AnyDesk is used legitimately by millions of IT professionals worldwide, to remotely connect to their clients’ devices to help with technical issues. However, scammers can try to misuse AnyDesk (or any other remote access software) to connect to your computer and steal data, access codes, and even money.
Can you get hacked via AnyDesk?
AnyDesk is used legitimately by millions of IT professionals worldwide, to remotely connect to their clients’ devices to help with technical issues. However, scammers can try to misuse AnyDesk (or any other remote access software) to connect to your computer and steal data, access codes, and even money.
Is AnyDesk on PC safe?
AnyDesk Remote Desktop Software comes with the highest security standards. From military-grade encryption to customizable security features, AnyDesk offers outstanding security that perfectly fits your needs.
What can be accessed through AnyDesk?
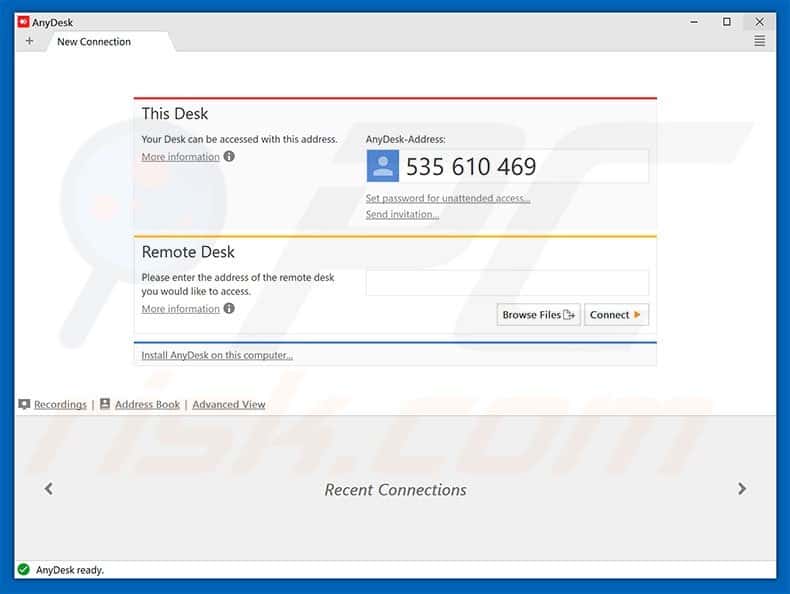
AnyDesk is a remote desktop application distributed by AnyDesk Software GmbH. The proprietary software program provides platform independent remote access to personal computers and other devices running the host application. It offers remote control, file transfer, and VPN functionality.
Is IT safe to give AnyDesk address?
AnyDesk itself is secure, trusted and used by millions of people and 15,000 companies in 165 countries. It’s completely secure and a tool for when IT experts want to work on remote devices without being on-site.
Can AnyDesk see my screen?
Increased privacy. When working remotely on the PC at the office, your activity can still be visible to your co-workers. By enabling Privacy Mode, the screen at the office will be black and all activity will be invisible.
How do I protect from AnyDesk?
You can do that in the security settings: Simply click “Enable unattended access” and choose a secure password. Don’t forget: A strong password is the first line of defense! Unattended access is where the security layers really start to show: If you want, you can set up two-factor authentication.
What are the disadvantages of AnyDesk?
The Cons. It can be slightly intimidating for first-time users. It cannot work without an active internet connection. The free version doesn’t have the address book feature.prieš 6 dienas
What can a scammer do with remote access to your computer?
In a remote access scam, a scammer attempts to persuade you into giving them remote control over your personal computer, which allows the scammer to con money out of you and steal your private information.
Does AnyDesk use camera?
He simply uses AnyDesk: Almost every laptop has a built-in webcam, and with AnyDesk, you can turn it on from anywhere and have a clear view of your room. That’s where you’ll find your kitties sleeping soundly. Be sure to use a strong password and disconnect the session afterwards.
