G oogle has announced that Google Chrome has been successfully hacked as it discovers 30 security flaws–seven of which pose a “high” threat to users. In a blog post, Google revealed that a new update will make improvements for Windows, Mac, and Linux, to fix the security issues after the hack.
Can Chrome browser be hacked?
G oogle has announced that Google Chrome has been successfully hacked as it discovers 30 security flaws–seven of which pose a “high” threat to users. In a blog post, Google revealed that a new update will make improvements for Windows, Mac, and Linux, to fix the security issues after the hack.
Can you encrypt Chrome?
Adding Search Encrypt To Google Chrome Scroll to the bottom of the page and click “Get more extensions” Search for “search encrypt” (Or just visit this page) Next to Search Encrypt select “+ Add to Chrome”. You will be prompted to add our extension.
Can someone hack my Chrome passwords?
Hackers can steal your Google Chrome or Microsoft Edge login password through malware, experts claim. Dangerous malware can steal your Google Chrome or Microsoft Edge login password stored in the browsers.
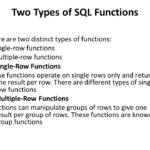
What is Chrome’s strongest security?
Advanced Protection is Google’s strongest account security, which comes with some restrictions on your account: You need your security key to sign in on any new device.
How do you tell if Chrome has been hijacked?
The most obvious sign that your browser has been exploited is that your homepage is different from what it used to be or toolbars that you don’t recognize have appeared. You might also see new favorites or bookmarks just below the address bar or if you manually look through the bookmarks.
What is send securely for Chrome?
SendSafely is an end-to-end encryption platform that eliminates the need for pre-shared encryption keys and passwords. With SendSafely, nobody other than you and the people you send items to can view them…not even us.
What encryption does Chrome use?
Starting with Chrome 80, the browser encrypts local passwords and cookies in Windows using AES-256 encryption. Prior to Chrome 80, the browser leveraged the data protection API (DPAPI) built into the OS to handle encryption chores.
What level of encryption does Chrome use?
Issue 37277: Chrome uses 128-bit encryption on some HTTPS sites even if other browsers can uses 256bit encryption.
Why You Should Never save passwords on Chrome?
The Browser Security Risk In the event one of your accounts was compromised, if you reuse passwords (which many people do) the hacker could also gain access to other accounts that belong to you.
How do hackers know my password?
Another popular way to get hold of your passwords is via malware. Phishing emails are a prime vector for this kind of attack, although you might fall victim by clicking on a malicious advert online (malvertising), or even by visiting a compromised website (drive-by-download).
Is Google Chrome safer than Microsoft Edge?
In fact, Microsoft Edge is more secure than Google Chrome for your business on Windows 10. It has powerful, built-in defenses against phishing and malware and natively supports hardware isolation on Windows 10—there’s no additional software required to achieve this secure baseline.
What is cross account protection?
With Cross-Account Protection, we can share security notifications about suspicious events with apps and services you’ve connected to your Google Account. That way, third-party apps and services can use Google’s suspicious event detection to help keep you safer online.
Is Google Safe Browsing a good idea?
Keeping over four billion devices safer. Google Safe Browsing helps protect over four billion devices every day by showing warnings to users when they attempt to navigate to dangerous sites or download dangerous files.
Which is better Google or Google Chrome?
Those who are looking to find out information based on keywords or phrases will want to just use the Google search bar, but those who are looking to have multiple tabs open or are looking for a particular website will want to choose Google Chrome.
What is the first thing you do when you get hacked?
Step 1: Change your passwords This is important because hackers are looking for any point of entry into a larger network, and may gain access through a weak password. On accounts or devices that contain sensitive information, make sure your password is strong, unique—and not easily guessable.
Who is the No 1 hacker in world?
Kevin Mitnick is the world’s authority on hacking, social engineering, and security awareness training. In fact, the world’s most used computer-based end-user security awareness training suite bears his name. Kevin’s keynote presentations are one part magic show, one part education, and all parts entertaining.
Will uninstalling Chrome remove malware?
After you uninstall and install Chrome again and log into your Google account, it will restore any settings, extensions, and potentially malware from the cloud backup. So if resetting browser settings and removing extensions didn’t help, reinstalling Chrome won’t remove malware either.
Can a hacker take control of my computer?
Your computer can be used to attack other computers. Sometimes hackers will take over a computer, sometimes thousands of them, to launch an attack on a website they’ve targeted.
Can an offline computer be hacked?
Still More Secure Than a Networked PC These attacks demonstrate that it is possible to hack an offline PC, even if you don’t have physical access. However, although technically feasible, these attacks aren’t straightforward. Most of these methods require a particular setup or optimal conditions.
Is confidential mode the same as encrypted?
All in all, Confidential Mode has the potential to be useful for what it is, but it doesn’t involve encryption or any sort of meaningful, higher-level privacy.
How do I send a secure email attachment?
In message that you are composing, click File > Properties. Click Security Settings, and then select the Encrypt message contents and attachments check box. Compose your message, and then click Send.