Answer: A: Answer: A: They can not access your phone, but if they have the credentials for you iCloud account, they could access anything stored in or synced to iCloud, including iMessages, photos, etc. Change your password and set up 2 factor authentication if you suspect someone may have your credentials.
Can someone connect to my iPhone without me knowing?
If your iPhone backs everything up to your iCloud account, then someone can spy on your activity by accessing your iCloud account from any web browser. They would need your Apple ID username and password in order to do this, so if you know that a third party has that information, there are a few steps you should take.
How do you check if my iPhone is linked to another device?
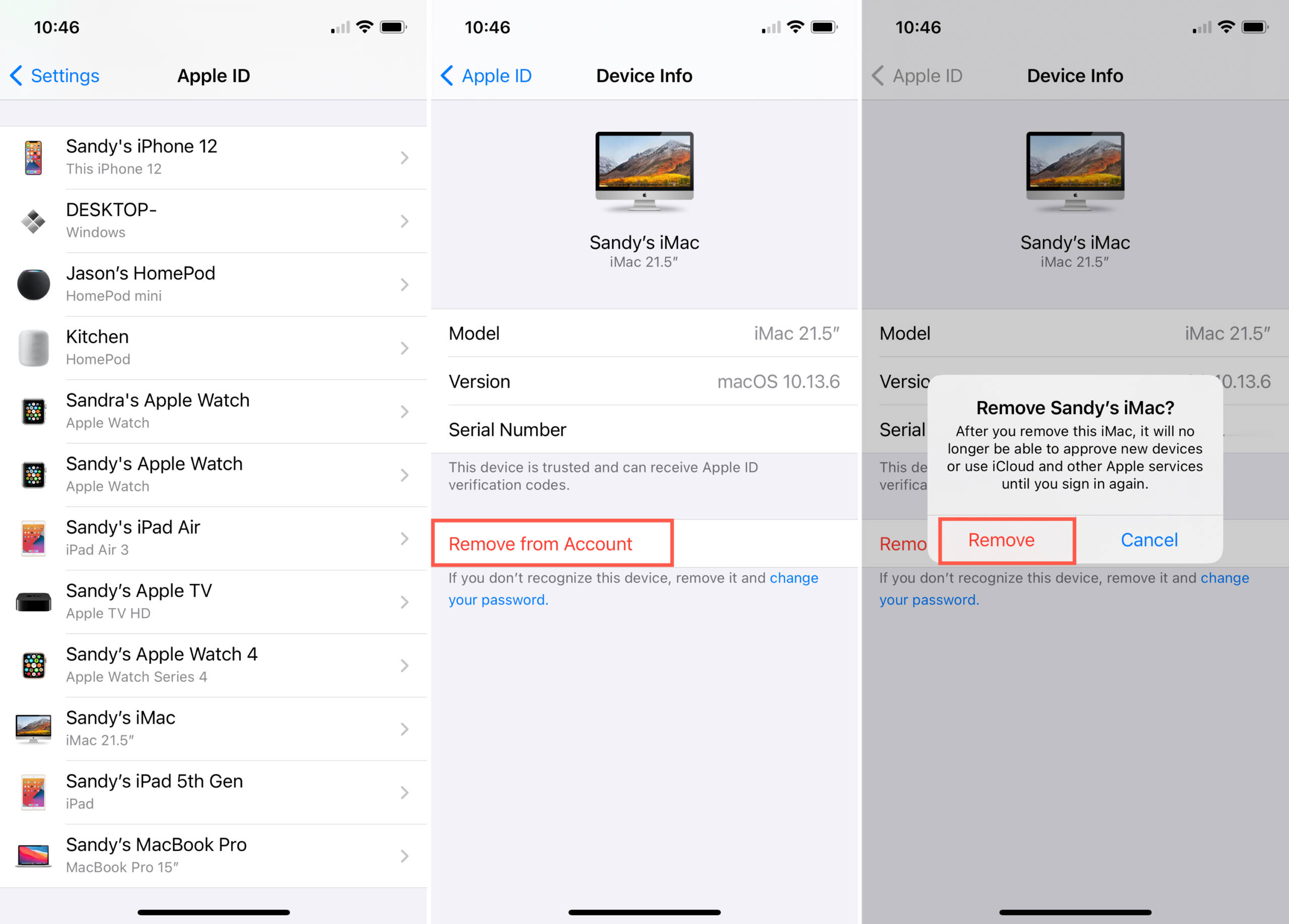
Sign in to the Apple ID website (https://appleid.apple.com) and review all the personal and security information in your account to see if there is any information that someone else has added. If you have two-factor authentication turned on, review trusted devices for any devices that you don’t recognize.
