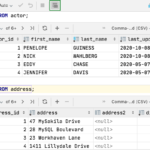
By having your cell number, a scammer could trick caller ID systems and get into your financial accounts or call financial institutions that use your phone number to identify you. Once the scammer convinces your carrier to port out your number, you may never get it back.
What information can someone get with your phone number?
The information found through these sites includes your address, bankruptcies, criminal records, and family members’ names and addresses. All of this can be used for blackmail, stalking, doxxing, social media hacking, or identity theft.
Can a scammer hack my phone?
Once the malicious code is on your smartphone, scammers can infect other devices or hijack yours. The easiest way to protect yourself from these kinds of attacks is to make sure you have cybersecurity on your phone, like Anti-virus for Android.
Can someone hack your phone with just your phone number?
Hopefully this has helped put your mind at ease that when it comes to whether or not someone can hack your device just with your number – the answer is a resounding NO!
What information can someone get with your phone number?
The information found through these sites includes your address, bankruptcies, criminal records, and family members’ names and addresses. All of this can be used for blackmail, stalking, doxxing, social media hacking, or identity theft.
What’s the worst someone can do with your phone number?
If someone steals your phone number, they become you — for all intents and purposes. With your phone number, a hacker can start hijacking your accounts one by one by having a password reset sent to your phone. They can trick automated systems — like your bank — into thinking they’re you when you call customer service.
Can a scammer hack my phone through text?
Android phones can get infected by merely receiving a picture via text message, according to research published Monday. This is likely the biggest smartphone flaw ever discovered.
Should I change my phone number after being scammed?
If you’ve experienced identity theft, you should probably change your phone number. It’s a massive inconvenience, but the pros will outweigh the cons. Let’s understand why. Most people upgrade their smartphone every two years — especially if they’re on a contract plan.
What can a scammer do with my phone number and address?
This can include details like Social Security number, birthdate, or name and address. Depending on what identity thieves find, they can do things like open new credit accounts, steal from existing accounts or commit other crimes using a fake identity.
Can you Unhack your phone?
If you’ve recently sideloaded apps on Android, they might be to blame for the hack. Therefore, to unhack your phone, delete all recently-downloaded apps from it.
What can a hacker do with your phone number and email address?
If a hacker can take control of a victim’s number they may be able to reroute login verification codes to themselves. Or, armed with a phone number, a hacker can send phishing messages or calls to the target to try and obtain their verification codes.
What happens if a scammer has your email?
What will scammers do with your email address? Once a scammer gets your email address, they’ll use it to benefit themselves in any way possible. Many will send you spam email, with the hope of collecting private information such as credit card numbers.
Can iPhone be hacked through phone number?
In some situations, it may even be virtually impossible to hack into an iPhone using just its phone number. This is because hacking into iPhones requires you to enter the target’s iTunes credentials to log into their iCloud. By doing so, you’d be able to retrieve and access relevant data from that device.
What can a scammer do with my phone number and address?
This can include details like Social Security number, birthdate, or name and address. Depending on what identity thieves find, they can do things like open new credit accounts, steal from existing accounts or commit other crimes using a fake identity.
What can a scammer do with my phone number and email address?
Once they have your number, the bad guys can clean out your financial accounts, confiscate your email, delete your data and take over your social media profiles.
What do I dial to see if my phone has been hacked?
Use the code *#21# to see if hackers track your phone with malicious intent. You can also use this code to verify if your calls, messages, or other data are being diverted. It also shows your diverted information’s status and the number to which the information is transferred.prieš 4 dienas
What information can someone get with your phone number?
The information found through these sites includes your address, bankruptcies, criminal records, and family members’ names and addresses. All of this can be used for blackmail, stalking, doxxing, social media hacking, or identity theft.
What to do if you accidentally said yes to a scammer?
What should you do if you receive such a call? Hang up immediately, or better yet, don’t answer calls from unknown numbers. If you think you may have been targeted by this or another scam, check your credit card, telephone and utility bills.
Why am I getting spam calls all of a sudden? Usually it’s because your number has been sold in a group list of phone numbers to other scammers. Remember, you can always report spam calls to the Better Business Bureau and also the Federal Trade Commission.
Can someone hack my bank account with my email address?
It’s also possible hackers could use your email account to gain access to your bank account or credit card information, draining funds from an account, or racking up charges. They might even use your email and password to sign up for online sites and services, sticking you with monthly fees in the process.
Can resetting your phone remove hackers?
The majority of malware can be removed with a factory reset of your phone. This will, however, wipe any data stored on your device, such as photos, notes, and contacts, so it’s important to back up this data before resetting your device.
Can someone hack my phone and read my texts?
By hacking into or otherwise gaining access to the SS7 system, an attacker can track a person’s location based on mobile phone mast triangulation, read their sent and received text messages, and log, record and listen into their phone calls, simply by using their phone number as an identifier.
What happens if a scammer calls your phone number?
Many location-based systems will think it’s you just by the scammer calling from your phone number. If hackers get this far, they can then change all your passwords and lock you out of your own accounts. Very scary stuff. How Do Scammers Get Your Phone Number?
How can I avoid getting scammed on the phone?
The best way to avoid scammers is to not answer any numbers that are not on your contacts list. If they’re important and legit they’ll leave a voice mail. And even if a scammer leaves one, that’s as far as he’s going to get.
How do scammers get your information?
Scammers can be very convincing. They call, email, and send us text messages trying to get our money or our sensitive personal information — like our Social Security number or account numbers. And they’re good at what they do.
How vulnerable is your smartphone to scammers?
Your smartphone is your confidante, your hand-held connection to the world — and one of your biggest vulnerabilities. Scammers can take advantage of day-to-day tasks that seem innocuous, like checking a bank balance or charging a phone at a public USB port, to exploit personal information for their profit.