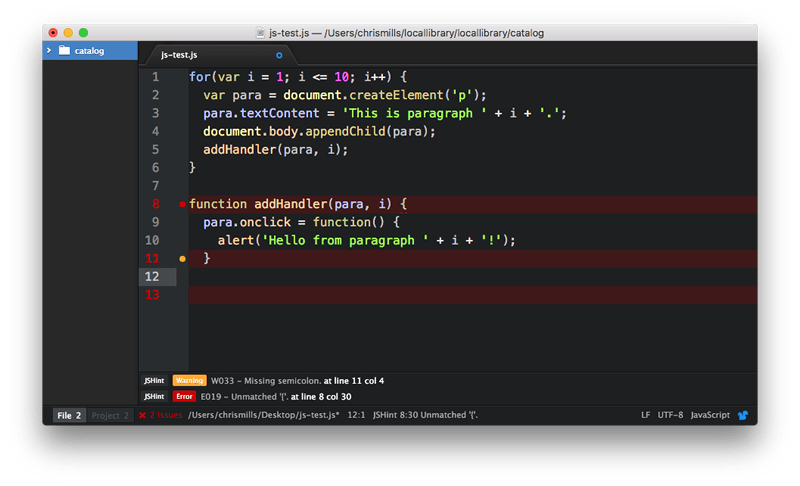
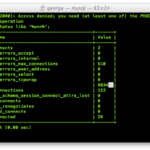
A few bad things Javascript can do: Javascript alone might allow all the information of a poorly written website to be sent to a “bad guy”. This is called XSS / CRSF. It can also cause your logged in account to make changes to websites (editing financial data of a different unrelated site) without you knowing.
Can JavaScript be dangerous?
JavaScript can be dangerous if the proper precautions aren’t taken. It can be used to view or steal personal data even you don’t realize what’s going on. And since JavaScript is so ubiquitous across the web, we’re all vulnerable.
Can you get a virus from JavaScript?
Infected JavaScript files doesn’t need user interaction. They are usually encoded in the links so browsing a website is enough to be hacked. That’s why malicious Javascripts are quite dangerous. There are several ways through which the malicious JavaScripts spread as listed below.
Is JavaScript safe in browser?
From a security perspective, JavaScript is fourth on the list of the most vulnerable languages – only behind Java, PHP, and C. For this reason, developers must remain proactive and defensive in securing their JavaScript applications to keep the web safe.
Can JavaScript be dangerous?
JavaScript can be dangerous if the proper precautions aren’t taken. It can be used to view or steal personal data even you don’t realize what’s going on. And since JavaScript is so ubiquitous across the web, we’re all vulnerable.
Can JavaScript steal passwords?
The scripting language also has many functions which can be used for malicious purposes, including stealing a user’s cookies containing passwords and other information. Cookies are information which a website requests or maintains regarding specific users which visit the page.
What is JavaScript malware?
A JavaScript injection attack is a type of attack in which a threat actor injects malicious code directly into the client-side JavasScript. This allows the threat actor to manipulate the website or web application and collect sensitive data, such as personally identifiable information (PII) or payment information.
Should you allow JavaScript?
Should you enable JavaScript or not? For most users, JavaScript is pretty safe. If you’re doing something that makes you particularly concerned about security, you can turn JavaScript off, then easily turn it back on. But to get the most out of the modern web, it’s best to leave it on.
What is the problem with JavaScript?
These days, most cross-browser JavaScript problems are seen: When poor-quality browser-sniffing code, feature-detection code, and vendor prefix usage block browsers from running code they could otherwise use just fine. When developers make use of new/nascent JavaScript features, modern Web APIs, etc.)
Do antivirus programs detect JavaScript malware?
Antivirus software works by scanning your computer for known threats. Although there are dozens of types of antivirus software, most of them are capable of detecting JavaScript malware. Antivirus software will offer solutions to deal with JavaScript malware.
What happens when I enable JavaScript?
It makes web pages functional for specific purposes and if disabled for some reason, the content or the functionality of the web page can be limited or unavailable. Here you can find instructions on how to enable (activate) JavaScript in five most commonly used browsers. Javascript is enabled in your web browser.
What happens if u block JavaScript?
If you disable JavaScript, you may be unable to use certain features on a website. In other cases, the website may even break completely, or you’ll be stuck using an incredibly old version of the page. For example, Gmail offers a very basic plain HTML mode for people with JavaScript disabled.
What is a JavaScript exploit?
Exploiting JavaScript vulnerabilities can manipulate data, redirect sessions, modify and steal data, and much more. Although JavaScript is typically thought of as a client-side application, JavaScript security issues can create problems on server-side environments as well.
What is Node JS virus?
Discovered by Xavier Mertens, Node. js is a ransomware-type malicious software. This malware encrypts the data of infected devices and demands payment for decryption.
What is JavaScript and why do I need it?
Javascript is used by programmers across the world to create dynamic and interactive web content like applications and browsers. JavaScript is so popular that it’s the most used programming language in the world, used as a client-side programming language by 97.0% of all websites.
How do I scan a website for malware?
Visit the SiteCheck website at sitecheck.sucuri.net and click Scan Website. If the site is infected, review the warning message to look for any payloads and locations. You can click More Details at the top to review the iFrames, links, scripts, and embedded objects to identify unfamiliar or suspicious elements.
Can JavaScript be dangerous?
JavaScript can be dangerous if the proper precautions aren’t taken. It can be used to view or steal personal data even you don’t realize what’s going on. And since JavaScript is so ubiquitous across the web, we’re all vulnerable.
Is it safe to visit a not secure website?
You might see a “Login not secure” or “Payment not secure” message. Dangerous: Avoid this site. If you see a full-page red warning screen, the site has been flagged as unsafe by Safe Browsing. Using the site will likely put your private information at risk.
Can a website steal my information?
Can a website steal your credit card info? The short answer is yes. With phishing, hackers attempt to steal valuable information by impersonating a trusted source. Phishing schemes can come in several different forms, including phone calls, fake websites and sales emails.
Can websites see your passwords?
Website owners can possibly view your password in either of two ways. One, they can watch your keystrokes as you type in the password when signing in to their site; or, if they actually store your password in plain text in their database, they can also view it there.
What is JavaScript and why do I need it?
Javascript is used by programmers across the world to create dynamic and interactive web content like applications and browsers. JavaScript is so popular that it’s the most used programming language in the world, used as a client-side programming language by 97.0% of all websites.
What is a JavaScript exploit?
Exploiting JavaScript vulnerabilities can manipulate data, redirect sessions, modify and steal data, and much more. Although JavaScript is typically thought of as a client-side application, JavaScript security issues can create problems on server-side environments as well.