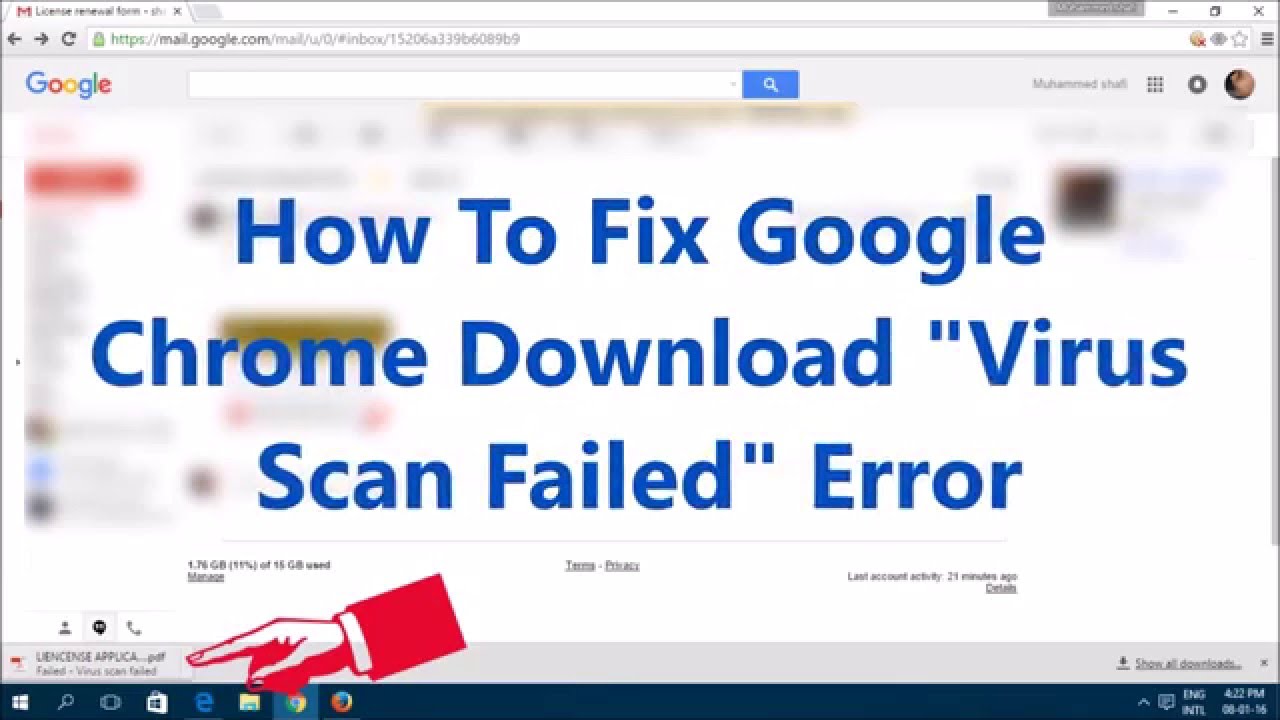
Google Chrome offers a built-in antivirus scanner that comes with the browser. You can the antivirus scanner to search your device for programs that might be harmful. Here’s how to run Chrome’s Antivirus Scanner: Open Chrome on your device.
Can you scan Google Chrome for malware?
To run a scan, you need to open Chrome’s settings. To do so, click on the triple-dot icon in the top-right corner, then click “Settings”. Once in the settings, you should run a quick “Safety check”, to do so, click on “Check now” in the “Safety check” subsection, which is third from the top.
Does Google Chrome need antivirus?
Yes, Google Chromebooks need antivirus protection. While they come with some in-built antivirus features, the protection provided isn’t foolproof. You can download a malicious app from the Google Play Store or fall victim to an online scam or phishing site.
Are virus warnings from Chrome real?
“Google Chrome Warning Alert” is a fake error message displayed by a malicious website that users often visit inadvertently – they are redirected by various potentially unwanted programs (PUPs) that infiltrate systems without consent.
Can you scan Google Chrome for malware?
