Malware can go undetected for extended periods of time. Many users are only aware of a malware attack if they receive an antimalware alert, see pop-up ads, are redirected to malicious websites, or experience slow computer speeds or frequent crashes. Malware exploits devices to benefit threat actors.
Can malware go undetected by Malwarebytes?
While these examples are simple to spot, other attacks go largely unnoticed—because it’s easy for malware to hide among lines of legitimate code. Can malware go undetected? The answer is yes—and it often does.
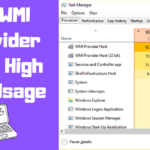
Can malware hide from Task Manager?
Summing Up. Task Manager can be a helpful tool for detecting malicious programs on your system. However, some malware is designed to evade detection by the Task Manager. As you can see, there are various ways that malware can hide from the task manager.prieš 1 dieną
Can antivirus detect Trojan?
An effective antivirus program searches for valid trust and app behavior, as well as trojan signatures in files in order to detect, isolate and then promptly remove them.
Can virus hide from antivirus Scan?
Typically, a stealth virus can hide in the legitimate files, partitions or boot sectors of a computing device without alerting the antivirus software or notifying the user of its presence.
How often does malware happen?
560,000 new pieces of malware are detected every day. There are now more than 1 billion malware programs out there. Every minute, four companies fall victim to ransomware attacks. Trojans account for 58% of all computer malware.
Can antivirus remove malware?
Antivirus software is designed primarily to prevent infection, but also includes the ability to remove malware from an infected computer.
What is the most difficult virus to detect?
Metamorphic viruses are one of the most difficult types of viruses to detect. Such viruses change their internal structure, which provides an effective means of evading signature detection.
Can ransomware be undetected?
Detection By Abnormal Traffic Monitoring file operations is an endpoint-level form of behavior-based threat detection. However, ransomware can also be detected at the network level by looking for anomalous traffic that may indicate a ransomware infection or malware in general.
Does Malwarebytes really work?
Yes, Malwarebytes is safe. It has a decent antivirus scanner, real-time protection that offers multiple layers of protection against malware, system vulnerabilities, and online threats, and a browser extension that provides additional protection against phishing and malicious sites.
How do I see if my Task Manager has a virus?
If you’re curious about whether a specific program is malicious, right-click it in the Task Manager and select “Search Online” to find more information. If information about malware appears when you search the process, that’s a sign you likely have malware.
Is Windows Defender better than McAfee?
The Smart Firewall, Wi-Fi scanner, VPN, and anti-phishing protections are all significantly better than Microsoft’s built-in tools. And the addition of system optimization and personal data cleanup tools, as well as excellent identity theft features, makes McAfee a much better alternative to Windows Defender.
How do I find hidden processes in Task Manager?
Right-click the Windows icon or press the Win and X keys at the same time. In the displayed window, click Task Manager. If the Task manager is opened for the first time and the Processes tab is hidden, click More details. The Processes tab and other tabs will be displayed.
What’s the difference between malware and virus?
Often used interchangeably, the terms malware and virus have two distinct meanings. Malware, or malicious software, is an overarching term used to describe any program or code that is created with the intent to do harm to a computer, network or server. A virus, on the other hand, is a type of malware.
Will Malwarebytes remove viruses?
Scan and remove viruses and malware free. Malwarebytes free antivirus includes multiple layers of malware-crushing tech. Our anti-malware finds and removes threats like viruses, ransomware, spyware, adware, and Trojans.
What are the most common ways to be infected by a computer virus?
Methods of Malware and Virus Infection and Spread Downloading infected files as email attachments, from websites or through filesharing activities. Clicking on links to malicious websites in emails, messaging apps or social network posts.
Does factory reset remove Trojans?
In short, yes, a factory reset will usually remove viruses … but (there’s always a ‘but’ isn’t there?) not always. Due to the wide variety and ever-evolving nature of computer viruses, it’s impossible to say for sure that a factory reset will be the answer to curing your device from malware infection.
Can Windows Defender remove Trojan?
Windows Defender comes packed with the Windows 10 update and offers top-notch antimalware protection to keep your device and data safe. Although, Windows Defender is not capable of handling all kinds of viruses, malware, trojan, and other security threats.
How do Trojans avoid detection?
The trojan uses Alternate Data Stream (ADS) as a technique to run follow-up malware. The configuration scripts used during the infection process are obfuscated in an attempt to evade detection. The use of ADS, in particular, represents a serious ongoing threat, as it can easily hide follow-up malware.
Can malware hide from Windows Defender?
It is called Windows Defender. But sometimes, malware can outsmart Windows Defender by hiding within Windows while the operating system is running. To remove the more clever and devious malware, like rootkits, out in the wild you may have to run Windows Defender in offline mode.
How big is malware usually?
Can you get virus without downloading anything?
Yes, you can get a virus just from visiting a website. These days, it’s very easy to be overconfident in our abilities to avoid computer viruses. After all, many of us were told that we simply had to avoid files and programs we didn’t recognize. If an email came through that looked fishy, we didn’t open them.