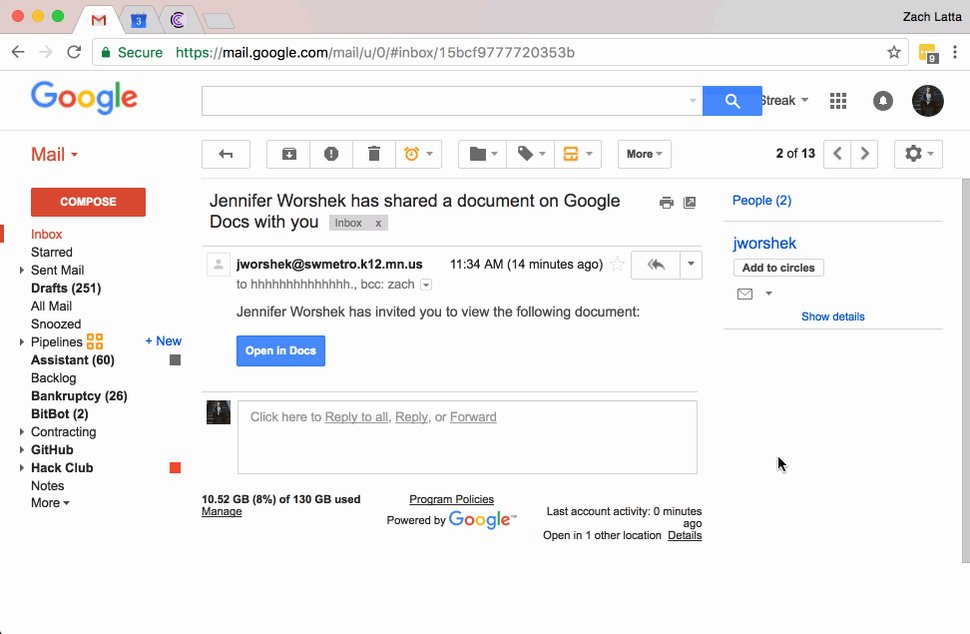
Attackers are exploiting Google Docs to conduct phishing and inject malware. Last October, Avanan reported that hackers could easily send malicious links through comments in Google apps like Docs and Slides. This known vulnerability has not been fully closed or mitigated by Google since then.
Can you get hacked by a Google Doc?
A new report from Avanan has found that cybercriminals are attempting to exploit Google Docs through its comment feature.
How safe is using Google Docs?
Your content is stored securely When you create a file on Google Docs, Sheets, & Slides and share it, it is stored securely in our world-class data centers. Data is encrypted in-transit and at-rest. If you choose to access these files offline, we store this info on your device.
Can you get virus from Google Docs?
This news might be shocking to many but it is an unfortunate truth. Security researchers have discovered malware that can not only manipulate Google Docs but also attack computer systems of the users who have trusted Google with their document, spreadsheet and other file management.
How do I secure my Google Docs?
Click on ‘File’, and then ‘Info’. There, you’ll see a drop-down ‘Protect Document’. Click on it and choose ‘Encrypt with Password’.
Is it safe to open Google Docs link?
If you have been wondering about “Can a Google Drive link be dangerous“. The answer is yes. According to the latest reports, hackers are using Google Drive and Google Docs platforms to deceive users into clicking a shared link to a fraudulent credential-stealing site.
Does Google own your docs?
Google Drive allows you to upload, submit, store, send and receive content. As described in the Google Terms of Service, your content remains yours. We do not claim ownership in any of your content, including any text, data, information, and files that you upload, share, or store in your Drive account.
Can someone access my Google Drive?
To help ensure your Google Drive files are private: Anyone who uses the computer could access your files.
Can Google Photos Be Hacked?
A couple of years ago, an independent security expert discovered a Google Photos bug that allowed hackers access to your personal information. Hackers were able to exploit a Google Photos defect to access the photos’ location, date, and user information.
What is Google Docs phishing?
The operators behind a recent phishing campaign are exploiting the commenting feature in Google Docs to send seemingly legitimate emails that convince targets to click malicious links.
Can Google Forms be a virus?
A Google form is a page hosted by Google to collect information from sources in text boxes, radio buttons etc. We cannot say that it is 100% secure but it is highly unlikely that you will get infected via a Google form unless it happens to include a link to a malware and you actively click on it.
Is Google Docs a safe place to store passwords?
Google Docs, Sheets, and Slides documents may not have an option for individual password protection, but they are still protected on Google’s servers. Unless you’ve shared them, other users can’t see your files without your Google Account username and password.
You can use password protection for a Google Drive folder as long as you were the user who created the files. However, you can’t encrypt a Google Drive folder, although individual documents can be encrypted. The owner can control permissions and grant them to users with whom the files are shared.
Can you put a password on a Google Doc?
Password Protect for Google Documents™ – Google Workspace Marketplace. It allows you to create a password pretected document for Google Documents™. You can share this file with others directly.
What can people see when you share a Google Doc?
Google Docs keeps a history of all edits made to a document. But when users edit the document through public sharing, their identity remains anonymous, regardless of whether they’ve signed in to their Google Account or not.
How do I know if I’m Anonymous on Google Docs?
If you share or open a file with a link, you may not see the names of people who view it. People you didn’t invite individually will show as anonymous animals when they’re in the file. People you invite individually will show by name when they’re in the file.
Are Google Docs searchable?
And as you’d expect from any good Word processor, a Google Doc is also easy to search. With a few clicks (or taps if you’re on mobile) you can find any word or term in the document, and if you’d like, you can replace it in one or every instance in which it appears.
Which is more secure Google Drive or OneDrive?
Instead of end-to-end encryption, Google Drive supports AES 128-bit encryption when files are at rest and SSL/TLS 256-bit encryption for files in transit. That means more stringent security measures are used when files are uploaded. OneDrive supports AES 265-bit encryption, both when files are in transit or at rest.
Who can see what’s in my Google Drive?
The files and folders in your Google Drive are private by default until you decide to share them. You can share your documents with specific people or you can make them public and anyone on the Internet can view the shared files.
Who owns a Google Doc?
Click the drop-down arrow next to the person who you want to make the new owner and select Make Owner. Click Yes to confirm this permanent change. That person immediately becomes the owner of the document. Your permission will change to Editor, unless the new owner changes it to something else.
How secure is Google Forms?
Since Google Forms are protected by TLS, the contents of data submitted to forms can’t be checked without the use of a web proxy, and the traffic otherwise looks like legitimate communications to a Google application. Google Forms abuse comes in a variety of forms.
How can I tell who has access to my Google Drive?
How to Check Who Has Access to a Google Drive File. To check the list of people who can see your file, right-click the file in question and click Share. A window will appear showing you all the people who have access to your file. If you haven’t shared it with anyone, you’ll only see yourself on the list.