Go to the Control Panel, and select Programs > Programs and Features. Right-click Adobe Genuine Service and select Uninstall. Review the message and then select Uninstall to finish uninstalling Adobe Genuine Service.
How do you get rid of Adobe software you are using is not genuine?
Go to the Control Panel, and select Programs > Programs and Features. Right-click Adobe Genuine Service and select Uninstall. Review the message and then select Uninstall to finish uninstalling Adobe Genuine Service.
Should I install genuine software?
Using Adobe software that is not genuine poses a risk for individuals and organizations as it is often modified, leading to issues such as: increased risk of exposure to viruses and malware that can compromise your data. increased chances of the software not functioning correctly or failing completely.
How do I get rid of Adobe not genuine popup on Mac?
How do I get rid of Adobe popups?
Hi, Open up adobe fill and sign and touch the little person symbol, then click the settings top right corner and disable the usage info. And The pop-ups will stop.
Why do I need Adobe genuine service?
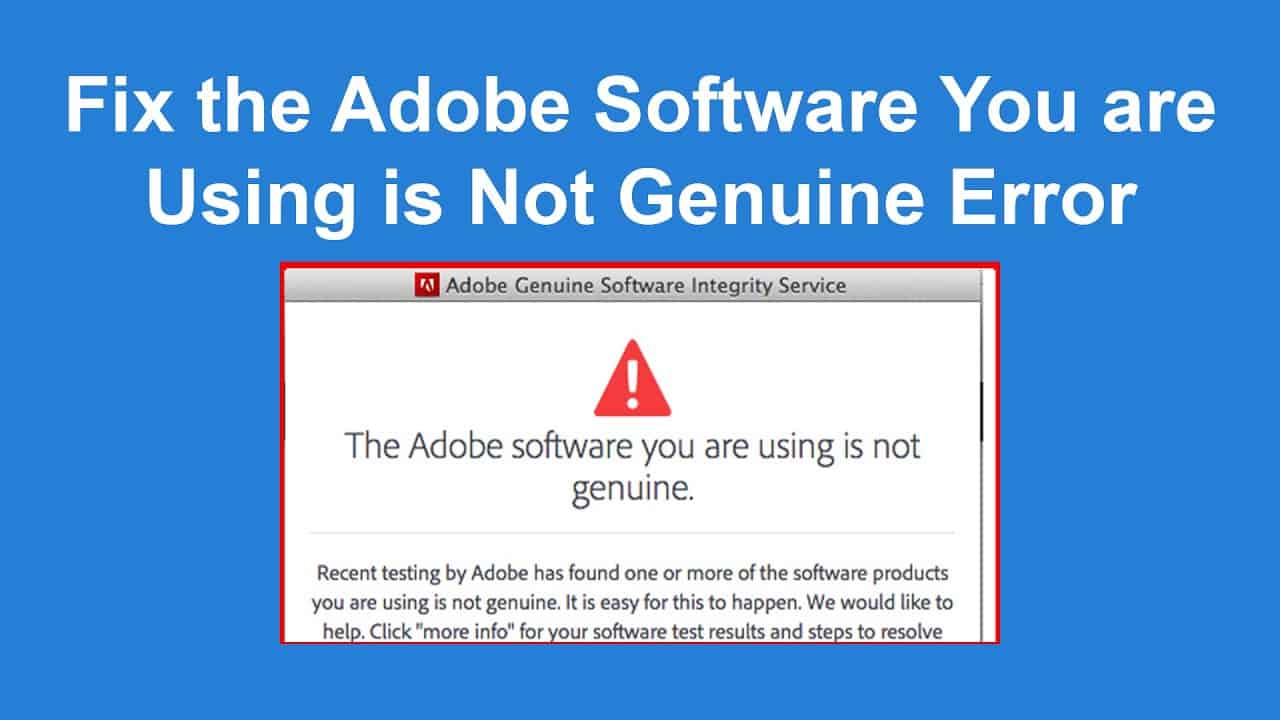
The Adobe Genuine Service periodically verifies whether installed Adobe apps are genuine or not, helping protect customers from security vulnerabilities and harmful malware that may be present in non-genuine apps. * When Adobe apps are found to be not genuine, the AGS can inform the user through notifications.
