browser hijacker: A form of malware that changes your homepage and redirects you to other websites.
Which malware changes your home page?
browser hijacker: A form of malware that changes your homepage and redirects you to other websites.
Does uninstalling Chrome remove malware?
When you uninstall and reinstall Chrome, the moment you login to your Google account again, Google will faithfully restore your cloud backup which ends up reinstalling the malware. To fix this, you need to wipe your Chrome sync data. That will delete all the cloud backups, including hopefully the malware.
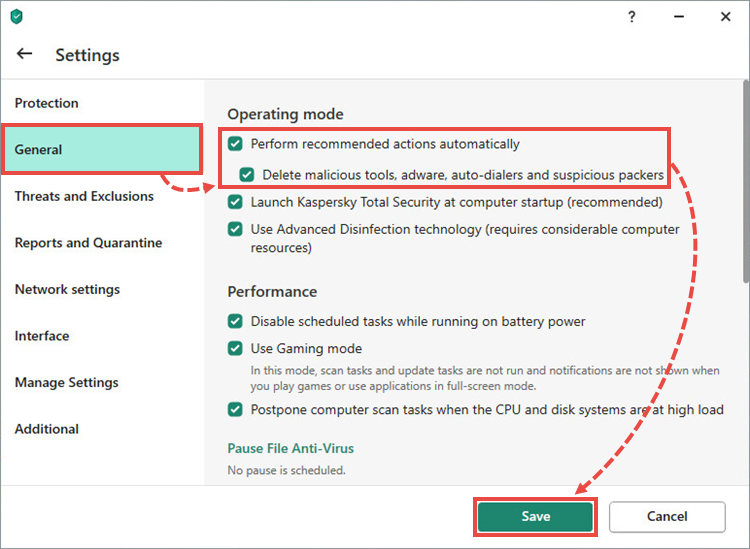
What does Chrome reset and cleanup do?
If Chrome is not acting like its usual self, it includes a clean-up and reset process that may set things right. The process scans your computer for harmful software that could cause problems and then removes it.
Is search a virus?
This monitoring can lead to privacy issues and identity theft. www-searching.com is not technically a virus or malware, however, it is browser settings-changing adware, and therefore, you are advised to eliminate it from your Internet browsers.
Can your browser be hacked?
In most cases, browser hijacking is a crude – if deeply annoying – scam designed to redirect users to sites or ads where extra clicks generate revenue for the hackers. It can be dangerous, however, depending on the kind of malware involved.
How do you tell if Chrome has been hijacked?
The most obvious sign that your browser has been exploited is that your homepage is different from what it used to be or toolbars that you don’t recognize have appeared. You might also see new favorites or bookmarks just below the address bar or if you manually look through the bookmarks.
How can I find a hidden virus on my computer?
You can also head to Settings > Update & Security > Windows Security > Open Windows Security on Windows 10, or Settings > Privacy and Security > Windows Security > Open Windows Security on Windows 11. To perform an anti-malware scan, click “Virus & threat protection.” Click “Quick Scan” to scan your system for malware.
What should you do if you have a virus?
Get rest and stay hydrated. Take over-the-counter medicines, such as acetaminophen, to help you feel better. Stay in touch with your doctor. Call before you get medical care.
Why does Chrome keep telling me I have a virus?
The Google Chrome pop-up virus is a common and frustrating malware on Android phones. The most common cause for this virus is downloading apps from third-party or unknown sources which contain the malware. The most important thing is to NOT tap anywhere on the pop-up!
How can you tell a fake virus warning?
The Federal Trade Commission (FTC) warns that the scareware scam has many variations, but there are some telltale signs: You may get ads that promise to “delete viruses or spyware,” “protect privacy,” “improve computer function,” “remove harmful files,” or “clean your registry.”
Can your Google Account get a virus?
Users who download Gooligan-infected apps or click links in phishing messages are being exposed to the malware, which allows attackers to access sensitive information from Google apps like Gmail, Drive, and Photos.
Why does Chrome keep telling me I have a virus?
The Google Chrome pop-up virus is a common and frustrating malware on Android phones. The most common cause for this virus is downloading apps from third-party or unknown sources which contain the malware. The most important thing is to NOT tap anywhere on the pop-up!
Can Chrome check for viruses?
Does Chrome have inbuilt Antivirus? YES, Google Chrome comes with an inbuilt Malware scanner. It can search and report the malicious files and applications that are causing the trouble on your system or browser. However, this inbuilt anti-malware only comes with the Windows version of Google Chrome.
What causes browser hijacking?
Browser hijacking occurs when unwanted software alters the activity of the internet browser to spy on users, steal their information, or to display persistent advertising.
What are the 4 examples of browser hijacker?
Some of the most popular hijackers known on the Web are the Babylon Toolbar, Conduit Search or Search Protect, CoolWebSearch, SourceForge Installer, OneWebSearch, Snap.do, and Sweet Page.
What happens if your browser is hacked?
Symptoms of Browser Hijacking Searches that are redirected to different websites. Multiple pop-up advertisement alerts. Slow-loading web pages. Multiple toolbars on a web browser not installed by the user.
Can someone hack your Google Chrome?
(NewsNation) — If you use Google Chrome as an internet browser, beware: Your information could be compromised. Google issued an alert warning billions of Chrome users that the browser has been successfully targeted by hackers.
What is page hijacking?
Page hijacking involves creating a site that roughly duplicates the content of an existing site, then games search engine ranking systems to make sure that the second, duplicated site gets more recognition than the original. The goal in page hijacking is to make the second page more prominent than the first.
What is a hijacked search engine?
Search hijacking, or browser hijacking, occurs when a third party sneaks files into your computer and alters your browser’s settings without your permission. These changes help the hijackers make money by forcing you to look at ads, click on paid links, or give up your private information.
How do I remove home search design?
Click Look and feel from the left menu in Control Panel, and open the Customize tab. Select the Google branding option. Chose the Disable Google Branding option.
What is the first thing you do when you get hacked?
Step 1: Change your passwords This is important because hackers are looking for any point of entry into a larger network, and may gain access through a weak password. On accounts or devices that contain sensitive information, make sure your password is strong, unique—and not easily guessable.