Cyber hijacking, or computer hijacking, is a type of network security attack in which the attacker takes control of computer systems, software programs and/or network communications.
What is hijacking example?
The definition of hijack is to take over something that doesn’t belong to you such as a plane, ship, bus or other vehicle, to commandeer or to take over by force. When you take control of a conversation others were having and make it all about you, this is an example of a time when you hijack the conversation.
What is a hijacking attack?
Definition(s): An attack in which the attacker is able to insert himself or herself between a claimant and a verifier subsequent to a successful authentication exchange between the latter two parties. The attacker is able to pose as a subscriber to the verifier or vice versa to control session data exchange.
What is called hijacking?
: to seize possession or control of (a vehicle) from another person by force or threat of force specifically : to seize possession or control of (an aircraft) especially by forcing the pilot to divert the aircraft to another destination. Other Words from hijack.
Why is hijacking used?
Various motives have driven such occurrences, such as demanding the release of certain high-profile individuals or for the right of political asylum (notably Flight ET 961), but sometimes a hijacking may have been affected by a failed private life or financial distress, as in the case of Aarno Lamminparras in the Oulu …
What are the different types of hijacking?
The two main types of session hijacking are Application Layer Hijacking and Transport Layer Hijacking. Each type includes numerous attack types that enable a hacker to hijack a user’s session.
What are five methods of session hijacking?
There are five key methods of Session hijacking: Session Fixation. Session Side Jacking. Cross Site Scripting.
What is a hijacker virus?
Browser hijackers, or simply hijackers, are a type of malware created for the purpose of modifying Internet browser settings without the user’s knowledge or consent.
Is hijacking a crime?
For the full article, see hijacking. hijacking, Crime of seizing possession or control of a vehicle from another by force or threat of force.
Which of the following is an example of control hijacking?
Buffer overflow attacks. Integer overflow attacks. Format string vulnerabilities.
What is hijacking and defense of computer system?
Cyber hijacking, or computer hijacking, is a type of network security attack in which the attacker takes control of computer systems, software programs and/or network communications.
What is content hijacking?
The term comes from the English word, meaning “kidnap”. It consists of duplicating completely the content of a domain in another domain with more authority.
What is a hijack website?
A browser hijacker is a malware program that modifies web browser settings without the user’s permission and redirects the user to websites the user had not intended to visit. It is often called a browser redirect virus because it redirects the browser to other, usually malicious, websites.
When was the last hijacking?
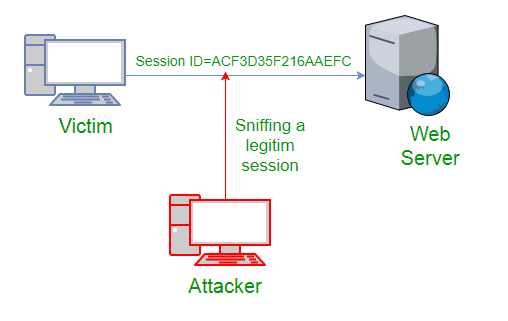
How does session hijacking work?
The Session Hijacking attack consists of the exploitation of the web session control mechanism, which is normally managed for a session token. Because http communication uses many different TCP connections, the web server needs a method to recognize every user’s connections.
What is DNS server hijacking?
Domain Name Server (DNS) hijacking, also named DNS redirection, is a type of DNS attack in which DNS queries are incorrectly resolved in order to unexpectedly redirect users to malicious sites.
Which of the following is an example of control hijacking?
Buffer overflow attacks. Integer overflow attacks. Format string vulnerabilities.
What type of crime is hijacking?
hijacking, Crime of seizing possession or control of a vehicle from another by force or threat of force.
When was the last hijacking?
Who hijacked the first airplane?
The first airplane hijacking happened in 1931 in Peru. Armed revolutionaries approached the grounded plane of pilot Byron Richards and demanded that he fly them over Lima so they could drop propaganda leaflets. Richards refused, and a ten-day standoff ensued before he was eventually released.
What prevents session hijacking?
Does VPN prevent session hijacking?
There are several things you can do to prevent session hijacking and protect your data and identity online, including: Use a VPN. A high-quality VPN can mask your IP address and keep your online activity private and secure. Avoid public or unsecure Wi-Fi networks.