According to the FBI’s “Lawful Access” guide, if served with a court order or a search warrant, Apple must hand over basic subscriber information as well as 25 days’ worth of data about queries made in iMessage, such as what a targeted user looked up in iMessage and also which other people searched for that targeted …
Can the government look at iMessage?
According to the FBI’s “Lawful Access” guide, if served with a court order or a search warrant, Apple must hand over basic subscriber information as well as 25 days’ worth of data about queries made in iMessage, such as what a targeted user looked up in iMessage and also which other people searched for that targeted …
Can the government see Iphone messages?
A DEA report obtained by CNet has revealed that law enforcement has been stumped by communications sent over Apple’s encrypted iMessage system. It turns out that encryption is only half the problem, and it’s really legislation that keeps iMessages invisible to law enforcement.
Can FBI read your iMessage?
Can iMessage be traced by police?
Law enforcement can retrieve messages via Google / iCloud backups. The chart shows that subpoenas will not grant access to message content for six of the nine secure messaging apps. The three that do give up “limited” content are iMessage, Line and WhatsApp.
Can the government see Iphone messages?
A DEA report obtained by CNet has revealed that law enforcement has been stumped by communications sent over Apple’s encrypted iMessage system. It turns out that encryption is only half the problem, and it’s really legislation that keeps iMessages invisible to law enforcement.
Can police recover deleted iMessages?
Keeping Your Data Secure So, can police recover deleted pictures, texts, and files from a phone? The answer is yes—by using special tools, they can find data that hasn’t been overwritten yet. However, by using encryption methods, you can ensure your data is kept private, even after deletion.
Can iMessages be retrieved for court?
This is not a common occurrence, so, in short, the answer is, yes, text messages can be subpoenaed, but, no, they are not frequently used as evidence for the reasons above. Text messages can fall into the murky area of ‘hearsay evidence,’ which is inadmissible in court.
Are my iMessages private?
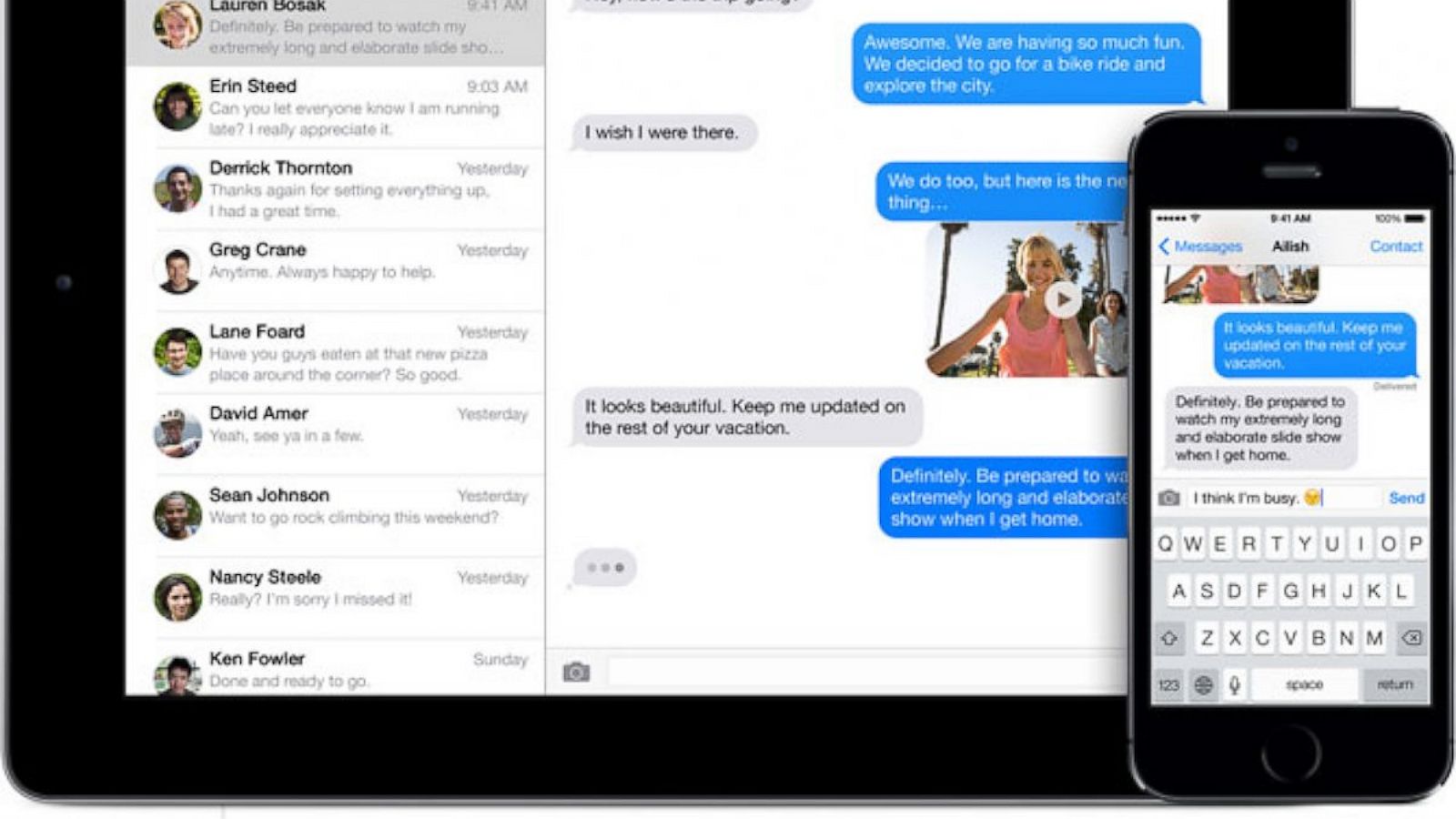
Apple’s iMessage for iPhone, iPad, and Mac always uses end-to-end encryption. Only the sender and receiver of the messages can see their contents. Photos, videos, and other file attachments are also encrypted. What’s more, Apple’s FaceTime service also uses end-to-end encryption for voice and video calls, too.
Who can see your iMessages?
Text messages are sent through the cell network, and are not shared via Family Sharing. The only device that will be able to see the text messages is the one that has the SIM for that text message’s originator/receiver.
How long are iMessages saved for?
For example, on an Apple device, you can choose to keep messages for 30 days, 1 year or forever.
