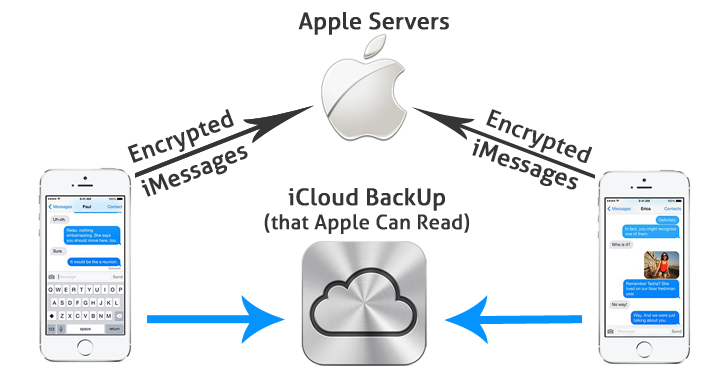
End-to-end encryption With watchOS, iOS, and iPadOS, your messages are encrypted on your device so they can’t be accessed without your passcode. iMessage and FaceTime are designed so that there’s no way for Apple to read your messages when they’re in transit between devices.
Can police see iMessages?
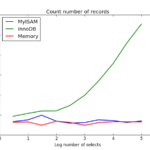
Law enforcement can retrieve messages via Google / iCloud backups. The chart shows that subpoenas will not grant access to message content for six of the nine secure messaging apps. The three that do give up “limited” content are iMessage, Line and WhatsApp.
Can the government look at iMessage?
According to the FBI’s “Lawful Access” guide, if served with a court order or a search warrant, Apple must hand over basic subscriber information as well as 25 days’ worth of data about queries made in iMessage, such as what a targeted user looked up in iMessage and also which other people searched for that targeted …
Can someone read my iMessages through iCloud?
Answer: A: Yes. If they can login to your iCloud then they have the exact same access as you do. iCloud has no way of knowing who is using the AppleID and signing in.
Does iMessage get monitored?
“Because iMessage is encrypted end-to-end, we do not have access to the contents of those communications,” Apple said. “In some cases, we are able to provide data from server logs that are generated from customers accessing certain apps on their devices.”
Is iMessage really secure?
End-to-end encryption protects your iMessage and FaceTime conversations across all your devices. With watchOS, iOS, and iPadOS, your messages are encrypted on your device so they can’t be accessed without your passcode.
Can FBI see your iMessage?
All but one (IP address) of iMessage can be accessed by the FBI. For WhatsApp, Line and iMessage, the access to message content is limited, while in the remaining, the FBI said it has no access to message content.
Can police recover deleted iMessages?
Keeping Your Data Secure The answer is yes—by using special tools, they can find data that hasn’t been overwritten yet. However, by using encryption methods, you can ensure your data is kept private, even after deletion.
Who can access my iMessages?
They can only view this information if they are logged into your account on their iDevice. For example, an iPhone, iPad and MacBook all on the same account will receive all messages sent or received from the other machines (barring a lack of network connectivity). My suggestion to you is to change your password.
Does Apple save text messages?
The IOS Messages app does not support the saving of text messages, nor are there any apps which really do this well (other than connecting to iTunes with a cable – ugh!). Contrastly, Android has an app like SMS Backup + which will automatically backup all call logs and text messages to Google folders (wirelessly).
How do I make my iMessage private?
Turn Off Message Preview to Make Message Private on iPhone Open Settings app on your iPhone. Navigate to Notifications > Messages. In the Messages section, you will see two options; you can either use the Message Preview feature to turn on for the Lock Screen or disable the feature completely.
Can someone see my iPhone messages?
Will he be able to read all of my iPhone’s text messages? Yes. If he has an iPad, Mac, or iPhone hooked up to the same iCloud account as you use on your iPhone, then all of the texts you receive will notify him too, and he can see your sent texts and send some of his own too.
How do you permanently delete iMessages?
Deleting Texts From Your Android Phone You can delete individual texts or conversations within your messaging app. For individual texts, hover over the text you want to delete within the conversation and select the trash can icon in the top right corner to delete.
Can phone companies see iMessages?
All replies. As far as the carrier is concerned, iMessages are data, just like streaming music, downloading email. They don’t see the content of the messages or any information on when or to whom they are sent.
What does Apple do with reported junk messages?
The sender’s information and the message are sent to Apple, and the message is permanently deleted from your device. Note: Reporting junk or spam doesn’t prevent the sender from sending messages, but you can block the number to stop receiving them.
How long are deleted iMessages stored?
The good news for iPhone users however, is that the iPhone tends to store deleted text messages longer than other phones, according to Jesse Lindmar, Assistant Director of Computer Forensics at Sensei Enterprises. He states that messages up to two years old can be recovered, although this happens rarely.
Can police retrieve deleted iMessages?
Keeping Your Data Secure So, can police recover deleted pictures, texts, and files from a phone? The answer is yes—by using special tools, they can find data that hasn’t been overwritten yet. However, by using encryption methods, you can ensure your data is kept private, even after deletion.
Can police get iPhone text messages?
Deleted text messages are usually retrievable from a phone, but before beginning the process, law enforcement officers would need to obtain a court order. Once obtained, officers can use mobile device forensic tools (MDFTs) to extract any data from a device, including emails, texts, images and location data.
Do iMessages show up in phone records?
Question: Q: Can I messages be seen on phone bills Answer: A: No, iMessages don’t show on your bill. They are sent as data.
Does Apple give information to police?
Apple will not process a Government or Law Enforcement Information Request unless it is received from the requesting officer’s official government or law enforcement email address.
Can iMessage be hacked?
Apple iMessage uses end-to-end encryption, and it is one of the safest messaging apps available right now. In addition, it uses a security system known as BlastDoor to protect it against malware attacks. It is a safe app because all the photos, videos, and other attachments have encryptions.
Can Apple access my iCloud?
iCloud Keychain uses end-to-end encryption and is designed so that only you can access this information and only on devices where you’re signed in to iCloud. No one else, not even Apple, can access your iCloud keychain data.