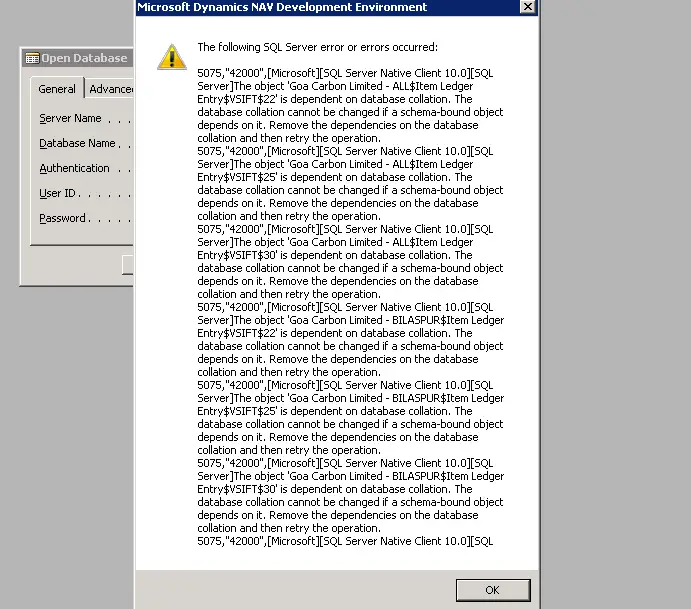
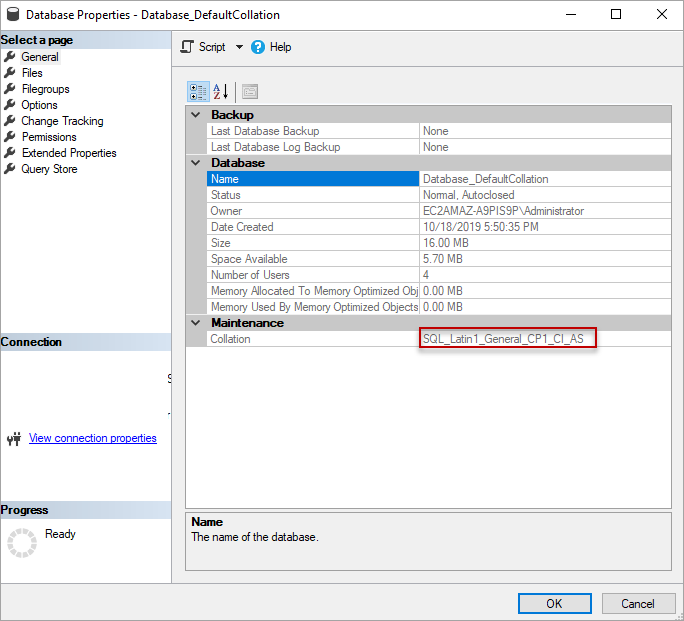
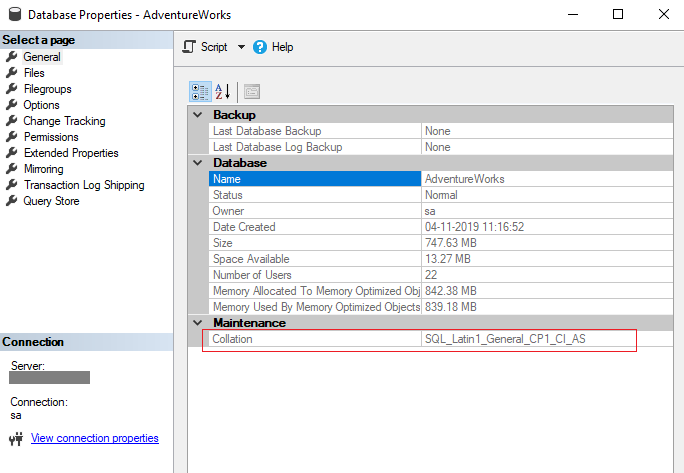
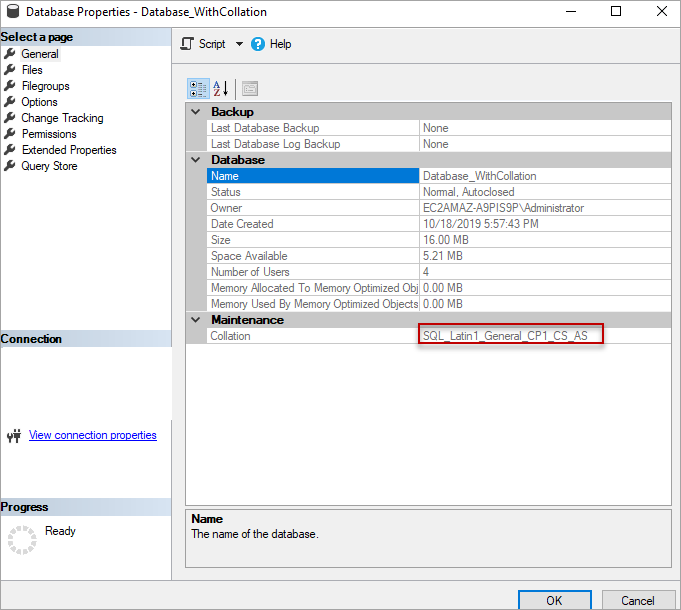
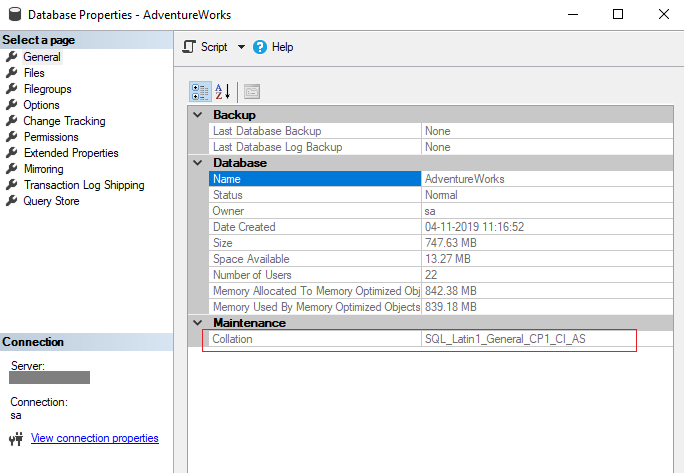
How do you remove the dependencies on the database collation and then retry the operation?
There are two ways to remove the binding of a user-defined function to its base objects: Alter the function so that its definition no longer specifies schema binding. Drop the function (then re-create it without schema binding if required). How do I remove schema bound dependency in SQL Server? There are two ways to remove the binding of a user-defined …