On the left, click Applications. Look for any programs you don’t recognize. Right-click the name of any unwanted programs. Click Move to Trash.
How do I remove unwanted programs from Chrome?
On the left, click Applications. Look for any programs you don’t recognize. Right-click the name of any unwanted programs. Click Move to Trash.
Why does Chrome take so long to check for harmful software?
Conclusion. Google Chrome’s CleanUp Tool may sometimes crash while searching for harmful software. To fix the problem, update Chrome, clear the cache and cookies and restart your computer. If the issue persists, uninstall the browser, remove the Chrome folder from Local App Data and download a fresh copy of the browser …
How do I remove unwanted programs from Chrome?
On the left, click Applications. Look for any programs you don’t recognize. Right-click the name of any unwanted programs. Click Move to Trash.
Why does Chrome take so long to check for harmful software?
Conclusion. Google Chrome’s CleanUp Tool may sometimes crash while searching for harmful software. To fix the problem, update Chrome, clear the cache and cookies and restart your computer. If the issue persists, uninstall the browser, remove the Chrome folder from Local App Data and download a fresh copy of the browser …
How do I know if I have unwanted extensions in Chrome?
To remove (or uninstall) Chrome extensions, follow the steps below: Open Chrome, and click / tap the menu button “…” Click / tap More Tools. Click / tap Extensions.
Why do I keep getting random notifications from Chrome?
A: By default, Chrome alerts you whenever a website, app, or extension wants to send you notifications. So if you’re getting notifications it’s because you’ve allowed a site to send you notifications, though it’s easy to miss being asked if it’s OK.
Will uninstalling Chrome remove malware?
After you uninstall and install Chrome again and log into your Google account, it will restore any settings, extensions, and potentially malware from the cloud backup. So if resetting browser settings and removing extensions didn’t help, reinstalling Chrome won’t remove malware either.
What is unsafe software?
Malware is unsafe or unwanted software that may steal personal info or harm your device. You may have malware on your device if: Google signed you out of your Google Account to help protect you from malware on your device.
How can I find a hidden Virus on my computer?
You can also head to Settings > Update & Security > Windows Security > Open Windows Security on Windows 10, or Settings > Privacy and Security > Windows Security > Open Windows Security on Windows 11. To perform an anti-malware scan, click “Virus & threat protection.” Click “Quick Scan” to scan your system for malware.
What happens when you reset Chrome settings?
Resetting Chrome will restore your home page and search engine to their default settings. It will also disable all browser extensions and clear out your cookie cache. But your bookmarks and saved passwords will remain, at least in theory. You may want to save your bookmarks before performing a browser rest.
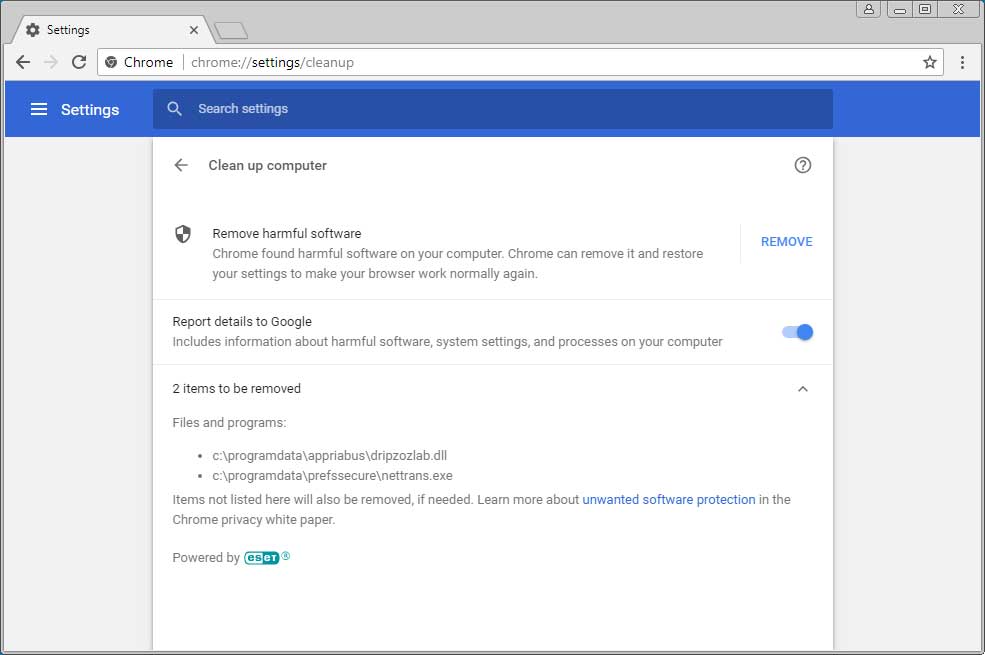
What is the Chrome cleanup tool?
The Chrome Cleanup Tool is a program written by Google that will scan a computer for programs that cause problems in Google Chrome. The targeted applications are potentially unwanted programs, malware, badware, and adware extensions that cause advertisements or other wanted actions to appear in Chrome.
How good is Google Chrome antivirus?
Does Chrome have virus protection? Yes, it includes a built-in antivirus for Windows. Chrome Cleanup can quickly scan your PC for suspicious applications and not only. Chrome antivirus requires no additional installation and adds extra layers of protection against digital threats.
Why do we should remove unnecessary Programs?
Uninstalling unused or unwanted programs can help your computer in various ways. By uninstalling these programs you will be, Adding hard drive space. Increasing computer speed – By removing programs you’re not using, they won’t have access to run in your background; therefore, increasing PC speeds.
How do I remove unwanted programs from Chrome?
On the left, click Applications. Look for any programs you don’t recognize. Right-click the name of any unwanted programs. Click Move to Trash.
Why does Chrome take so long to check for harmful software?
Conclusion. Google Chrome’s CleanUp Tool may sometimes crash while searching for harmful software. To fix the problem, update Chrome, clear the cache and cookies and restart your computer. If the issue persists, uninstall the browser, remove the Chrome folder from Local App Data and download a fresh copy of the browser …
How do I block Chrome extensions?
You can try with providing the Permission to the Goggle Chrome Extensions ( Allow/ Deny ) for the particular User’s. To disable write access, Right Click the Extensions -> properties -> security -> edit -> Select the User. Hit Allow/Deny on check box and they will/ will not be able to install extensions.
Does Chrome have built in antivirus?
Does Chrome have inbuilt Antivirus? YES, Google Chrome comes with an inbuilt Malware scanner. It can search and report the malicious files and applications that are causing the trouble on your system or browser. However, this inbuilt anti-malware only comes with the Windows version of Google Chrome.
Can you get malware from Chrome?
Google Chrome includes a feature to synchronize your browser data between computers, including web browser extensions. This is a convenient feature, but when malware infects your Google Chrome browser, it can hitch a ride on the sync data and become difficult to remove with anti-virus programs.
How do I stop Chrome from detecting viruses?
1] Disable the Virus Scan feature in Chrome Click on the Advanced button to navigate to the Privacy and security section. Select the option for Sync and Google services. Toggle the option for Safe Browsing to be off. Restart your browser and your issue should be resolved.
What is Chrome virus?
What Is the Chromium Virus? The Chromium virus is a malicious web browser that is created using the Chromium code. It is able to overwrite the Chrome browser and replace the original shortcuts with fake ones.
Why do spammers register on my site?
But the question remains—why do spammers register on your site? There are various reasons these malicious spambots want to spam your signups. One is that they’re looking for weaknesses in your site to exploit them for further gain. It could also be to gather all of your email addresses and send you spam.