Everything stored in iCloud, including iCloud photos, is securely encrypted in transit and stored with encryption keys. Encryption keys are stored on Apple’s servers. Without these encryption keys, files can not be decrypted. Apple also uses “end-to-end” encryption for data.
Are iPhone photos encrypted?
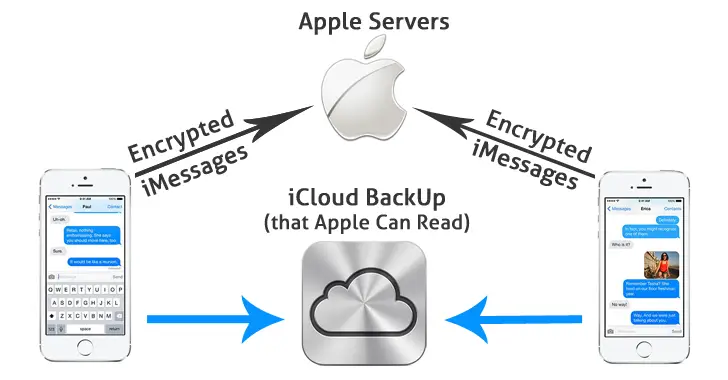
We designed iMessage to use end-to-end encryption, so there’s no way for Apple to decrypt the content of your conversations when they are in transit between devices. Attachments you send over iMessage (such as photos or videos) are encrypted so that no one but the sender and receiver(s) can access them.
Can Apple decrypt photos?
Apple’s encrypts photos in transit and stores them encrypted, but has the decryption key to decrypt them if necessary—to serve data stored in iCloud under subpoena, or to make your iCloud photos available in a web browser.
Can Apple see my photos?
Apple’s technology scans photos in your iCloud photo library and compares them to the database. If it finds a certain number of matches (Apple has not specified what that number is), a human will review it and then report it to NCMEC, which will take it from there.
Are iCloud pictures encrypted?
iCloud uses best-in-class security technologies, employs strict policies to protect your information, and leads the industry by adopting secure, privacy-preserving technologies like end-to-end encryption for your data.
Who can see your iCloud photos?
Photos need to be actually shared through that album to be visible to other members of the family group however. So unless you actually share you photos, they cannot be seen by anybody else.
As for encryption, all your data is protected in transit with TLS or SSL, and your files already on the iCloud servers are encrypted with AES 128-bit encryption.
Does Apple use end-to-end encryption?
Data encryption For additional privacy and security, many Apple services use end‑to‑end encryption, which means that only you can decrypt and access your information, and only on trusted devices where you’re signed in with your Apple ID.
Is iCloud safer than Google Drive?
iCloud is the more secure platform, although Google Drive has made several necessary steps forward recently. Both platforms enable you to use multi-factor authentication, which we highly recommend. Almost all data stored on iCloud’s servers is encrypted both in transit and at rest to 128-bit AES standard.
Can Apple recover permanently deleted photos?
On iCloud.com, you can recover files deleted from both iCloud Drive and other apps within the last 30 days, whether you deleted them on iCloud.com or another device that has iCloud Drive turned on. However, you can’t recover or restore files you permanently remove.
Is iCloud safe for private photos?
Everything stored in iCloud, including iCloud photos, is securely encrypted in transit and stored with encryption keys. Encryption keys are stored on Apple’s servers. Without these encryption keys, files can not be decrypted. Apple also uses “end-to-end” encryption for data.
Are iPhone photos deleted permanently?
When you delete photos and videos, they go to your Recently Deleted album for 30 days. After 30 days, they’ll be permanently deleted.
Can photos be encrypted?
Phone apps enable you to encrypt your images directly on your phone. Encryption apps for Android-based smartphones include WhisperCore and Droid Crypt, and iPhone apps include Kryptos and SecuMail.
How do I know if my iPhone is encrypted?
Thankfully, it’s easy to set up if it isn’t. Go to Settings > Security and you will see the Encrypt Phone option. If your phone is already encrypted, it will say so but if not, tap on it and follow the instructions.
Is iCloud private and secure?
iCloud is generally secure overall. It employs high-quality encryption protocols, and it secures data processing end-to-end. Not to mention, Apple is dedicated to user privacy, regardless of where they live.
Is iCloud safe from hackers?
iCloud is Extremely Secure “Data stored in the iCloud is encrypted so a hacker needs a key to access it. Meaning to say: this storage system is extremely secured.”
Has iCloud ever been hacked?
The short answer to that question is yes, however, our research has shown that iCloud hacking is not possible in the same way it used to work. Spyware is unable to download a full backup of a victim’s device from iCloud. Instead, it now works in a more limited way by acquiring iCloud Synced Data.
Is iCloud a good place to store photos?
Bottom line. For me, iCloud Photo Library is an excellent way to bring my images and video to all my devices. It boasts impressive sync capabilities, offline photo access, and easy management and backup, even for gigantic libraries. But it also has a few caveats that, while not deal-breakers for me, might be for others …
Can Apple see my iCloud files?
Yes, but that’s not end-to-end encryption. End-to-end would mean that the content is encrypted and decrypted on the user’s devices only, using keys that Apple never sees. Apple uses HTTPS for the “in transit” part, but the data is decrypted on their end and then re-encrypted for storage.
Can someone hack my iPhone photos?
Image Backup But as convenient as it may be, having them on the iCloud also makes it available to hackers. Hackers have been known to attack iCloud accounts to access private data like photos and videos. Disable settings like Photo Sharing and Photo Stream to protect your photos from being accessed.
Will deleting pics from iPhone delete from iCloud?
When you delete a photo or video from the Photos app on your iPhone, iPad, iPod touch, or Mac, it also deletes from your iCloud Photos and any other devices where you’re signed in to iCloud Photos. It also no longer counts towards your iCloud storage.
Can someone see your photos on iPhone?
No they can’t. Those photos are for your device only. They can’t see them.