An error correcting code (ECC) is an encoding scheme that transmits messages as binary numbers, in such a way that the message can be recovered even if some bits are erroneously flipped. They are used in practically all cases of message transmission, especially in data storage where ECCs defend against data corruption.
Where is error correction used?
In telecommunication, information theory, and coding theory, forward error correction (FEC) or channel coding is a technique used for controlling errors in data transmission over unreliable or noisy communication channels.
Why networks use error-correcting codes?
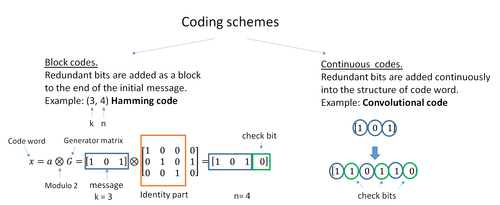
Error Correcting codes are used to ensure integrity, accuracy and fault-tolerance in transmitted data. These are categorized as Block Codes and Convolutional Codes.
Where is error correction used?
In telecommunication, information theory, and coding theory, forward error correction (FEC) or channel coding is a technique used for controlling errors in data transmission over unreliable or noisy communication channels.
What is error correction give examples?
The most classic example of error-correction is the repetition code, where for each bit in an input message, we duplicate each bit multiple times. For example, if you had the message 01101 we could encode it using this repetition method and it would become 000 111 111 000 111 .
How many types of error correction are there?
There are three types of procedures for error correction. All three types are presented after the learner engages in a defined incorrect response (including no response within a specific amount of time) and are combined with a differential reinforcement procedure. Each of the three is defined independently below: 1.
What are the most commonly used error detection techniques?
Error Detection Techniques There are three main techniques for detecting errors in frames: Parity Check, Checksum and Cyclic Redundancy Check (CRC).
Which of the following error detection correction is most commonly used?
The method of detecting and correcting burst errors in the data sequence is called “Burst error correction”. Hamming code or Hamming Distance Code is the best error correcting code we use in most of the communication network and digital systems.
What is error correction in language teaching?
Error correction is a way to develop competence of language learners in a second or foreign language. It can be used in order to attain conscious knowledge of a second or foreign language, and in learning the language’s rules.
What is correction of errors in accounting?
An Error Correction is the correction of an error in financial statements that were previously issued. Error corrections can be an error in the measurement, recognition, presentation or disclosure in financial statements.
What is a correction of error?
Correction of Error is a process for improving quality by documenting and addressing issues. You will want to define a standardized way to document critical root causes, and ensure they are reviewed and addressed.
Where is error correction used?
In telecommunication, information theory, and coding theory, forward error correction (FEC) or channel coding is a technique used for controlling errors in data transmission over unreliable or noisy communication channels.
What is error correction and its types?
Error Correction can be handled in two ways: Backward error correction: Once the error is discovered, the receiver requests the sender to retransmit the entire data unit. Forward error correction: In this case, the receiver uses the error-correcting code which automatically corrects the errors.
What are different types of error detecting and correcting codes?
It is not always possible to avoid those errors, but it is possible to detect and correct the error. First, it is important to detect an error. It is done by adding an extra bit to the transmitted data. There are different codes like parity code, block parity, hamming code, etc to detect and correct the errors.
Why do we require Hamming codes?
Why do we require hamming codes? Explanation: Hamming codes are used for the purpose of error detection and correction. It is also used for channel encoding and decoding. They are linear-error correcting codes.
Which is the best form of error correction?
Self-correction considered to be the best form of correction. Teachers should encourage students to notice their own errors and to make attempts to correct themselves.
How is CRC code used in error detection?
The Cyclic Redundancy Checks (CRC) is the most powerful method for Error-Detection and Correction. It is given as a kbit message and the transmitter creates an (n – k) bit sequence called frame check sequence. The out coming frame, including n bits, is precisely divisible by some fixed number.
Which is the most efficient error correction method?
The best-known error-detection method is called parity, where a single extra bit is added to each byte of data and assigned a value of 1 or 0, typically according to whether there is an even or odd number of “1” bits.
Why is error checking important?
There is always the chance that data has been corrupted (changed in some way) during transmission. This is true regardless of the distance of transmission. To avoid having corrupted data it is really important that computers check for errors and correct them wherever possible.
Can CRC be used for error correction?
The Cyclic Redundancy Check (CRC) method is used for error detection. CRC is used to control such factors in received information. In this paper, the new method based on CRC has been introduced that is able to detect the exact place of double bits error and correct them.
How does CRC work in networking?
A cyclic redundancy check (CRC) is an error-detecting code commonly used in digital networks and storage devices to detect accidental changes to digital data. Blocks of data entering these systems get a short check value attached, based on the remainder of a polynomial division of their contents.
When should errors be corrected?
When to correct errors in accuracy-based lessons. If you’re teaching a class or activity that aims for accuracy, for example applying a new grammar rule during a conversation, you can correct immediately after the mistake has been made, assuming that it is a mistake about said rule.