The use of Node. js is an unusual choice for malware authors writing commodity malware, as it is primarily designed for web server development, and would not be pre-installed on machines likely to be targeted. However, the use of an uncommon platform may have helped evade detection by antivirus software.
Should I uninstall node JS?
Once you install nvm and use Node through it, it does NOT use bin/node , but the version installed with nvm , so your old Node is obsolete. The main reason they recommend you to uninstall Node is because it could confuse the shell about which Node to use.
Can I delete node exe?
If you have installed Node. js, you need to uninstall it to remove the node.exe process permanently.
Where is node JS installed on Windows?
The prefix config defaults to the location where node is installed. On most systems, this is /usr/local . On windows, this is the exact location of the node.exe binary.
How do I completely uninstall npm?
To remove a package with the npm uninstall command, you can use the syntax npm uninstall package-name in the directory where the package is located. The package I will be using to demonstrate how a package is uninstalled is Express – a NodeJS framework.
How do I uninstall Node using NVM?
NVM allows you to uninstall Node versions that are no longer required. Run the command nvm uninstall with the version of Node you’d like to remove. You cannot remove a version you are currently using, so you must switch to a different version first. NVM confirms the Node version has been removed.
What is Spoolsv exe?
spoolsv.exe runs the Windows OS print spooler service. Any time you print something with Windows this important service caches the print job into memory so your printer can understand what to print. If the print spooler is running you can usually see it in the bottom right Windows notification area.
What is MoUSOCoreWorker exe?
MoUSO Core Worker Process — also known as MoUSOCoreWorker.exe — is a file from Microsoft which is related to Windows Update. It is a Microsoft task that helps coordinate the installation of Windows updates within the operating system.
Is dasHost exe safe?
The true dasHost.exe file is a safe Microsoft Windows system process, called “Device Association Framework Provider Host”. However, writers of malware programs, such as viruses, worms, and Trojans deliberately give their processes the same file name to escape detection.
Do I need Svchost exe?
Windows uses svchost.exe files to launch the DLLs (dynamic-link libraries) that help Windows processes run efficiently. DLLs offer flexibility from a programming perspective, since they can be individually altered without an entire program needing to be updated.
What is SvcHost exe doing?
The Service Host (svchost.exe) is a shared-service process that serves as a shell for loading services from DLL files. Services are organized into related host groups, and each group runs inside a different instance of the Service Host process. In this way, a problem in one instance doesn’t affect other instances.
Does npm come with node?
NPM is included with Node. js installation. After you install Node. js, verify NPM installation by writing the following command in terminal or command prompt.
How do I check if node is installed Windows?
To see if Node is installed, open the Windows Command Prompt, Powershell or a similar command line tool, and type node -v . This should print the version number so you’ll see something like this v0. 10.35 .
Do I need to uninstall node before installing NVM?
You can use it to install multiple versions of node, and then you can easily switch the currently used node version with one line of command. In other words, you don’t need to uninstall and install anymore, just use nvm to install which version you want to use, and just switch with one instruction after installation!
Is Node.js a programming language?
Node. js is not a programming language. Rather, it’s a runtime environment that’s used to run JavaScript outside the browser.
What is the latest version of node?
Is Node.js a framework?
js is actually not a framework or a library, but a runtime environment, based on Chrome’s V8 JavaScript engine.
What npm install does?
The npm install installs all modules that are listed on package. json file and their dependencies. npm update updates all packages in the node_modules directory and their dependencies.
What is npm clean install?
The npm clean-install command (or npm ci for short) is an in-place replacement for npm install with two major differences: It does a clean install: if the node_modules folder exists, npm deletes it and installs a fresh one. It checks for consistency: if package-lock.
Can I delete npm cache?
Run: “npm cache clean –force” are both not working and you still can’t clear the cache, you can force clear the cache by running: npm cache clean –force or npm cache clean -f . This will force delete the npm cache on your computer.
Does npm cache packages?
npm stores cache data in an opaque directory within the configured cache , named _cacache . This directory is a cacache -based content-addressable cache that stores all http request data as well as other package-related data.
What does npm cache clean do?
clean: Delete all data out of the cache folder. Note that this is typically unnecessary, as npm’s cache is self-healing and resistant to data corruption issues. verify: Verify the contents of the cache folder, garbage collecting any unneeded data, and verifying the integrity of the cache index and all cached data.
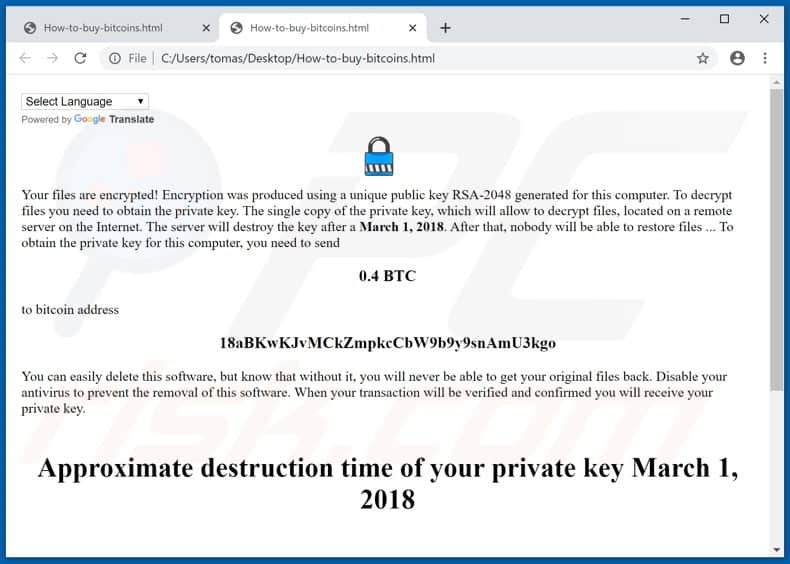
What is Node JS encryption malware?
Discovered by Xavier Mertens, Node.js is a ransomware-type malicious software. This malware encrypts the data of infected devices and demands payment for decryption. When Node.js encrypts, files are appended with the “.encrypted ” extension.
What is Node JS proxies malware?
Thousands of Windows computers across the world have been infected with a new strain of malware that downloads and installs a copy of the Node.js framework to convert infected systems into proxies and perform click-fraud.
What is nodersok malware?
New Nodersok malware installs Node.js to turn systems into proxies, perform click-fraud. Thousands of Windows computers across the world have been infected with a new strain of malware that downloads and installs a copy of the Node.js framework to convert infected systems into proxies and perform click-fraud.
What is a node antivirus and how does it work?
Personal laptops can use an antivirus program to keep their files protected from malware, and smartphones can use a similar antimalware app to catch viruses and other threats before they cause any harm. “Node” also describes a computer file in a tree data structure.