Instead, Opera VPN is more of a secure proxy service that spoofs your location by hiding your IP address. Opera VPN is better than most proxies because it actually encrypts your data, but it won’t offer the comprehensive privacy and protection that a full VPN provides.
Is Opera VPN anonymous?
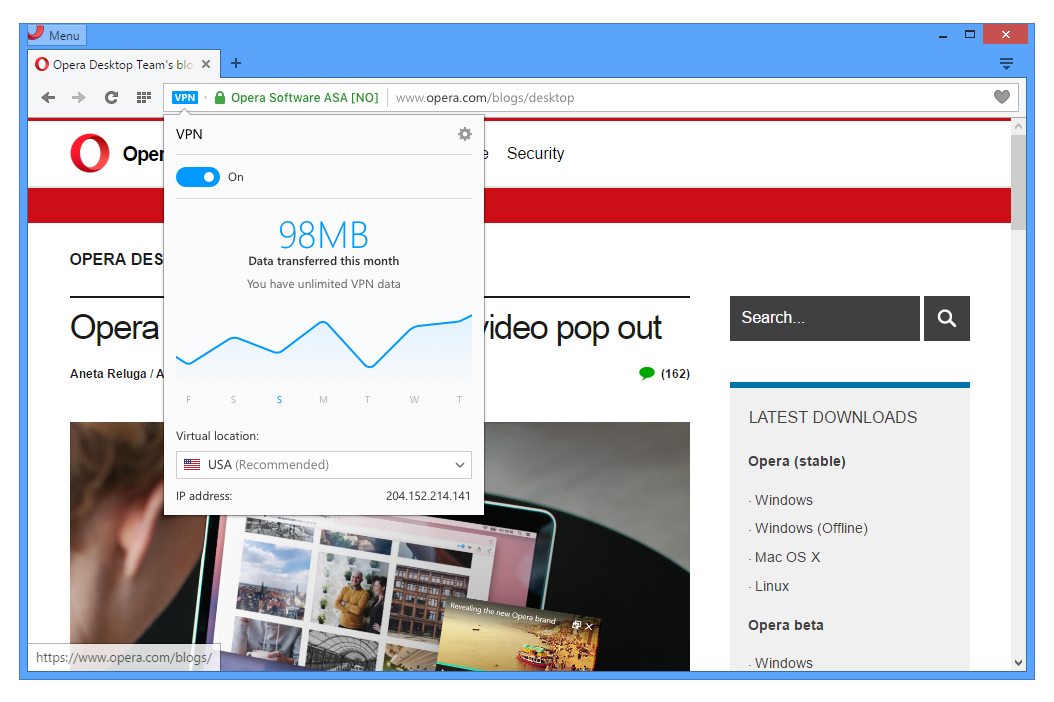
Protect your privacy with Opera’s Free VPN service Virtual Private Networks protect your privacy and online activity from third parties with an encrypted connection for your internet traffic.
Is Opera actually private?
Chrome and Opera both have their own private browsing modes. The private browsing window doesn’t keep Google, Opera or websites from collecting your personal information, but it’s still useful for keeping personal data off your device.
Can your internet provider see your history with Opera VPN?
VPNs encrypt all internet traffic, effectively hiding your browsing history from your ISP. However, that doesn’t mean the ISP is blind to your activities. They may be able to tell that you’re connected to a VPN and for how long, based on the fact that the encrypted traffic is headed to an IP address of a VPN server.
Can Opera VPN be trusted?
Our Verdict. Opera VPN is not a safe or secure service to use. It doesn’t use a tunneling protocol, its logging policy is overly invasive, and it isn’t strictly a real VPN. We don’t recommend you use Opera VPN to protect yourself online.
Is Opera good for privacy?
Connecting to webpages through Opera’s VPN (virtual private network) means that the data sent back and forth is encrypted and routed through a remote server. The encryption helps secure your data from prying eyes, while the remote server disguises your IP address and location for more privacy.
Is Opera owned by China?
Does Opera sell your data?
Opera says it does not collect any user data, though the company encourages consumers to send some information about their feature usage to improve the product.
Can Wi-Fi owner see what sites I visit with VPN?
VPN hides almost everything regarding your browsing histories, such as links clicked, search terms, and the websites you visited. With VPN, your ISP will only get to see the IP address of the VPN you’re using.
Can VPN see what I’m doing?
While using a VPN service, your ISP can only see that encrypted data is traveling to a server. They can’t see the contents of your traffic, or where its travelling to and from. Your ISP won’t be able to see what websites you visit when using a VPN, or anything you do online while you’re using a VPN.
Does Opera VPN change IP address?
If your IP address becomes blocked by server spam services and you’re no longer able to access some websites, you can temporarily change your IP using the Opera VPN.
Does Opera sell your data?
Opera says it does not collect any user data, though the company encourages consumers to send some information about their feature usage to improve the product.
Should I trust Opera?
Is Opera safe? Unfortunately, Opera is not considered a secure browser. Its built-in VPN is logging your data, and there are also other privacy issues. Opera also lacks security extensions.
Does Opera track data?
The Opera browser has a built-in ad blocker and uses a tracker blocker that takes from the EasyPrivacy Tracking Protection List, which can help protect users from seeing ads and being tracked by advertisers and other websites. It bases part of its code on Chromium, which is open-source and therefore can be scrutinized.
Is Opera owned by Google?
Does Opera sell data to China?
The Chinese company is still run from Oslo, meaning Opera is still sharing data with western intel agencies, just like it always had. They trust the Chinese consortium to do the right things, in other words, cooperate fully with western intel agencies.
How does Opera make money?
Opera generates a major part of its revenue by selling its software products and developing advertising solutions for brands and businesses. It has partnered with various organisations to provide its services to users. Opera Browsers: Opera launched itself as a browser-making company and monetised the business.
Why Opera is the best browser?
Which browser do hackers use?
Almost every ethical hacker and security researcher prefers the Mozilla Firefox browser for web-based application penetration testing.
Can private searches be tracked?
Still, the cookies used during private browsing sessions can provide information about your browsing behavior to third parties. This means your web activity can still be tracked.
Why do hackers use Opera?
According to Opera, hackers were able to infiltrate Opera Sync, the service that helps sync browser activities across platforms. That breach may have compromised data that spans usernames and passwords.
Does Opera VPN encrypt traffic?
Opera VPN is a browser proxy that encrypts traffic between the Opera browser and a proxy server. Unlike a true VPN, Opera’s “VPN” only works within the browser, rather than encrypting all traffic on your operating system.
Is opera VPN free to use?
Opera VPN is absolutely free, as it simply comes with the Opera browser. There are no paid subscriptions that would enhance your experience. However, even though this seems to justify its mediocrity, I still don’t recommend using it even if you are on a tight budget.
How do I enable VPN on Opera GX browser?
I downloaded Opera GX Browser, it has a free VPN. Go to your browser settings (or you’ll have a “easy setup” button in the top right corner bellow the Close button) Scroll down to the Privacy and Security section. There you’ll have a “Enable VPN in settings” button. It will take you to Advanced Settings page where you can activate VPN.
Does opera VPN work with WebRTC?
Even within the Opera browser, plugins such as WebRTC for browser-based video calling may not work well with the VPN integration; however, this is something that will likely be improved in the future. Users who are concerned about their online privacy might be better off sticking to VPN solutions that specifically change the IP of the device.
Does opera VPN leak data?
Despite this, our latest round of testing showed absolutely no data leaks while using Opera VPN. This is a good start, but we’d like to see Opera introduce a range of additional security features to make sure it remains leak-free.