone and computer usage, use GPS tracking, and more.
How would you know if your computer has been hacked?
Frequent pop-up windows, especially the ones that encourage you to visit unusual sites, or download antivirus or other software. Changes to your home page. Mass emails being sent from your email account. Frequent crashes or unusually slow computer performance.
What is one way hackers can trick you into transmitting?
What is one way hackers can trick you into transmitting personal data over on a public network without your knowledge? They disguise the network as an evil twin.
Can Wi-Fi be hacked remotely?
Yes, it’s absolutely possible for your home network to get hacked. There are a couple of ways hackers can gain access to your network. One common method is to guess the password. It sounds simple, but routers often come with a preset default password that the manufacturer uses for all devices.
Why should you cover your laptop camera?
Cybercriminals can access these cameras, and because of their positions — facing your living room, kitchen, or office — they can expose your privacy and sensitive conversations. That’s why it’s a good idea to cover up your webcam or take other steps to improve your internet security.
Should you cover your phone camera?
Most of the products come in multiple packs and cost a few dollars. While covering a smartphone camera could help mitigate a threat, Yalon cautions that no one should ever feel truly secure. “The microphone and tracking abilities, as we demonstrated in our new research, contain yet another set of concerns,” he says.
Should you put tape over your laptop camera?
Many security experts recommend camera covers as a first step to promote your cybersecurity. Because protection is as simple as placing a Post-It note or electrical tape over your camera, taking the extra precaution is a no brainer.
Can a computer be used as a listening device?
Yes, it is true! You can hack any laptop device using its operating system and take over the microphone and use it to listen to the conversations and record surrounds information secretly.
What do I dial to see if my phone has been hacked?
Use the code *#21# to see if hackers track your phone with malicious intent. You can also use this code to verify if your calls, messages, or other data are being diverted. It also shows your diverted information’s status and the number to which the information is transferred.prieš 4 dienas