Can someone monitor your iPhone remotely?
Yes, a partner, parent, or even employer can gain remote, real-time access to your iPhone using spying software. Spyware can track your GPS location, record your keypad inputs such as credit card numbers and passwords, and monitor your calls, texts, app usage, emails, voice, and other personal data.
Can I control an iPhone from another iPhone?
Select Device. Select Use Other Device. Select the device that you want to control, then select Connect. Now you can use the switch connected to your iPhone, iPad, or iPod touch to control the other device.
How do you check if my iPhone is linked to another device?
Sign in to the Apple ID website (https://appleid.apple.com) and review all the personal and security information in your account to see if there is any information that someone else has added. If you have two-factor authentication turned on, review trusted devices for any devices that you don’t recognize.
Can someone log into your iCloud and see your messages?
Answer: A: Yes. If they can login to your iCloud then they have the exact same access as you do. iCloud has no way of knowing who is using the AppleID and signing in.
How do I know if my iCloud is on another device?
See your devices On iCloud.com, go to Account Settings. In the My Devices section, select a device in the list. Note: If one of your devices isn’t listed, make sure you’re signed in on the device with your Apple ID.
How can you tell if your phone is being monitored by someone else?
Flashing of a blue or red screen, automated settings, unresponsive device, etc. could be some signs that you can keep a check on. Background noise while making calls – Some of the spying apps can record the calls made on the phone. To be sure, listen carefully while making a call.
How can I find out who’s monitoring my iPhone?
There is absolutely no way to know if anyone is tracking you using Find my iPhone. The ONLY way someone can track you is if they know your Apple ID and password, so if you suspect someone is tracking you simply change your password and they won’t be able to.
Can an iPhone be jailbroken remotely?
Is it possible to hack an iPhone remotely? It might surprise you, but yes, it is possible to remotely hack an iOS device.
Can iPhone be a mirror?
Answer: A: While one iPhone cannot mirror another, 2 iPhones that share an Apple ID can both see anything that either phone syncs to iCloud. So the takeaway is NEVER share an Apple ID between different people.
What happens when you pair two iPhones?
Question: Q: what happens when pair two iPhones Answer: A: Answer: A: You don’t really “pair” iOS devices to each other so much as sync them both to iCloud/iTunes etc. If you want to send content between 2 iOS devices, iCloud is effective as is AirDrop.
Can someone link their phone to yours without you knowing?
It’s even possible for someone to monitor your cell phone’s activity without ever even touching it. Mobile spyware, sometimes called stalkerware, can be installed onto your phone to monitor information such as calls, text messages, emails, location, photos, and browsing history.
Can someone read my iMessages from another phone?
Unless someone is still logged into your Apple ID on their device, they can’t read your iMessages or text messages. If you’re concerned, change your Apple ID password and disable iMessage on the other devices.
Can someone log into your iCloud and see your messages?
Answer: A: Yes. If they can login to your iCloud then they have the exact same access as you do. iCloud has no way of knowing who is using the AppleID and signing in.
What does unknown accessory detected near you mean on iPhone?
If your iPhone has been close to an unfamiliar AirTag or other accessory for a prolonged period of time, you may receive a notification on the Find My application stating, “Item Detected Near You.” Tap this message and it will allow you to play a sound on the AirTag in order to find it.
How do you check if my iPhone is linked to another device?
Sign in to the Apple ID website (https://appleid.apple.com) and review all the personal and security information in your account to see if there is any information that someone else has added. If you have two-factor authentication turned on, review trusted devices for any devices that you don’t recognize.
Is there a way to Unhack your phone?
If you’ve recently sideloaded apps on Android, they might be to blame for the hack. Therefore, to unhack your phone, delete all recently-downloaded apps from it. Also, make sure you carefully examine your apps and search on Google for the ones you don’t remember installing.
Can you check to see if your phone is hacked?
Use the code *#21# to see if hackers track your phone with malicious intent. You can also use this code to verify if your calls, messages, or other data are being diverted. It also shows your diverted information’s status and the number to which the information is transferred.
What can a hacker see on your phone?
Hackers can use keyloggers and other tracking software to capture your phone’s keystrokes and record what you type, such as search entries, login credentials, passwords, credit card details, and other sensitive information.
How do I block my phone from being tracked?
On Android: Open the App Drawer, go into Settings, select Location, and then enter Google Location Settings. Here, you can turn off Location Reporting and Location History.