The browser hijacking software could be bundled with a browser extension or be part of the software. Browser hijackers can also originate from shareware, freeware, adware and spyware infections. Browser hijackers are likely to be downloaded unintentionally by the user.
What are the 4 examples of browser hijacker?
Some of the most popular hijackers known on the Web are the Babylon Toolbar, Conduit Search or Search Protect, CoolWebSearch, SourceForge Installer, OneWebSearch, Snap.do, and Sweet Page.
How do I fix my hijacked Chrome?
To remove browser hijackers in Chrome, remove any suspicious Google Chrome extensions. Then go to the Chrome settings and restore your browser to the default settings.
What are the 4 examples of browser hijacker?
Some of the most popular hijackers known on the Web are the Babylon Toolbar, Conduit Search or Search Protect, CoolWebSearch, SourceForge Installer, OneWebSearch, Snap.do, and Sweet Page.
Will uninstalling Chrome remove malware?
After you uninstall and install Chrome again and log into your Google account, it will restore any settings, extensions, and potentially malware from the cloud backup. So if resetting browser settings and removing extensions didn’t help, reinstalling Chrome won’t remove malware either.
Can your browser be hacked?
In most cases, browser hijacking is a crude – if deeply annoying – scam designed to redirect users to sites or ads where extra clicks generate revenue for the hackers. It can be dangerous, however, depending on the kind of malware involved.
Can Chrome get a virus?
Scanning for viruses can be done very easily on Google Chrome. In this guide, we have explained how viruses can be caught and removed from Windows, Mac, and Android. How do I fix the redirect virus in Chrome?
How do you tell if Chrome has been hijacked?
The most obvious sign that your browser has been exploited is that your homepage is different from what it used to be or toolbars that you don’t recognize have appeared. You might also see new favorites or bookmarks just below the address bar or if you manually look through the bookmarks.
Can browser hijackers steal passwords?
Sometimes hackers drop malware into browsers to take users to websites used to capture critical information about them. The data could include user IDs, passwords, full names, addresses, social security numbers, and even answers to security questions — mother’s maiden name, etc.
Can Chrome browser be hacked?
(NewsNation) — If you use Google Chrome as an internet browser, beware: Your information could be compromised. Google issued an alert warning billions of Chrome users that the browser has been successfully targeted by hackers.
Why does Google keep sending me to other search engines?
Such redirects to various search engines are caused by software classified as browser hijackers. They modify browser settings to promote (mostly fake) Web searching tools. Furthermore, browser-hijacking software spies on users’ browsing activity.
What are the 4 examples of browser hijacker?
