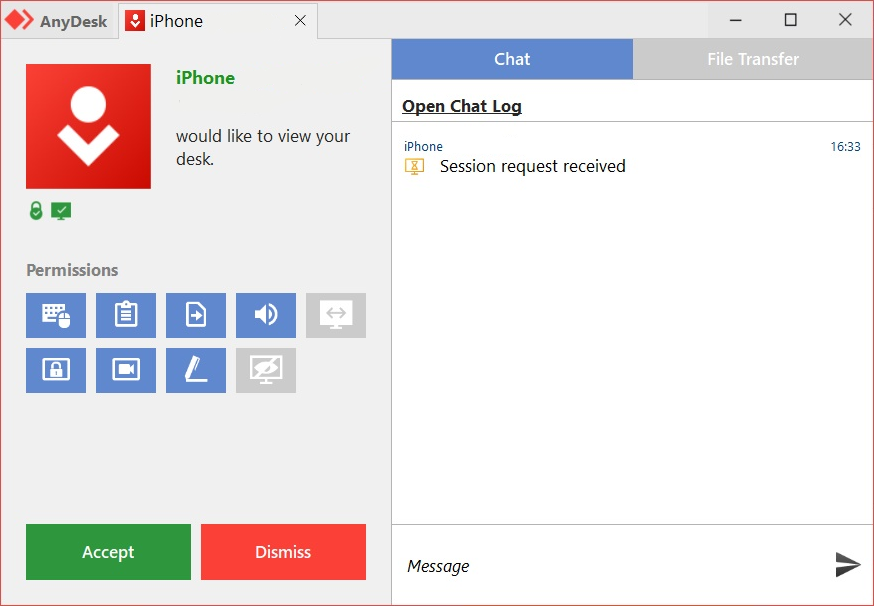
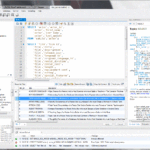
To get started, open AnyDesk. The number you see on the left is your personal ID. People can use this number to access your device, and you need this number from the person you want to connect to. Type the ID of the remote device into the search bar on the right.When AnyDesk is running on both devices, check the address listed in the pane for This Desk. Then, enter the address given in the pane for Remote Desk on a guest device and click on Connect. A window will appear on the remote PC asking the user to accept the request for the remote session.
Can someone use AnyDesk to access my computer?
Anyone who knows the password and your AnyDesk ID can potentially have full access to your computer depending on the available permissions.
How can I remotely access a computer remotely?
On your Windows, Android, or iOS device: Open the Remote Desktop app (available for free from Microsoft Store, Google Play, and the Mac App Store), and add the name of the PC that you want to connect to (from Step 1). Select the remote PC name that you added, and then wait for the connection to complete.
How do I use AnyDesk unattended?
To use Unattended Access, setting up a password on the remote device is required. This is done in the security settings. You only get access to the remote device, when you enter this password in a dialog window. The window appears after you requested a session.
How do I access another computer on the same network?
Step 1: Connect two Computers using an ethernet cable. Step 2: Click on Start->Control Panel->Network and Internet->Network and Sharing Center. Step 3: Click on option Change Advanced Sharing Settings in the upper-left side of the window. Step 4: Turn on file sharing.
Is AnyDesk a security risk?
AnyDesk Remote Desktop Software comes with the highest security standards. From military-grade encryption to customizable security features, AnyDesk offers outstanding security that perfectly fits your needs.
Does AnyDesk use camera?
He simply uses AnyDesk: Almost every laptop has a built-in webcam, and with AnyDesk, you can turn it on from anywhere and have a clear view of your room. That’s where you’ll find your kitties sleeping soundly. Be sure to use a strong password and disconnect the session afterwards.
Does AnyDesk work after uninstalling?
No ! then the data which is stored in your sd card releted to that particular apps is not deleted.
Can you monitor someone’s computer?
Can You Monitor Someone’s Computer? This question is asked of us many times, and the answer apparently is “yes”. You may have heard about computer hackers who are capable of breaking the security of someone’s computer, stealing credit or debit card information, and getting other personal data to sell it.
