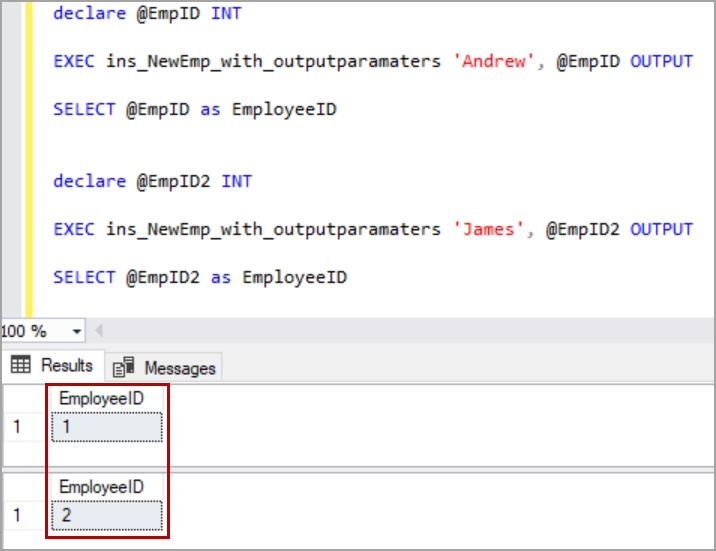
A method is procedure or function that is part of the object type definition, and that can operate on the attributes of the type. Such methods are also called member methods, and they take the keyword MEMBER when you specify them as a component of the object type.
What is method in database?
A database method of a structured type is a relationship between a set of input data values and a set of result values, where the first input value (or subject argument) has the same type, or is a subtype of the subject type (also called subject parameter), of the method.
What are methods in an SQL Server?
Methods perform specific tasks related to the object, such as issuing a Checkpoint on a database or requesting an enumerated list of logons for the instance of Microsoft SQL Server. Methods perform an operation on an object. Methods can take parameters and often have a return value.
What is access methods in SQL?
The Access Methods object in SQL Server provides counters to monitor how the logical data within the database is accessed. Physical access to the database pages on disk is monitored using the Buffer Manager counters.
What are methods in an SQL Server?
Methods perform specific tasks related to the object, such as issuing a Checkpoint on a database or requesting an enumerated list of logons for the instance of Microsoft SQL Server. Methods perform an operation on an object. Methods can take parameters and often have a return value.
What is method and function?
Function — a set of instructions that perform a task. Method — a set of instructions that are associated with an object.
What are methods of query?
Query methods are methods that find information from the database and are declared on the repository interface. Spring Data has pretty versatile support for different return values that we can leverage when we are adding query methods to our Spring Data JPA repositories.
How many methods are there in SQL?
Methods: Using PL/SQL.
What are the 3 types of SQL commands?
There are 3 main types of commands. DDL (Data Definition Language) commands, DML (Data Manipulation Language) commands, and DCL (Data Control Language) commands.
What is access method and types?
An access method is: The portion of a computer’s operating system responsible for formatting data sets and their direction to specific storage devices. Examples from the mainframe world include Virtual Storage Access Method (VSAM) and Indexed Sequential Access Method (ISAM).
What are the three types of access methods?
There are three ways to access a file into a computer system: Sequential-Access, Direct Access, Index sequential Method. It is the simplest access method.
What is schema in SQL?
What are types of functions in SQL?
There are three types of user-defined functions in SQL Server: Scalar Functions (Returns A Single Value) Inline Table Valued Functions (Contains a single TSQL statement and returns a Table Set) Multi-Statement Table Valued Functions (Contains multiple TSQL statements and returns Table Set)
What is method in data structure?
Data structures such as binary search trees — also known as an ordered or sorted binary tree — provide efficient methods of sorting objects, such as character strings used as tags. With data structures such as priority queues, programmers can manage items organized according to a specific priority.
What is process and method?
Method is a particular way of doing something. Process is the step wise actions involved in implementing the method. So process will be different when we carry out a particular job with a different method. For example water can be purified using the method of boiling or using the method of filtration.
What are the four methods of data?
Data may be grouped into four main types based on methods for collection: observational, experimental, simulation, and derived. The type of research data you collect may affect the way you manage that data.
What are methods in an SQL Server?
Methods perform specific tasks related to the object, such as issuing a Checkpoint on a database or requesting an enumerated list of logons for the instance of Microsoft SQL Server. Methods perform an operation on an object. Methods can take parameters and often have a return value.
What is called a method?
A method is a routine that applies to a particular class of objects. Once an object is declared, you can refer to it by its identifier when calling methods.
What’s a method definition?
meth·od ˈmeth-əd. : a procedure or process for attaining an object: as. : a systematic procedure, technique, or mode of inquiry employed by or proper to a particular discipline see scientific method. : a way, technique, or process of or for doing something.vor 6 Tagen
What are the two methods to create a query?
You can create a select query by using the Query Wizard or by working in Design view.
What is a string in SQL?
A string function is a function that takes a string value as an input regardless of the data type of the returned value. In SQL Server, there are many built-in string functions that can be used by developers.
What are the 4 major types of command types in SQL?
Types of SQL Commands Data Query Language (DQL Commands in SQL) Data Definition Language (DDL Commands in SQL) Data Manipulation Language (DML Commands in SQL) Data Control Language (DCL Commands in SQL)