Can feds tap iMessage?
A recently discovered FBI training document shows that US law enforcement can gain limited access to the content of encrypted messages from secure messaging services like iMessage, Line, and WhatsApp, but not to messages sent via Signal, Telegram, Threema, Viber, WeChat, or Wickr.
Can feds see your FaceTime?
§2703(d), or court order with the equivalent legal standard, or search warrant. FaceTime communications are end-to-end encrypted and Apple has no way to decrypt FaceTime data when it is in transit between devices. Apple cannot intercept FaceTime communications.
Can the government see encrypted messages?
The FBI training document reveals that the government agencies can obtain access to the encrypted message content and other details from secure messaging solutions like WhatsApp, WeChat, Viber, iMessage, Line, Telegram, Wickr, and Threema.
Does Apple keep a record of iMessages?
Apple may record and store some information related to your use of the Messages app and the iMessage service to operate and improve Apple’s products and services: Apple may store information about your use of iMessage in a way that doesn’t identify you.
Do iMessages show up in phone records?
Question: Q: Can I messages be seen on phone bills Answer: A: No, iMessages don’t show on your bill. They are sent as data.
Can the Feds tap your iPhone?
Federal agents cannot legally tap your phone whenever they want to. They have to follow strict guidelines and go through a specific process to obtain approval.
Can the government see my text messages?
Unfortunately, the government continues to take advantage of an outdated law to read Americans’ private electronic communications without a warrant. Under the law, the government does need a warrant to access the content of electronic communications that are 180 days old or less, but doesn’t need one for older emails.
Who can access my iMessages?
They can only view this information if they are logged into your account on their iDevice. For example, an iPhone, iPad and MacBook all on the same account will receive all messages sent or received from the other machines (barring a lack of network connectivity). My suggestion to you is to change your password.
Can the government watch your FaceTime?
§2703(d), or court order with the equivalent legal standard, or search warrant. FaceTime communications are end-to-end encrypted and Apple has no way to decrypt FaceTime data when it is in transit between devices.
Can the Feds tap your iPhone?
Federal agents cannot legally tap your phone whenever they want to. They have to follow strict guidelines and go through a specific process to obtain approval.
Can the government see Iphone messages?
A DEA report obtained by CNet has revealed that law enforcement has been stumped by communications sent over Apple’s encrypted iMessage system. It turns out that encryption is only half the problem, and it’s really legislation that keeps iMessages invisible to law enforcement.