Access to a corporate or public wifi network allows hackers to carry out various operations such as sniffing users’ credentials, executing a man-in-the-middle attack, and even redirecting victims to malicious websites for further compromise. People often associate computer hacking with compromising a system remotely.
Can hackers remotely access your computer?
Remote desktop hacks become a common way for hackers to access valuable password and system information on networks that rely on RDP to function. Malicious actors are constantly developing more and more creative ways to access private data and secure information that they can use as leverage for ransom payments.
What gives hackers open access to your computer?
They do this either by purchasing ads directly, hijacking the ad server or hacking someone else’s ad account. Malware sold as legitimate software – Fake antivirus programs have infected millions of computers. Software is offered as free, available through the internet that includes malware designed to infect computers.
What happens when a hacker gets into your computer?
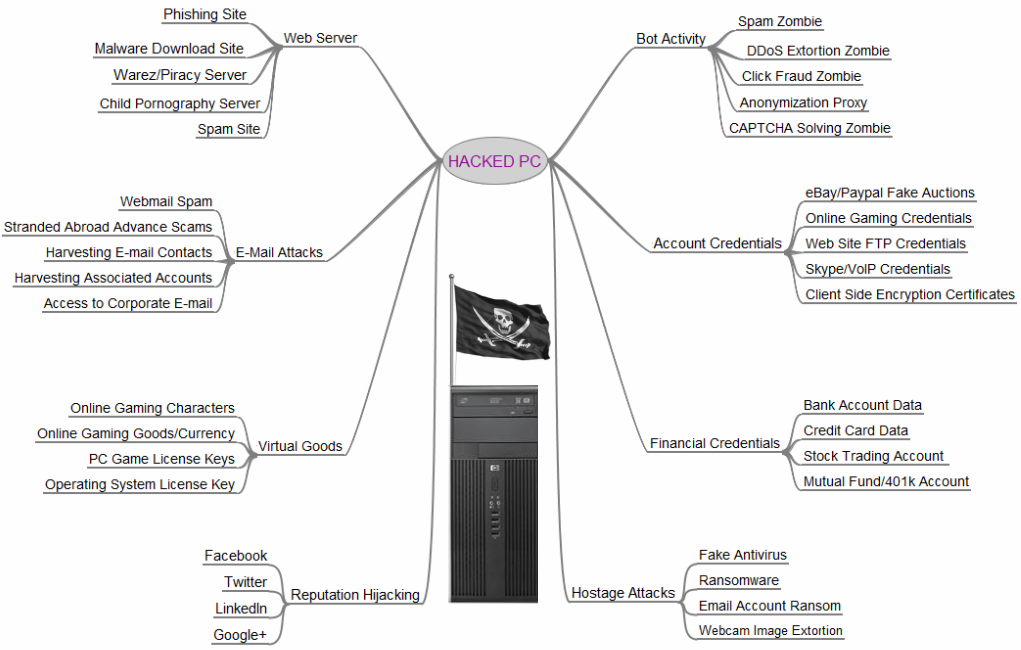
The hacker could be across the street or across the country. No matter where they are, they can copy photos from your computer onto theirs, or delete your tax records. They can steal your personal data or delete the programs you have on your computer. Worse yet, they can download more viruses.
Can you tell if someone has hacked your computer?
Frequent pop-up windows, especially the ones that encourage you to visit unusual sites, or download antivirus or other software. Changes to your home page. Mass emails being sent from your email account. Frequent crashes or unusually slow computer performance.
What gives hackers open access to your computer?
They do this either by purchasing ads directly, hijacking the ad server or hacking someone else’s ad account. Malware sold as legitimate software – Fake antivirus programs have infected millions of computers. Software is offered as free, available through the internet that includes malware designed to infect computers.
What happens when a hacker gets into your computer?
The hacker could be across the street or across the country. No matter where they are, they can copy photos from your computer onto theirs, or delete your tax records. They can steal your personal data or delete the programs you have on your computer. Worse yet, they can download more viruses.
Does shutting down computer stop hackers?
In general, the answer is no, you cannot hack into a computer that’s been turned off. Unless two conditions are met, the PC cannot be restarted and hacked from outside, even if you leave it connected to the internet and to power.
Can someone access my computer remotely without me knowing?
“Can someone access my computer remotely without me knowing?” The answer is “Yes!”. This could happen when you are connected to the internet on your device.
