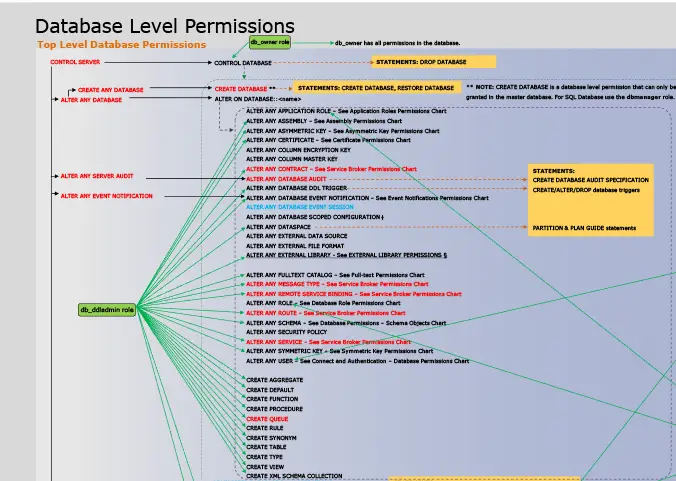
Control statements are SQL statements that allow SQL to be used as a structured programming language. SQL control statements provide the capability to control the logic flow, declare and set variables, and handle warnings and exceptions.CONTROL confers god-like permissions to a “securable” object (e.g. database, etc.) in SQL Server. https://docs.microsoft.com/en-us/sql/relational-databases/security/permissions-database-engine?view=sql-server-2017
What is control server in SQL Server?
SQL Server’s ‘Control server’ permission is a high server-level privilege that must only be granted to individual administration accounts through roles. This administrative privilege must not be assigned directly to administrative user accounts (or any other user accounts).
What is control permission?
In essence if you have the control permission you have every stated permission to the object. This includes the ability to grant permissions to others (probably the most dangerous permission you can grant).
What is control permission on the database?
For example, CONTROL on a database implies all permissions on the database, all permissions on all assemblies in the database, all permissions on all schemas in the database, and all permissions on objects within all schemas within the database.
What is control permission?
In essence if you have the control permission you have every stated permission to the object. This includes the ability to grant permissions to others (probably the most dangerous permission you can grant).
What is control permission on the database?
For example, CONTROL on a database implies all permissions on the database, all permissions on all assemblies in the database, all permissions on all schemas in the database, and all permissions on objects within all schemas within the database.
What is control server?
Definition(s): A controller that also acts as a server that hosts the control software that communicates with lower-level control devices, such as Remote Terminal Units (RTUs) and Programmable Logic Controllers (PLCs), over an ICS network.
What is a principal in SQL?
In SQL Server, the concept for permissions is using principals and securables. Principals are the individuals, groups, and processes granted access to SQL Server. Securables are the server, database, and objects the database contains. Principals can be arranged in a hierarchy.
What is schema in SQL?
What are roles in SQL Server?
SQL Server provides server-level roles to help you manage the permissions on a server. These roles are security principals that group other principals. Server-level roles are server-wide in their permissions scope. (Roles are like groups in the Windows operating system.)
What is DBO in SQL?
The dbo schema is the default schema of every database. By default, users created with the CREATE USER Transact-SQL command have dbo as their default schema. The dbo schema is owned by the dbo user account. Users who are assigned the dbo as default schema don’t inherit the permissions of the dbo user account.
What is sysadmin role in SQL Server?
The “sysadmin” fixed server role is designed to provide accounts assigned to the role full control over all aspects of the SQL Server instance it is a part of. By default, the sa account is assigned to the sysadmin role, making it a prime target for attackers.
What type of control mechanism does SQL support?
SQL Server supports three types of roles: server, database, and application. Server roles share the same scope as logins, which means they operate at the server level and pertain to the database engine as a whole.
Which control covers the majority of concerns for Microsoft SQL Server?
The Answer is CIS benchmarks.
What is control permission?
In essence if you have the control permission you have every stated permission to the object. This includes the ability to grant permissions to others (probably the most dangerous permission you can grant).
What is control permission on the database?
For example, CONTROL on a database implies all permissions on the database, all permissions on all assemblies in the database, all permissions on all schemas in the database, and all permissions on objects within all schemas within the database.
What is C2 command and control?
Command and Control Infrastructure, also known as C2 or C&C, is the set of tools and techniques that attackers use to maintain communication with compromised devices following initial exploitation.
What is this server?
A server is a computer program or device that provides a service to another computer program and its user, also known as the client. In a data center, the physical computer that a server program runs on is also frequently referred to as a server.
What is a C2 server?
What is a C2 server? A command-and-control server is a computer that is controlled by a cybercriminal. Command-and-control servers are used by attackers to maintain communications and send commands to systems inside a target network compromised by malware.
What are database principles?
It is a representation of some aspect of the real world or a collection of data elements (facts) representing real-world information. A database is logical, coherent and internally consistent. A database is designed, built and populated with data for a specific purpose. Each data item is stored in a field.
What is acid SQL?
In the context of transaction processing, the acronym ACID refers to the four key properties of a transaction: atomicity, consistency, isolation, and durability. Atomicity.
What are the 3 types of schema?
Schema is of three types: Logical Schema, Physical Schema and view Schema. Logical Schema – It describes the database designed at logical level. Physical Schema – It describes the database designed at physical level. View Schema – It defines the design of the database at the view level.
What does control mean on a database?
For example, CONTROL on a database implies all permissions on the database, all permissions on all assemblies in the database, all permissions on all schemas in the database, and all permissions on objects within all schemas within the database.
What is the relationship between control and security in SQL Server?
Because the SQL Server security model is hierarchical, CONTROL at a particular scope implicitly includes CONTROL on all the securables under that scope.
What is SQL Server control permission?
One of the most powerful permissions available in SQL Server is control. But what exactly is it? Per BOL: CONTROL: Confers ownership-like capabilities on the grantee.
What is source control option in SQL Server management studio?
Source control option is one feature that was expected by many of the database developers/administrators. This article will describe about the source control option provided in SQL Server Management Studio. The source control used for this article is Microsoft Visual Source Safe 6. It is assumed that a source safe database is created.