Signs your Apple ID has been compromised You receive an email or notification that your Apple ID was used to sign in to a device you don’t recognize or did not sign in to recently (for example, “Your Apple ID was used to sign in to iCloud on a Windows PC”).
Can someone else get into my iCloud?
If someone knew your Apple ID or your iCloud username/password, they might be able to access your data and information. Some security and privacy measures include determining what of your information you want to be accessible from in the cloud or changing the password to your iCloud account.
Can someone use my Apple ID without me knowing?
iPhone security tips Someone else knows your password and can sign in with your Apple ID. It is not safe to share your Apple ID, even with family members. You don’t have access to the email address or phone number associated with your Apple ID. You click malicious links and enter your credentials.
Can someone else get into my iCloud?
If someone knew your Apple ID or your iCloud username/password, they might be able to access your data and information. Some security and privacy measures include determining what of your information you want to be accessible from in the cloud or changing the password to your iCloud account.
How do I know if someone is logged into my iCloud?
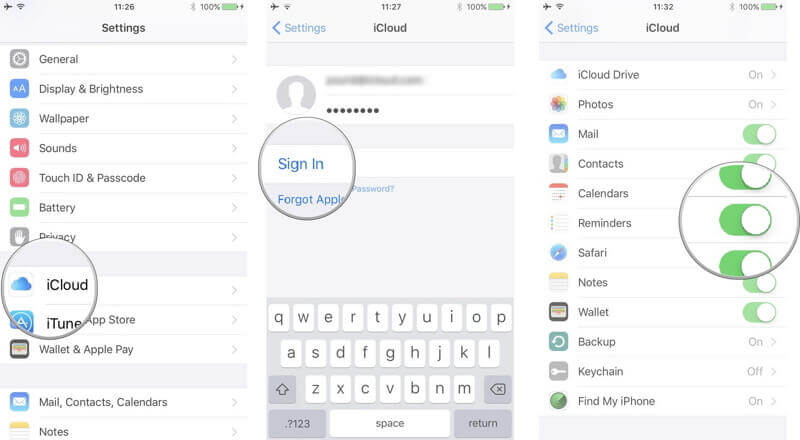
From the Devices section of your Apple ID account page, you can see all of the devices that you’re currently signed in to with your Apple ID, including Android devices, consoles, and smart TVs: Sign in to appleid.apple.com,* then select Devices.
How do I know if someone is using my iCloud?
Go to appleid.apple.com and sign in to your Apple ID. Look at the Devices section. Click on Details. You will see all the devices signed in with your Apple ID.
What does it mean when someone is trying to log into your Apple ID?
If someone you don’t know or don’t trust can sign in with your Apple ID, your account is not secure. Your Apple ID might not be secure for the following reasons: Someone else created an Apple ID on your behalf, or you’re using an Apple ID that was already signed in when you received your device.
Is iCloud safe from hackers?
iCloud is Extremely Secure “Data stored in the iCloud is encrypted so a hacker needs a key to access it. Meaning to say: this storage system is extremely secured.”
Can someone access my iPhone from another device?
Answer: A: Answer: A: They can not access your phone, but if they have the credentials for you iCloud account, they could access anything stored in or synced to iCloud, including iMessages, photos, etc. Change your password and set up 2 factor authentication if you suspect someone may have your credentials.
What does it mean when someone is trying to log into your Apple ID?
If someone you don’t know or don’t trust can sign in with your Apple ID, your account is not secure. Your Apple ID might not be secure for the following reasons: Someone else created an Apple ID on your behalf, or you’re using an Apple ID that was already signed in when you received your device.
Can anyone see iCloud photos?
Photos need to be actually shared through that album to be visible to other members of the family group however. So unless you actually share you photos, they cannot be seen by anybody else.
Can someone see my pictures if they use my Apple ID on another device?
Yes. If you give somebody else the details of your Apple ID and its password they can poke around in any data stored in the cloud and make purchases on your account. This is not a sensible idea.
Can someone else get into my iCloud?
If someone knew your Apple ID or your iCloud username/password, they might be able to access your data and information. Some security and privacy measures include determining what of your information you want to be accessible from in the cloud or changing the password to your iCloud account.
Can someone access my iPhone from another device?
Answer: A: Answer: A: They can not access your phone, but if they have the credentials for you iCloud account, they could access anything stored in or synced to iCloud, including iMessages, photos, etc. Change your password and set up 2 factor authentication if you suspect someone may have your credentials.
What if my Apple ID is being used on another device?
Question: Q: apple id was being used on another device Answer: A: Answer: A: Go to https://appleid.apple.com/ and change your AppleID password. Also see If you think your Apple ID has been compromised – Apple Support and follow the suggestions there to enhance the security of your AppleID.
Can you see messages on iCloud?
Any messages currently stored in iCloud are now accessible on your device, and any new messages you receive on your device will be stored in iCloud.
Can someone see my pictures if they use my Apple ID on another device?
Yes. If you give somebody else the details of your Apple ID and its password they can poke around in any data stored in the cloud and make purchases on your account. This is not a sensible idea.
How do I find out who is using my Apple ID?
Via the Apple ID website: Go to appleid.apple.com, click Sign In, and log in with your credentials. Click Devices in the left-hand menu bar. In iOS/iPadOS: Go to Settings > Account Name and swipe down until you see your devices.
Why does my iPhone say I’m logged in a different location?
If the IP address of your device used to log in is seen as being in another location, that message appears. These login attempts that show up are actually just you signing on and your ISP routing the traffic through servers that aren’t near you.
Why is my Apple ID saying I’m in a different location?
The reason your other device shows some strange location in the pop-up message is that the location shown is not actually your device’s location. It is an approximation of the address of your device’s ‘IP Address’.
Can someone hack your iPhone and see everything you do?
Despite this security, it’s still possible for hackers to access your iPhone through phishing links, third-party apps, or unsecured WiFi. If your iPhone is jailbroken, you no longer have Apple’s “sandbox” security measures which puts you at even greater risk of hacking.
Is there a way to Unhack your phone?
If you’ve recently sideloaded apps on Android, they might be to blame for the hack. Therefore, to unhack your phone, delete all recently-downloaded apps from it. Also, make sure you carefully examine your apps and search on Google for the ones you don’t remember installing.