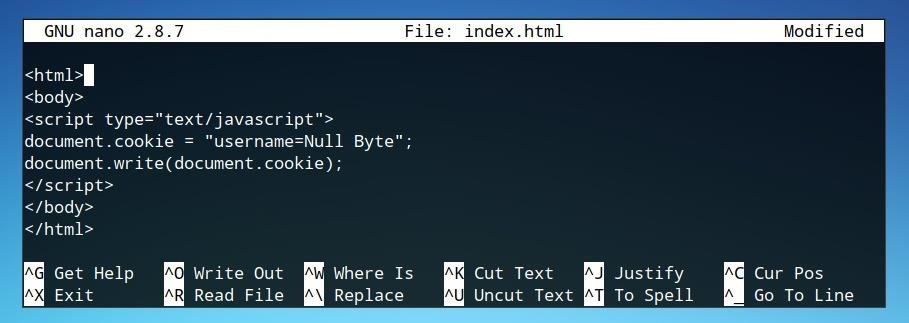
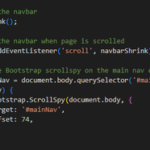
The scripting language also has many functions which can be used for malicious purposes, including stealing a user’s cookies containing passwords and other information. Cookies are information which a website requests or maintains regarding specific users which visit the page.
Can a website steal my saved passwords?
While it may be tempting to click “Remember Password” when your web browser prompts you, doing so puts your security at RISK. If you walk away from your unlocked computer, (even briefly) at work or in public, there is a very real risk that someone could steal your passwords in just a few simple clicks.
Can cookies steal passwords?
Like a phishing attack, cookie hijacking allows a cybercriminal to steal personal information like usernames, passwords, and other important data held within the cookie. If you enter your information while on the fake website, the criminal can then put that cookie in their browser and impersonate you online.
How do hackers know my password?
Another popular way to get hold of your passwords is via malware. Phishing emails are a prime vector for this kind of attack, although you might fall victim by clicking on a malicious advert online (malvertising), or even by visiting a compromised website (drive-by-download).
How could someone get my password?
Sometimes phishing emails contain malicious software, or malware, either in attachments or in embedded links. By downloading the malware to their computer, people increase the likelihood of having a keylogger installed that can then capture their passwords and send it to a hacker.
Why you should not accept cookies?
While most cookies are perfectly safe, some can be used to track you without your consent. Worse, legitimate cookies can sometimes be spied upon if a criminal gets access.
Can I get hacked by accepting cookies?
Cookies are a common technology that allow websites to recognize you. But they can also give hackers enough data to steal your personal information. Search for anything online — and the next thing you know that item is following you on the internet in the form of an ad at just about every website you visit.
Can Chrome passwords be hacked?
Hackers can steal your Google Chrome or Microsoft Edge login password through malware, experts claim. Dangerous malware can steal your Google Chrome or Microsoft Edge login password stored in the browsers. Dangerous malware can steal your Google Chrome or Microsoft Edge login password stored in the browsers.
How do I save a password that is not secure?
In the address bar type in: ‘chrome://flags/#enable-password-force-saving’, then press “Enter.” Choose “Enabled” from the drop-down menu under the “Force-saving of passwords” option. Navigate to the bottom right of the page and click the blue “Relaunch” button. Now re-open your Chrome browser.
Can a website steal your data?
Hackers illegally access devices or websites to steal peoples’ personal information, which they use to commit the crimes like theft. Many people shop, bank, and pay bills online. People also store financial information, like credit card or bank account numbers, on their devices.
Can you get hacked by visiting a website on Iphone?
iPhones can get hacked from websites, which is why it’s best to use antivirus software to scan for malicious sites.
Do websites store passwords?
As discussed in that earlier article, websites do not (or, rather, should not), keep a record of your password. Instead, they “hash” the string of characters you provide as your password, and store that hash instead. When you log in, they hash the password you type in and compare the result with the hash they stored.
Is it safe to visit a not secure website?
You might see a “Login not secure” or “Payment not secure” message. Dangerous: Avoid this site. If you see a full-page red warning screen, the site has been flagged as unsafe by Safe Browsing. Using the site will likely put your private information at risk.
Can hackers see you through your phone camera?
On top of that, popular app developers aren’t immune to accusations of watching you through your phone’s camera. Generally, however, a stalker would need to install spyware on your device in order to compromise it. Hackers can gain access to your phone physically, through apps, media files, and even emojis.
Can hackers see through your camera?
Are hackers really spying on people through their phone cameras and webcams? The short answer: Yes. Webcams and phone cameras can be hacked, giving bad actors complete control over how they function. As a result, hackers can use a device’s camera to both spy on individuals and search for personal information.
Can malware get your passwords?
Spyware. Spyware is a spy malware that monitors everything you see and does on your device. Its job is to steal data and passwords from its victims, allowing the cybercriminal access to all kinds of accounts, including email.
Can someone hack your email without a password?
As Garry Brownrigg, CEO & Founder of QuickSilk, explains, “They can ‘spoof’ an email message with a forged sender address – they don’t even need your password for this.” The things they send can be anything from harmful malware to scams and requests for money; either way, you’d certainly rather they didn’t come from …
What happens when you reject all cookies?
Accepting cookies will give you the best user experience on the website, while declining cookies could potentially interfere with your use of the site. For example, online shopping. Cookies enable the site to keep track of all of the items that you’ve placed in your cart while you continue to browse.
What happens if I reject cookies?
Most cookies are really not an issue. They are just used by the website owner so you have a better experience with the site. You can decline the “Accept Cookies” message and most websites will work just fine. Of course, any personalization will not be available to you.
What happens if you block all cookies?
Here are some examples of what happens if you block all cookies: You may not be able to automatically sign in to a site because your saved username and password is deleted. Some web pages or features won’t function. You may see a message on websites asking you to enable cookies for it to load.
What is cookie stealer?
Cookie theft occurs when a third party copies unencrypted session data and uses it to impersonate the real user. Cookie theft most often occurs when a user accesses trusted sites over an unprotected or public Wi-Fi network.
What are JavaScript cookies?
Cookies are data, stored in small text files, on your computer. When a web server has sent a web page to a browser, the connection is shut down, and the server forgets everything about the user.