How do I make AnyDesk secure?
You can do that in the security settings: Simply click “Enable unattended access” and choose a secure password. Don’t forget: A strong password is the first line of defense! Unattended access is where the security layers really start to show: If you want, you can set up two-factor authentication.
What are the disadvantages of AnyDesk?
The Cons. It can be slightly intimidating for first-time users. It cannot work without an active internet connection. The free version doesn’t have the address book feature.prieš 6 dienas
Is AnyDesk safe to use in mobile?
Whether it’s a scam email or a phone call, scammers could ask you to download remote access software and grant them access to your smartphone. Remote desktop tools like AnyDesk are generally very secure, using layers of encryption and many security features, but the chances of getting tricked are still there.
Can someone remote into my computer without me knowing?
“Can someone access my computer remotely without me knowing?” The answer is “Yes!”. This could happen when you are connected to the internet on your device.
Can someone turn on my laptop camera remotely?
There’s a good reason so many people put tape over their computer webcams or use a dedicated webcam cover to shut them off: Webcams can be hacked, which means hackers can turn them on and record you when they want, usually with a “RAT” or remote administration tool that’s been secretly uploaded.
How do I know if AnyDesk is disconnected?
Check the corner of the taskbar next to the clock if the AnyDesk icon is showing up. If yes, then click on it and terminate the connection. If you have installed AnyDesk, uninstall it. If you have only let it run for one time only, then you are safe.
Can I control a phone with AnyDesk?
Mobile Remote Control Not only does AnyDesk enable you to access devices with different operating systems, but it also allows you to control them remotely as if you were in front of them – even with Android devices.
Can AnyDesk see my screen?
Increased privacy. When working remotely on the PC at the office, your activity can still be visible to your co-workers. By enabling Privacy Mode, the screen at the office will be black and all activity will be invisible.
How do I stop AnyDesk from running in the background?
Exclusive Unattended Access To force the AnyDesk client to only be accessible using the Unattended Access password, “Never show incoming session requests” can be enabled in Settings > Security > Interactive Access.
What can a scammer do with remote access to your computer?
In a remote access scam, a scammer attempts to persuade you into giving them remote control over your personal computer, which allows the scammer to con money out of you and steal your private information.
Does AnyDesk use camera?
He simply uses AnyDesk: Almost every laptop has a built-in webcam, and with AnyDesk, you can turn it on from anywhere and have a clear view of your room. That’s where you’ll find your kitties sleeping soundly. Be sure to use a strong password and disconnect the session afterwards.
How do hackers take control of your computer?
Another common way that hackers use to gain control of your computers is by sending out Trojan Viruses disguised as email attachments. Hackers typically send out these messages to 1000s of users with enticing headings and an attachment which they are hoping you will open.
Is AnyDesk a scam?
However, scammers can try to misuse AnyDesk (or any other remote access software) to connect to your computer and steal data, access codes, and even money. #1. Rule Number One Never give anyone you don’t know access to your devices. #2. Rule Number Two Never share online banking login details or any passwords with anyone.
How do I remove AnyDesk from my computer?
If you notice that AnyDesk has infiltrated systems without your consent, or you have downloaded it from a third party source, immediately eliminate it and scan the system with a reputable anti-virus/anti-spyware suite to remove all remnants. AnyDesk should be downloaded from its official website only.
Is it safe to use any desk?
We use it for people who work from home for set up and maintenance. Provided you don’t have a password for anydesk, there is no way for them to get in without your permission. If they do, provided its not on, there is still no way in. The only risk is if you have it set to auto start, walk away from your PC, and they have a password.
Can Someone remotely access my phone with AnyDesk?
The above information is just for you that what AnyDesk is. You said you accidentally install AnyDesk on your phone , then no one can remotely access your phone with that app because it it need unique code for remotely access. I had a scammer call me, asking me to install TeamViewer.