Some of the most popular hijackers known on the Web are the Babylon Toolbar, Conduit Search or Search Protect, CoolWebSearch, SourceForge Installer, OneWebSearch, Snap.do, and Sweet Page.
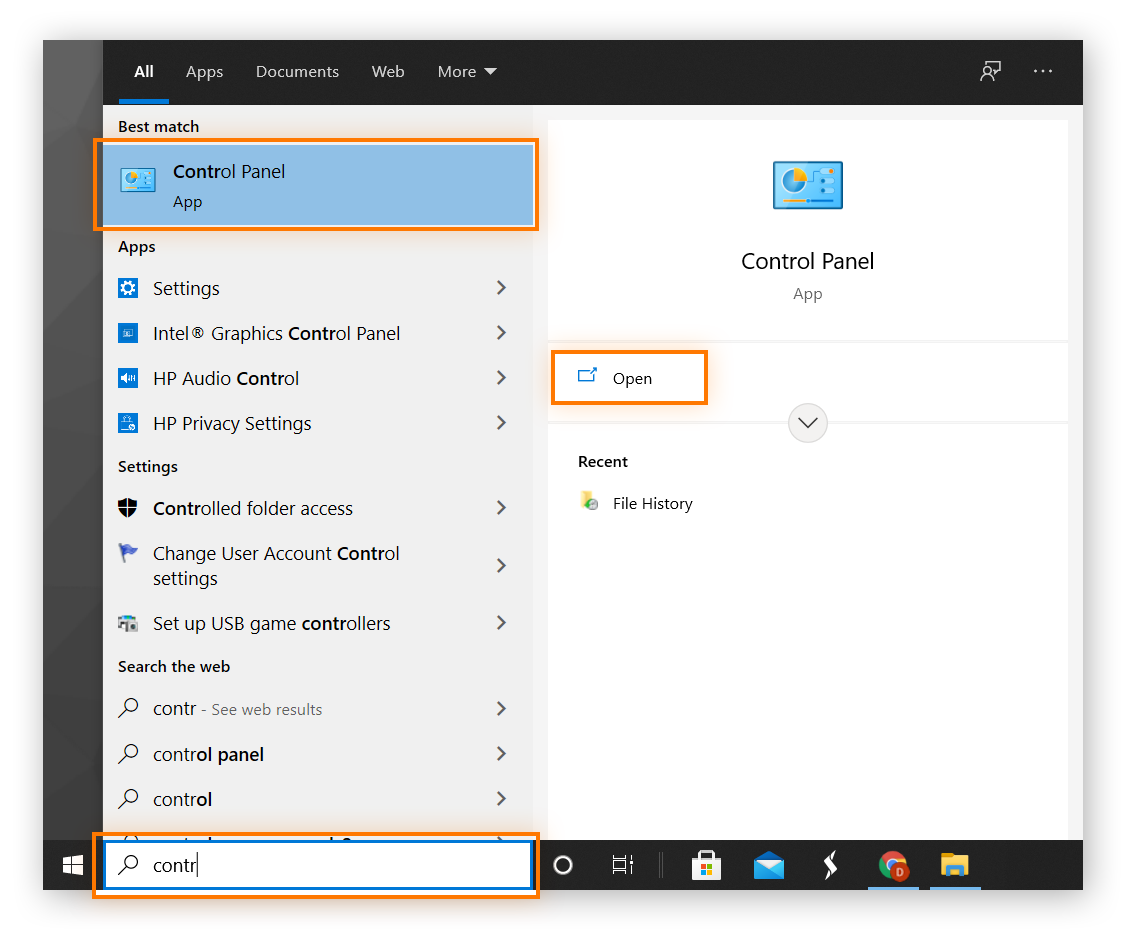
How do I fix my hijacked Chrome?
To remove browser hijackers in Chrome, remove any suspicious Google Chrome extensions. Then go to the Chrome settings and restore your browser to the default settings.
How can you tell a fake virus warning?
The Federal Trade Commission (FTC) warns that the scareware scam has many variations, but there are some telltale signs: You may get ads that promise to “delete viruses or spyware,” “protect privacy,” “improve computer function,” “remove harmful files,” or “clean your registry.”
How do I check for malware on Chrome?
To run a scan, you need to open Chrome’s settings. To do so, click on the triple-dot icon in the top-right corner, then click “Settings”. Once in the settings, you should run a quick “Safety check”, to do so, click on “Check now” in the “Safety check” subsection, which is third from the top.
Why is Google Chrome telling me I have a virus?
The Google Chrome pop-up virus is a common and frustrating malware on Android phones. The most common cause for this virus is downloading apps from third-party or unknown sources which contain the malware. The most important thing is to NOT tap anywhere on the pop-up!
What is the first thing you do when you get hacked?
Step 1: Change your passwords This is important because hackers are looking for any point of entry into a larger network, and may gain access through a weak password. On accounts or devices that contain sensitive information, make sure your password is strong, unique—and not easily guessable.
Can my browser get a virus?
Yes, you can get a virus just from visiting a website.
Can someone install spyware on my computer?
Abusers can install spyware on your computer if they have physical or Internet access to your computer. Some abusers might hack into your computer from another location via the Internet. Some might send spyware to you as an attached file that automatically installs itself when you open the email.
How can I find a hidden virus on my computer?
You can also head to Settings > Update & Security > Windows Security > Open Windows Security on Windows 10, or Settings > Privacy and Security > Windows Security > Open Windows Security on Windows 11. To perform an anti-malware scan, click “Virus & threat protection.” Click “Quick Scan” to scan your system for malware.
What is device hijacking?
When a legitimate device (browser, phone, app) is hijacked for the purposes of carrying out fraud, that device is known as a hijacked device.
Is Safari a virus?
It may seem like the iPhone’s main browser, Safari, has no risk of giving your phone a virus. However, no matter the method of browsing the internet, there’s always a chance it could happen. Although it’s incorrect to say that the iPhone can’t get a virus, it is true that iOS devices are generally more secure.