How does Adobe detect piracy?
To do so, Adobe is bundling its products with a Software Integrity Service that can scan for and detect pirated software. “Adobe now runs validation tests and notifies people who are using non-genuine software. Our tests check for software tampering and invalid licenses,” Adobe explains.
How do I block an Adobe license checker?
Step 1: Type services in the Search box to open it. Then, you need to click the Standard category. Step 2: Then, find Adobe Genuine Software Integrity Service and right-click it to choose Properties. Step 3: Under the General tab, you need to change the Startup Type to Disabled and click the Apply button.
What is Adobe Air and do I need it?
Adobe® AIR® is a multi-operating system, multi-screen runtime that allows you to leverage your web development skills to build and deploy rich Internet applications (RIAs) to the desktop and mobile devices.
What is AdobeGCClient Mac?
Answer: A: AdobeGCClient (Adobe Genuine Copy Validation Client Application) is a process that checks for pirated Adobe software and tampering of Adobe program files.
How do I block an Adobe license checker?
Step 1: Type services in the Search box to open it. Then, you need to click the Standard category. Step 2: Then, find Adobe Genuine Software Integrity Service and right-click it to choose Properties. Step 3: Under the General tab, you need to change the Startup Type to Disabled and click the Apply button.
How do I block Adobe firewall in Windows 11?
Double-click the first Adobe inbound rule. In the new window, under the General tab, select “Block the Connection.” Click “OK,” close the window and repeat this process for every Adobe process you find.
What is genuine software integrity service?
The Adobe Genuine Service periodically verifies whether installed Adobe apps are genuine or not, helping protect customers from security vulnerabilities and harmful malware that may be present in non-genuine apps.
Why does Adobe Flash keep popping up?
The major culprit behind the Adobe Flash Player pop-up ads is the adware program that you might have accidentally installed on your computer while surfing the internet. The advertising-supported software is usually comes bundled with a number of free software which we commonly call freeware.
How do I block Adobe firewall in Windows 11?
Double-click the first Adobe inbound rule. In the new window, under the General tab, select “Block the Connection.” Click “OK,” close the window and repeat this process for every Adobe process you find.
What is Adobe Refresh Manager used for?
Adobe Refresh Manager is a software program developed by Adobe Systems. During setup, the program creates a startup registration point in Windows in order to automatically start when any user boots the PC. Upon being installed, the software adds a Windows Service which is designed to run continuously in the background.
Is it safe to use pirated Adobe?
The plain answer is no, it’s not safe to crack Photoshop. Adobe is formally moving the latest versions of Photoshop and related design and production software to the cloud — specifically, to Adobe’s newly dubbed “Creative Cloud” — where they will only be available via monthly subscription. …
Can Photoshop still be pirated?
Adobe’s new cloud-integrated image editing application Photoshop CC has been pirated within a day of its release. Photoshop CC represents a big step away from standalone software for Adobe, and is only available through a monthly or annual subscription.
Does Adobe allow pirated software?
1 Correct answer. It’s not legal and you shouldn’t use it. Adobe doesn’t permit using cracked software.
How do I stop Adobe Acrobat from accessing the Internet?
In the Manage Internet Access dialog box, choose from the following options: To allow access to all websites, select Allow PDF Files To Access All Web Sites. To restrict access to all websites, select Block PDF Files’ Access To All Web Sites. To restrict access to only the websites you specify, select Custom Setting.
How do I permanently disable Adobe Updater?
To Change the Adobe Updater preferences, do the following: Start the Adobe Updater application from /Applications/Utilities/Adobe Utilities/Adobe Updater5/. When the update screen appears, click the Preferences link. Uncheck the Automatically Check for updates checkbox and click OK.
Should the firewall be on or off?
The most important thing is to make sure your firewall is turned on. See the Mac and Windows firewall links above for more information. Once your firewall is turned on, test it for open ports that could allow in viruses and hackers. Firewall scanners like the one at Gibson Research Corporation (ShieldsUp!)