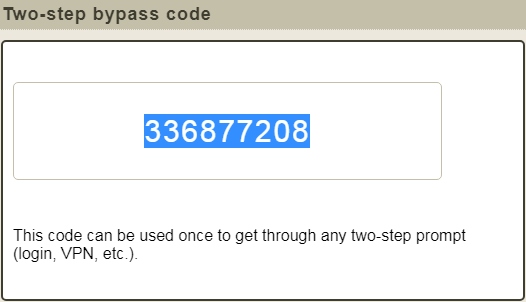
Bypass codes are nine-digit passcodes that you can use to complete multi-factor authentication prompts. Enter the codes in the Passcode field of the MFA prompt. DIT recommends you use bypass codes as a backup for when you do not have your primary MFA device available.
What is the bypass code?
A bypass code is a temporary passcode created by an administrator for a specific user.
Why is duo asking for a bypass code?
Duo Bypass Codes can be used to access resources protected by Duo when your device is unavailable. You may also need to use Bypass codes if your device is lost, stolen, or replaced. Bypass codes should be placed in a secure location.
How can I bypass duo security code?
To generate a bypass code: Log in to the Duo Admin Panel and click Users in the left sidebar. Select a user by clicking their username. Scroll down to the bottom of the user properties page and click the Add Bypass Code button.
How can I get my Duo mobile activation code?
With a passcode: When opening the Duo mobile app, it will display a six digit code which you can enter after selecting “Enter a Passcode” from the authentication screen. If you have a hardware token, select “Enter a Passcode”, press the button on the token, then enter the code the token displays.
What is bypass in Iphone?
Q #1) What is an iCloud bypass app? Answer: An iCloud bypass software allows you to gain access to your iCloud account if you happen to lose your password. The bypass activation lock app will allow you to unlock your phone without having to enter the ID or password.
How do I use Duo hardware tokens?
To authenticate via Duo using a hardware token, click the “Enter a Passcode” button when prompted. Press the button on your hardware token to generate a new passcode, type it into the space provided, and click “Log In” (or type the generated passcode in the “second password” field).
Where is the secret key for duo?
Log in to the Duo Admin Panel. Click on Applications. Click on the application for which you’d like to generate a new secret key. On the application’s properties page, click Reset Secret Key.
What is key on Duo Mobile?
What are Security Keys? A security key plugs into your USB port and when tapped or when the button is pressed it sends a signed response back to Duo to validate your login. Duo uses the WebAuthn authentication standards to interact with your security keys. You may also see WebAuthn referred to as “FIDO2”.
How do I reconnect my Duo account?
Open the Duo Mobile app on your new device. If you previously created a third-party account backup, Duo Mobile notifies you that it found accounts to recover. Tap Automatically reconnect to begin the recovery process. Enter your recovery password and then tap Reconnect.
Where is the QR code on a Duo phone?
Open Duo Mobile and tap Add in the upper right of your accounts list to go to the account type selector. If the new account you want to add shows you a QR code to scan with an authenticator app, tap Use QR code from Duo Mobile’s Add account list. Scan the QR code with your camera to add the account.
Why is my Duo not working?
Make sure you are running the latest version of Duo Mobile. If tapping “Open Duo Mobile” doesn’t launch Duo Mobile, reboot your phone and try to authenticate again. If you have a personal profile and a work profile on your device, verify which profile Duo Mobile is installed on.
What is the bypass for GoGuardian?
GoGuardian has various block pages. When a page is blocked by GoGuardian Admin’s custom filtering policies, students will receive the GoGuardian Admin block page, which includes a “Bypass” button. Users may enter the Bypass Password and be unlocked for a preset amount of time.
Can Apple ID be bypassed?
If you’ve purchased a second-hand iOS device with the old Apple account on it but you don’t know the correct password, the easiest way to bypass Apple ID is to ask the previous owner to remove the original Apple ID for you. Once the old Apple ID gets removed, you can log in using your own Apple ID.
What is the bypass code?
A bypass code is a temporary passcode created by an administrator for a specific user.
Can I update bypass iPhone?
It is possible to push iOS update MDM without losing your new status. Once you have successfully removed iOS MDM configuration profile and can finally use a corporate iDevice outside of office without any limits, you can also keep this bypass active while upgrading to newer version of Apple iOS firmware.
Is it possible to unlock a iCloud locked iPhone?
Get the Original Owner to Unlock Your iPhone. One of the easiest ways to unlock an iCloud locked iPhone is to get the original owner to unlock the phone for you. Since the original owner will likely have their iCloud password with them, they will be able to enter the password on the iPhone and get it unlocked.
Sign Up for an account. Click on Apps in Menu. Scroll down and look for Brackets and click on it. Now you can access any website you want.
How do I activate duos on my Iphone?
Activate Duo Mobile for the First Time To proceed with adding your initial Duo account to Duo Mobile, tap Use a QR code. Use your camera to scan the QR code shown by Duo Enrollment in your browser. If you’re prompted to allow Duo Mobile permission to use your device camera, please grant it.
How do hardware authentication tokens work?
Hardware token. Many hardware tokens contain an internal clock that, in combination with the device’s unique identifier, an input PIN or password, and potentially other factors, is used to generate a code, usually output to a display on the token. This code changes on a regular basis, often every 30 s.
What is hardware OTP token?
A one-time password token (OTP token) is a security hardware device or software program that is capable of producing a single-use password or PIN passcode. One-time password tokens are often used as a part of two-factor and multifactor authentication.
What is a hardware token used for?
In simple terms, a hardware token (also known as a security or authentication token) is a small physical device that you use to authorize your access to a specific network. Its purpose is to provide an extra security layer by ensuring two-factor authentication.