How can I access a device by IP address?
You can follow a path to a device if you know its IP address by using the tracert command at the command prompt (cmd). Open a Command Prompt window and type in tracert followed by the IP address that you know. The output will show each router that has a connection to that device will pass through.
What can hackers do with AnyDesk?
Sophos discovered that the AvosLocker attackers installed AnyDesk so it works in Safe Mode, tried to disable the components of security solutions that run in Safe Mode, and then ran the ransomware in Safe Mode.
Does AnyDesk use camera?
He simply uses AnyDesk: Almost every laptop has a built-in webcam, and with AnyDesk, you can turn it on from anywhere and have a clear view of your room. That’s where you’ll find your kitties sleeping soundly. Be sure to use a strong password and disconnect the session afterwards.
What can be accessed through AnyDesk?
AnyDesk is a remote desktop software that allows us to connect to a computer remotely. It is a cross-platform software that provides platform independent remote access to different devices such as PC and other host devices. It provides remote access, file transfer, VPN features.
What can a scammer do with remote access to your computer?
In a remote access scam, a scammer attempts to persuade you into giving them remote control over your personal computer, which allows the scammer to con money out of you and steal your private information.
What are the disadvantages of AnyDesk app?
The Cons. It can be slightly intimidating for first-time users. It cannot work without an active internet connection. The free version doesn’t have the address book feature.prieš 6 dienas
How do I know if AnyDesk is disconnected?
Check the corner of the taskbar next to the clock if the AnyDesk icon is showing up. If yes, then click on it and terminate the connection. If you have installed AnyDesk, uninstall it. If you have only let it run for one time only, then you are safe.
Can a computer camera be turned on remotely?
The remotely activated webcam can be used to watch anything within the webcam’s field of vision, sometimes including the webcam owner themselves. Camfecting is most often carried out by infecting the victim’s computer with a virus that can provide the hacker access to their webcam.
Can we connect AnyDesk on mobile?
Designed for Android The Android version of the AnyDesk Remote Desktop app integrates seamlessly with your device. Easily connect and control desktops, smartphones, and other devices remotely via your Android device.
What are the disadvantages of AnyDesk app?
The Cons. It can be slightly intimidating for first-time users. It cannot work without an active internet connection. The free version doesn’t have the address book feature.prieš 6 dienas
What can a scammer do with remote access to your computer?
In a remote access scam, a scammer attempts to persuade you into giving them remote control over your personal computer, which allows the scammer to con money out of you and steal your private information.
Is AnyDesk a security risk?
AnyDesk Remote Desktop Software comes with the highest security standards. From military-grade encryption to customizable security features, AnyDesk offers outstanding security that perfectly fits your needs.
Can a hacker see my computer screen?
Researchers at DEF CON say computer monitors can be hacked to actively snoop on you, covertly steal data and even manipulate what you see on the screen. The list of ways we can be spied upon seems nearly endless, but you can add one more to that list: active screen snooping via your vulnerable monitor.
How to connect to AnyDesk remotely?
To access the remote device, the ID number of AnyDesk is necessary, with which connecting becomes feasible. One has to know this ID number before diving into making a remote connection to any device or PC.
Is AnyDesk free for personal use?
Free for personal use and available for a monthly subscription price for business use, AnyDesk lets you quickly connect to any remote device running the program. You can require a response from the remote PC or set a password for unattended access. You can connect from a mobile device to a PC.
How do I remotely access a PC?
If you wish to remotely access a PC within your organization, you’ll likely first need to establish a secure connection through a VPN or Remote Access Gateway. Make sure AnyDesk is running on both the remote and guest devices.
How do I secure access to a remote device?
Use a password to securely access devices from anywhere, so that the remote session doesn’t have to be accepted manually. Double protect access to the remote device. Use time-based number codes in addition to your Unattended Access password. The remote device is in sleep mode and can’t be accessed?