To run a scan, you need to open Chrome’s settings. To do so, click on the triple-dot icon in the top-right corner, then click “Settings”. Once in the settings, you should run a quick “Safety check”, to do so, click on “Check now” in the “Safety check” subsection, which is third from the top.
Can Google Chrome be infected?
Google Chrome includes a feature to synchronize your browser data between computers, including web browser extensions. This is a convenient feature, but when malware infects your Google Chrome browser, it can hitch a ride on the sync data and become difficult to remove with anti-virus programs.
Does uninstalling Chrome remove malware?
When you uninstall and reinstall Chrome, the moment you login to your Google account again, Google will faithfully restore your cloud backup which ends up reinstalling the malware. To fix this, you need to wipe your Chrome sync data. That will delete all the cloud backups, including hopefully the malware.
How long does Google Chrome take to check for harmful software?
Chrome generally takes two to five minutes to check for harmful software. You can speed up the process by clearing your cache first. If the CleanUp Tool detects any suspicious programs or extensions, it will prompt you to remove them.
Which antivirus is used by Google?
For example, in addition to its own technology for protecting against malicious links, Google also uses Microsoft’s Windows Defender antivirus scanner to protect users from phishing attacks.
How do I enable antivirus on Chrome?
Press Windows + S, type “firewall” in the dialogue box and open the application. Once in Firewall settings, click on “Allow an app or feature through Windows Defender Firewall”.
How can you tell a fake virus warning?
The Federal Trade Commission (FTC) warns that the scareware scam has many variations, but there are some telltale signs: You may get ads that promise to “delete viruses or spyware,” “protect privacy,” “improve computer function,” “remove harmful files,” or “clean your registry.”
Why is Chrome giving me a security warning?
If you get this message, Chrome thinks that the web address may be for a different site than the one you expected. The message may also say “Is this the right site?” or “Fake site ahead.” You get this message when the site you try to visit: Appears similar to a safe site you usually visit.
How do I get rid of malware on Chrome?
To get rid of a browser hijacker in Chrome, you’ll need to reset browser settings, uninstall unwanted and suspicious applications from your device, and remove unwanted and malicious browser extensions.
Will uninstalling Chrome remove malware?
When you uninstall and reinstall Chrome, the moment you login to your Google account again, Google will faithfully restore your cloud backup which ends up reinstalling the malware. To fix this, you need to wipe your Chrome sync data. That will delete all the cloud backups, including hopefully the malware.
How long does Google Chrome take to check for harmful software?
Chrome generally takes two to five minutes to check for harmful software. You can speed up the process by clearing your cache first. If the CleanUp Tool detects any suspicious programs or extensions, it will prompt you to remove them.
Can you scan Google Chrome for malware?
To run a scan, you need to open Chrome’s settings. To do so, click on the triple-dot icon in the top-right corner, then click “Settings”. Once in the settings, you should run a quick “Safety check”, to do so, click on “Check now” in the “Safety check” subsection, which is third from the top.
Does Google have a free antivirus?
Does Google have a free antivirus? Yes, it does.
What is Chrome virus?
What Is the Chromium Virus? The Chromium virus is a malicious web browser that is created using the Chromium code. It is able to overwrite the Chrome browser and replace the original shortcuts with fake ones.
What does Google Chrome Cleanup tool do?
The Chrome Cleanup tool periodically checks for suspicious programs. It lets you know when something untoward is discovered and offers the option to remove it.
Can your Google Account get a virus?
Users who download Gooligan-infected apps or click links in phishing messages are being exposed to the malware, which allows attackers to access sensitive information from Google apps like Gmail, Drive, and Photos.
Why is there a yellow dot on my Chrome icon?
At their core, Android O’s notification dots represent an expanded system for delivering notifications. As the name suggests, the feature causes a dot to appear in the upper-right corner of an app’s icon on your home screen whenever that app has a notification pending.
Is Google clean up good?
It’s 100% safe to download, install and use Chrome Cleanup Tool on Windows 10 and other editions, including Windows 7. It’s a legitimate software product created by Google to find and detect harmful software that prevents you from fully experiencing the Chrome web browser.