Can hackers hack without Internet?
Can an Offline Computer be Hacked? Technically — as of right now — the answer is no. If you never connect your computer, you are 100 percent safe from hackers on the internet. There is no way someone can hack and retrieve, alter or monitor information without physical access.
What is the first thing you do when you get hacked?
Step 1: Change your passwords This is important because hackers are looking for any point of entry into a larger network, and may gain access through a weak password. On accounts or devices that contain sensitive information, make sure your password is strong, unique—and not easily guessable.
Can hackers be traced?
Most hackers will understand that they can be tracked down by authorities identifying their IP address, so advanced hackers will attempt to make it as difficult as possible for you to find out their identity.
What happens when you are hacked?
This can be really serious, hackers can use your identity details to open bank accounts, get credit cards, order products in your name, take over existing accounts and take out mobile phone contracts. Hackers could even get genuine documents such as passports and driving licenses in your name once they have stolen your …
Who is the No 1 hacker in world?
Kevin Mitnick is the world’s authority on hacking, social engineering, and security awareness training. In fact, the world’s most used computer-based end-user security awareness training suite bears his name. Kevin’s keynote presentations are one part magic show, one part education, and all parts entertaining.
Is someone spying on my computer?
To open the Activity Monitor, hit Command + Spacebar to open Spotlight Search. Then, type Activity Monitor and press Enter. Check over the list for anything you don’t recognize. To close out a program or process, double click, then hit Quit.
Can someone remotely access my computer without my knowledge?
There are two ways someone can access your computer without your consent. Either a family member or work college is physically logging in to your computer or phone when you are not around, or someone is accessing your computer remotely.
How do hackers hack remotely?
Remote hackers use various malware deployment methods; the most common (and probably the easiest) way for hackers to reach unsuspecting victims is through phishing campaigns. In this scenario, hackers will send emails with links or files, which unsuspecting recipients may click on.
What gives hackers open access to your computer?
They do this either by purchasing ads directly, hijacking the ad server or hacking someone else’s ad account. Malware sold as legitimate software – Fake antivirus programs have infected millions of computers. Software is offered as free, available through the internet that includes malware designed to infect computers.
What happens when a hacker gets into your computer?
The hacker could be across the street or across the country. No matter where they are, they can copy photos from your computer onto theirs, or delete your tax records. They can steal your personal data or delete the programs you have on your computer. Worse yet, they can download more viruses.
Can hackers access a sleeping computer?
A computer cannot be hacked “in” sleep mode, but it can be hacked either if the user resumes his or her computer to make it back into functioning under the power of the operating system or the hacker triggers a Wake-on-Lan (WOL).
Does putting computer on sleep prevent hackers?
This means that when in sleep mode, the computer cannot be accessed by a network connection. A hacker needs an active network connection to your computer to be able to access it. A computer that is in sleep mode is just as protected from hackers as a computer that has been turned off.
Can laptop be hacked through WIFI?
You have likely heard of the dangers of using unsecure public Wi-Fi, so you know that hackers are out there snooping. It is pretty easy to hack into a laptop or mobile device that is on a public Wi-Fi connection with no protection. Hackers can read your emails, steal passwords, and even hijack your website log ins.
How can a hacker gain access to your computer?
10 Ways Hackers Can Gain Access To Your Laptop 1 Phishing. … 2 Malware. … 3 Weak passwords. … 4 Social engineering. … 5 Insecure network. … 6 USB connection. … 7 Outdated software. … 8 Downloading from unverified sources or dangerous sites. … 9 Clicking on false ads. …
Can a computer be hacked through an open port?
Hacking your computer through open ports For hackers to hack your computer, they often rely on open ports. These are not the physical ports of your computer (such as the USB port) but the endpoints of the internet connection that gather the data packets based on their scope (sending an email, accessing a webpage).
What is hacking and how does it work?
Once regarded as exploratory curiosity, hackers would access systems without permission only to see if they could. Hacking has converted over time into aggressive intrusions into computer systems for ill-begotten profit. Now hackers target vulnerable systems and mine for useful data that can be used to make or steal money, or used to commit fraud.
How does a USB drive get hacked?
Sometimes, hackers infect a USB drive with malware software and they left it behind in coffee shops or public places. Someone passing by might take the USB drive and plug it in their computer. Needless to say that once the drive is in, the computer gets compromised and the hacker gets access to the victim’s private information.