Brave and Google Chrome are both Chromium-based web browsers; they’re both compatible with most of the extensions found on the Chrome Web Store. And the vast majority of extensions you find there are safe.
Can Chrome extensions harm your computer?
Browser extensions are a great way to expand the functionality of your favorite browser. But bad Chrome extensions can cause much more harm than help. Whether they use lots of system resources, collect your data, install adware, redirect your searches to spammy sites, or similar, you don’t want them on your system.
Can Chrome extensions steal passwords?
Chrome extensions cannot steal your passwords by default. When you add an extension, you grant a set of permissions. If you approve access to site content, sensitive data can be read by the extension, including login usernames and passwords. It’s essential to vet extensions before installing them.
Can Chrome extensions harm your computer?
Browser extensions are a great way to expand the functionality of your favorite browser. But bad Chrome extensions can cause much more harm than help. Whether they use lots of system resources, collect your data, install adware, redirect your searches to spammy sites, or similar, you don’t want them on your system.
Are all browser extensions safe?
It really depends on the type of extensions you are installing; the biggest security risk they pose is from permissions management. The good news is that most modern web browsers have a permission system in place for extensions and some use very few permissions to perform their tasks.
Can browser extensions steal data?
Many browser extensions are safe, but some are malicious and could expose you to fraud and identity theft.
Can Chrome extensions have viruses?
Malicious Chrome extensions can be created with malicious code from the start or they can be “updated” with malicious code once they gain a certain level of popularity.
Should Chrome use extensions?
Answer: Chrome extensions come from a wide variety of developers. Google considers most extensions to be safe use. However, users should proceed with caution before installing extensions that have few downloads or reviews.
Can browser extensions be malware?
Dangerous browser extensions can seriously undermine your security. At present, Google Chrome is the only browser that asks you to agree to browser extension permissions. Left unchecked, dangerous browser extensions could log your keystrokes or even provide a passage for malware to make its way onto your device.
What is a malicious extension?
Extension malware is any browser extension that was developed intentionally with coding that causes undesirable behaviors or whose code has been compromised by an attacker to do so. Like other types of software, browser extensions can be designed to carry out attacks.
Do Chrome extensions collect data?
Starting next year, Chrome extensions will show what data they collect from users. Google will add a “Privacy practices” section on each Chrome extension’s Web Store page listing what data they collect from users and what the developer plans to do with it.
Can extension see my password?
Browser extensions are much more dangerous than most people realize. These small tools often have access to everything you do online, so they can capture your passwords, track your web browsing, insert advertisements into web pages you visit, and more.
What do Chrome extensions have access to?
Your tabs and browsing activity: The app or extension can see the URLs and titles of websites you visit. It can also open and close tabs and windows, as well as navigate to new pages in open tabs and windows. Your physical location: The app or extension can use the current location of your computer or device.
Can Chrome extensions have viruses?
Malicious Chrome extensions can be created with malicious code from the start or they can be “updated” with malicious code once they gain a certain level of popularity.
Is Orange Monkey extension Safe?
Yes, it is a reliable user scripts manager Chrome extension with over 2 million+ users.
Is music search for Chrome safe?
Due to this, Music Search for Chrome is classified as a browser hijacker. Additionally, it spies on users’ browsing activity. Since most users download/install browser hijackers unintentionally, they are also deemed to be PUAs (Potentially Unwanted Applications).
Is quick files download extension Safe?
Quick Files Download is a rogue browser extension that we discovered while inspecting untrustworthy download webpages. This piece of software is promoted as a download management tool. However, Quick Files Download actually operates as adware – it displays various advertisements and spies on users’ browsing activity.
Can Chrome extensions harm your computer?
Browser extensions are a great way to expand the functionality of your favorite browser. But bad Chrome extensions can cause much more harm than help. Whether they use lots of system resources, collect your data, install adware, redirect your searches to spammy sites, or similar, you don’t want them on your system.
Can browser extension steal password?
Remember that spell-checking browser extension that asked for permissions to read and analyze everything you type? Cybersecurity experts warn that there’s a high chance that some extensions are misusing your consent to steal the passwords you punch into the web browser.
Are Google extensions free?
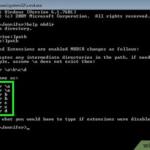
All of these extensions are free, so there’s no harm in giving them a try. You can easily disable or remove them by typing chrome://extensions/ into the Chrome address bar, or right-clicking an extension’s icon in the toolbar to remove it.
What is the most popular browser extension?
Google Chrome usage has increased steadily over the past few years, and it is now the most popular browser in the U.S.
Can Google Chrome be infected?
Google Chrome includes a feature to synchronize your browser data between computers, including web browser extensions. This is a convenient feature, but when malware infects your Google Chrome browser, it can hitch a ride on the sync data and become difficult to remove with anti-virus programs.