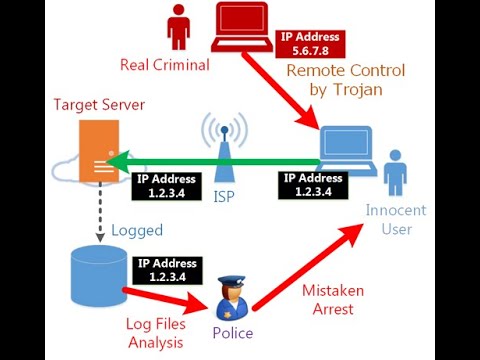
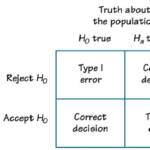
A VPN can be used to bypass a proxy server or firewall and prevent your computer from being directed to a site it doesn’t want to visit. This action provides an additional measure of security for anyone using a public Wi-Fi connection or any other unfamiliar network.
Does firewall work with VPN?
The VPN is completely protected from the Internet by the firewall. There is only one machine controlling all access to and from the Internet. Network restrictions for VPN traffic are located only on the VPN server, which can make writing rulesets easier.
Which VPN can break firewall?
OpenVPN is the most reliable, safe, and flexible protocol and will stop any firewall from standing in your way. Aside from choosing a service with OpenVPN, make sure it has 256-bit AES encryption as well as DNS and IPv6 leak protection.
Can a firewall be bypassed?
A firewall may be secure, but if it’s protecting an application or operating system with vulnerabilities, a hacker can easily bypass it. There are countless examples of software vulnerabilities that hackers can exploit to bypass the firewall.
Why is firewall a problem for VPN?
You can’t set up security rules on VPNs, as you don’t have the authority to establish any packet or network restrictions from your own computer. While VPNs allow you to bypass geo-restrictions, firewalls can only create restrictions that you have access to on your computer.
How do hackers get past firewalls?
To get around the firewall, attackers direct emails to specific targets within the network with the intention of tricking a user into accessing the email, which then gives them entry. Alternatively, they can attack public IP addresses found on a server to update their C&C systems.
Does DMZ bypass firewall?
A DMZ helps electronic signals bypass strict firewall and router security and open all ports for faster delivery of data packets.
How do you bypass school WIFI blocks without a VPN?
You can use Smart DNS to access blocked content and bypass geo-restrictions without triggering blocking mechanisms. For the best results, use premium Smart DNS providers. Most VPNs also offer Smart DNS under various names. In case you can’t use a VPN, you can request the Smart DNS.
What is bypass port?
A bypass switch (or bypass TAP) is a hardware device that provides a fail-safe access port for an in-line active security appliance such as an intrusion prevention system (IPS), next generation firewall (NGFW), etc.
Can my router block VPN?
Lots of routers block standard VPN protocols, like Point-to-Point Tunneling (PPTP) or SSTP. There’s probably an option that allows you to allow these protocols to communicate freely, but it’s easier to manipulate settings within the VPN tool itself.
Is VPN safer than antivirus?
Is a VPN better than an antivirus? No, a VPN alone is not better than an antivirus. However, both tools complement each other and can only help you maximize your security and privacy while used together. A VPN encrypts your traffic to protect private data whereas an antivirus prevents malware infections.
How do I get past administrative block?
Method 1. Right-click on the file you’re trying to launch, and select Properties from the context menu. Switch to the General tab. Make sure to place a checkmark in the Unblock box, found in the Security section. Click Apply, and then finalize your changes with the OK button.
Is firewall enough protection?
Most likely, it’s the trusty old firewall. However, the truth of the matter is that your firewall isn’t pulling its weight. A firewall alone simply isn’t enough protection against today’s cyber-threats. That doesn’t mean you should ditch your firewall, though – it’s part of a larger plan.
What can’t a firewall protect against?
A. Firewalls can’t protect very well against things like viruses or malicious software (malware). There are too many ways of encoding binary files for transfer over networks, and too many different architectures and viruses to try to search for them all.
Does firewall keep hackers out?
Firewall security measures are one of the most basic cyber protection tools that organizations of all sizes use to prevent data breaches and hacking. Network security firewalls filter out incoming traffic to prevent malicious files from being downloaded and block attackers from accessing sensitive systems.
Why is firewall blocking a site?
A network administrator may restrict certain websites with a firewall to prevent them from being accessed, whether for protection from malicious content or to save bandwidth. If you figure out that a web page has been blocked due to such restrictions, you can sometimes unblock it by switching from Wi-Fi to mobile data.
Can VPN bypass blocked sites?
A VPN lets you access blocked sites on mobile too. Now you’re browsing anonymously and securely from a hidden location. VPNs let you unblock websites, protect your online privacy, and stay safe on public Wi-Fi. A VPN is the easiest, most comprehensive tool to bypass content blocks.
Why are schools blocked everything?
For school administrators, students’ safety is the primary concern; they do not want their students to land in any trouble while they are at school. Also, students can easily get distracted by the internet and various contents over it; hence school administrators block everything.
How do I bypass Web filter violation?
How to Bypass FortiGuard Web Filtering Using a VPN. To unblock your network and access blocked websites such as Facebook and SoundCloud, just install a VPN app on your device. You’ll get a secure, encrypted tunnel between the VPN server and your device.
How can I access blocked sites without VPN?
You can use short links, like TinyURL or Bitly, to see these sites. Alternatively, you can use a restricted website’s IP address instead of their URL. Finally, you can use a proxy website, like ProxFree; however, some proxy sites may be blocked by your network, so you may have to use another one.
Why is my Internet blocking certain websites?
Websites can be blocked at three levels: Computer level, Network level or the ISP/Governmental level. Some DNS services, such as Open DNS, too provide options to block certain types of websites for different users sharing the computer.
Why some sites are not opening in Chrome?
There could be something wrong with your Chrome profile that’s causing problems. Uninstall Chrome and make sure to check the box to delete browsing data. Then reinstall Chrome. Uninstall and reinstall extensions.
Does a VPN bypass the OS/router firewall?
A VPN doesn’t bypass your OS / router firewall. And a VPN doesn’t act as a firewall either. We do not provide addon firewall service. You will need a good Antivirus/firewall protection suite to prevent malwares and intrusion.
Is it possible for a firewall to block VPN?
Yes, it is possible for a firewall to block your VPN. Luckily, it’s also possible to bypass this block with the help of obfuscated servers. However, most firewalls don’t block VPNs by default – a firewall will usually block VPN connections only if it was configured to do so.
What is a VPN firewall and do you need one?
So, a VPN firewall is a combination of the two. It is designed to prevent malicious internet users from intercepting a VPN connection. The firewall may come as software, hardware, or an all-inclusive device. With a firewall on your VPN, only authorized internet traffic can access your network.
How to bypass a firewall?
One of the most effective ways of bypassing a firewall is turning it off. Yes, if you kill the firewall service, there is no way it will get in your way of accessing the sites you want to access. However, this will only work if the firewall is a software installed on your system.