AutoKMS is not really a virus, but a hack tool downloaded intentionally by most users who try to activate unregistered Microsoft products. In order to get rid of it, you can try to uninstall it as you do with any other application.
What happens if you delete AutoKMS?
It can grant access to hackers or download malicious software and much more. Some Microsoft technicians claim that AutoKMS is a variation of the Troyan virus, but not all go that far. Simply because you can uninstall it anytime, and that’s just not the case with Trojan viruses.
Does uninstalling KMSPico after activation?
Yes you can remove KMSpico but dont do it. You may have activated windows or ms office with kmspico now you think that it is useless, no its not like this, to keep your windows activated do not remove kmspico. If you remove it then your windows will go again in trail mode.
What happens if you delete AutoKMS?
It can grant access to hackers or download malicious software and much more. Some Microsoft technicians claim that AutoKMS is a variation of the Troyan virus, but not all go that far. Simply because you can uninstall it anytime, and that’s just not the case with Trojan viruses.
Is kms activator a virus?
Originally Answered: Is KMS Activator is a Virus Program (malware)? No, KMS Auto is not a Virus file but it is simply a activator file. It just activator or unlock the full version of application.
Is AutoKMS a malware?
AutoKMS is Malwarebytes’ generic detection name for hacktools that are intended to enable the illegal use of Microsoft products like Windows and Office.
How do I check my KMS activation count?
To check if the client computer is properly activated, you can either check in the Control Panel System or run the SLMgr script in the command prompt. To check run Slmgr. vbs with the /dli command-line option. It will give you details about the Windows installation and its activation and licensing status.
Is KMSpico a Trojan?
It is extensively disseminated under a variety of names and variants on phoney download sites and file-sharing networks like BitTorrent. It can lead to a variety of dangerous acts as soon as it is installed, including data theft, Trojan operations, and more.
Is KMSpico spyware?
KMSPico is not a legitimate tool and is developed by cyber criminals, rather than the Microsoft corporation. Therefore, using this tool violates Windows Operating System terms and conditions. In addition, it is often distributed by dubious websites containing malicious content.
What is HackTool KMSpico?
HackTool. KMSpico is Malwarebytes’ detection name for a Hacktool that allows the user to use Microsoft software illegally.
Is it okay to remove Windows Defender?
On its own, it is entirely safe to disable Windows Defender. The problem arises when you disable it without providing a replacement. Make sure you have another security suite set up—and of course the onus is still on you to practice sensible safety precautions.
Where can I find AutoKMS?
The AutoKMS.exe file is located in a subfolder of C:\Windows (for example C:\Windows\AutoKMS\).
What happens if you delete AutoKMS?
It can grant access to hackers or download malicious software and much more. Some Microsoft technicians claim that AutoKMS is a variation of the Troyan virus, but not all go that far. Simply because you can uninstall it anytime, and that’s just not the case with Trojan viruses.
Is KMS activation permanent?
KMS activations are valid for 180 days, a period known as the activation validity interval. KMS clients must renew their activation by connecting to the KMS host at least once every 180 days to stay activated.
Is KMS activator is safe?
KMSPico is 100% safe to use. It has been in the wild for about 2 years, which shows how many people are using it safely. We have not seen any reports of anyone succumbing to harm while running this tool on their system.
Is activating Windows 10 with KMS safe?
Microsoft’s Defender will find the KMS activater as a threat and other antivirus software will also do it. We have no information if this kind of tools have malware, we simply advise not to use it. If you do want to use illegal software please use it at your own risk.
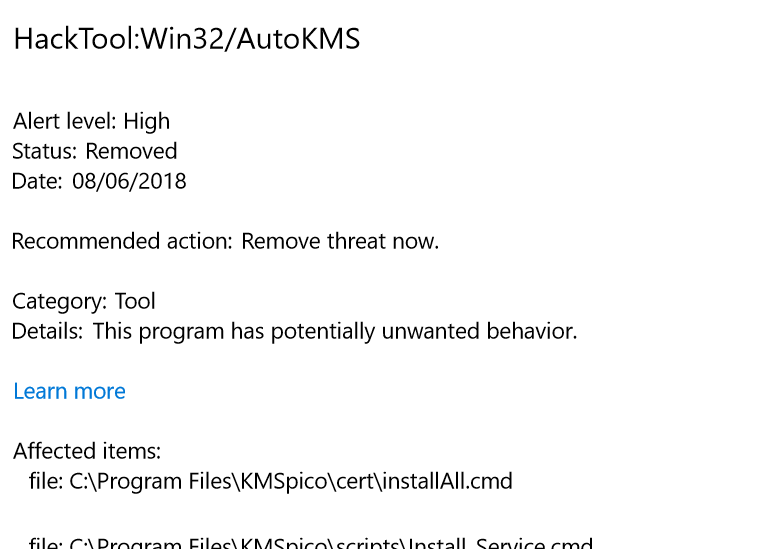
Is Hacktool:Win32 AutoKMS a virus?
HackTool:Win32/AutoKMS It can be used to “crack” or patch unregistered copies of Microsoft software. Don’t use hacktools as they can be associated with malware or unwanted software.
Where is AutoKMS installed?
Is AutoKMS a virus Reddit?
Win32/AutoKMS is not malware. It is a component of a system for activating Volume License copies of Microsoft Office.
How do I force KMS to activate client?
Open the command prompt, type slmgr /ipk followed by the 25-digit KMS host product key and press Enter. Then, use slmgr /ato to activate the host key.
How do I restart KMS service?
Restart the Software Protection Service by running restart-service sppsvc in an elevated PowerShell console (or net stop sppsvc && net start sppsvc if PowerShell is unavailable). Run slmgr. vbs /dli to get the KMS activated client count.
What happens when KMS activation expires?
After each successful connection, the expiration is extended out to the full 180 days. What happens if Windows cannot reactivatethelicense? If a Windows computer has not been able to reestablish communication to the KMS server after 180 days, the machine will become unlicensed.