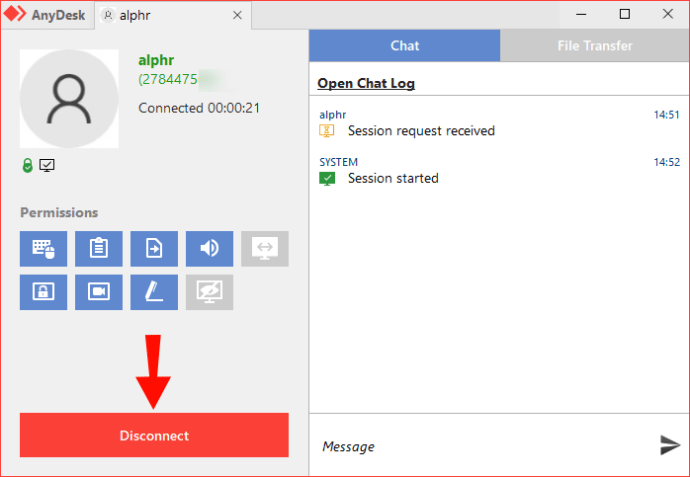
When it’s time to end the session, there are three ways you can end the connection: Click on the “Disconnect” button on the window of the other device. Close the tab of the remote device. Close the AnyDesk app.
How do I change my AnyDesk settings?
The User Interface settings can be found in Settings > User Interface. As the name implies, these settings predominately affect the user interface of the AnyDesk window. The session comment will be visible in the Sessions tab of the my.anydesk.com customer portal linked to the license of the client.
How do I stop AnyDesk from running in the background?
Exclusive Unattended Access To force the AnyDesk client to only be accessible using the Unattended Access password, “Never show incoming session requests” can be enabled in Settings > Security > Interactive Access.
How do I enable Ctrl Alt Del In AnyDesk?
How Do I Enable CTRL+Alt+Del in AnyDesk? To activate the “Send CTRL+ALT+DEL” function in AnyDesk on a remote Windows-based device, from your connected device, hold down the “CTRL+ALT+SHIFT” then press the “DEL” key.
How do I change my AnyDesk settings?
The User Interface settings can be found in Settings > User Interface. As the name implies, these settings predominately affect the user interface of the AnyDesk window. The session comment will be visible in the Sessions tab of the my.anydesk.com customer portal linked to the license of the client.
Can AnyDesk be tracked?
AnyDesk outputs trace files while running that can be utilized to diagnose problems. Some errors occur without causing an immediate crash and may cause other unintended behavior.
What is privacy mode on AnyDesk?
AnyDesk Privacy Mode allows you to blacken the screen of your remote device and still work on it as if you were sitting right in front of it. Nobody can view your screen and your data is safe.
What is unattended access in AnyDesk?
Access work? To use Unattended Access, setting up a password on the remote device is required. This is done in the security settings. You only get access to the remote device, when you enter this password in a dialog window. The window appears after you requested a session.
How do you do Ctrl Alt Delete on AnyDesk?
CTRL+ALT+DEL: Sends a CTRL+ALT+DEL command to the remote device. This is useful as CTRL+ALT+DEL commands sent via the keyboard are only transmitted locally when connecting from a Windows device. This option is only available if AnyDesk is installed on the remote Windows machine.
How do I press Ctrl Alt Delete in Remote Desktop?
Press the “CTRL,” “ALT” and “END” keys at the same time while you are viewing the Remote Desktop window. This command executes the traditional CTRL+ALT+DEL command on the remote computer instead of on your local computer.
How do you send Ctrl Alt Delete in Remote Desktop?
One option is to use the on-screen keyboard from within the first RDP session. You can press Ctrl-Alt-Del virtually, holding ctrl-alt on the top-level machine and clicking the ‘del’ in the desired level OSK. This allows you to send the key stroke within several depths of RDP session.
How do I get full Permissions on AnyDesk?
Setting up your whitelist You can find the Access Control List in the security tab of the AnyDesk settings. In order to activate access control, the security tab has to be unlocked. Use the + button to add an entry. A text entry will appear at the bottom of the list.
How do I fix connection to AnyDesk network?
Please make sure that AnyDesk is running on the remote computer and it is connected to the internet. This message is either shown due to a slow internet connection, an improperly configured firewall or a general network problem.
How do I change my AnyDesk settings?
The User Interface settings can be found in Settings > User Interface. As the name implies, these settings predominately affect the user interface of the AnyDesk window. The session comment will be visible in the Sessions tab of the my.anydesk.com customer portal linked to the license of the client.
What can a scammer do with remote access to your computer?
In a remote access scam, a scammer attempts to persuade you into giving them remote control over your personal computer, which allows the scammer to con money out of you and steal your private information.
Is AnyDesk a security risk?
AnyDesk Remote Desktop Software comes with the highest security standards. From military-grade encryption to customizable security features, AnyDesk offers outstanding security that perfectly fits your needs.
How do I know if AnyDesk is disconnected?
Check the corner of the taskbar next to the clock if the AnyDesk icon is showing up. If yes, then click on it and terminate the connection. If you have installed AnyDesk, uninstall it. If you have only let it run for one time only, then you are safe.
How do I completely remove AnyDesk from my Iphone?
Helpful answers. You can hold down Option key and the apps will start to jiggle, then press the cross button and press delete. The app is deleted. You can hold down Option key and the apps will start to jiggle, then press the cross button and press delete.
How do I find my AnyDesk ID on my computer?
On PCs where Anydesk is installed, the ID may be found in a text file. Alternatively, IDs may be found on the hub’s Status Page. c) If this file is present, double-click to open, and read the 9-digit number at the start of the text file. This is the PCs Anydesk ID.
What are the disadvantages of AnyDesk app?
The Cons. It can be slightly intimidating for first-time users. It cannot work without an active internet connection. The free version doesn’t have the address book feature.prieš 6 dienas
Does AnyDesk change your IP?
AnyDesk after accepting the connection from sharer screen will encrypt your traffic and secure your ip address with their relay servers and your privacy will be good, but the weakness occurs when incoming connection request is sent and you are able to retrieve other user ip address without interaction .
How do I restrict access to AnyDesk?
You can find the Access Control List in the security tab of the AnyDesk settings. In order to activate access control, the security tab has to be unlocked. Use the + button to add an entry. A text entry will appear at the bottom of the list.
How do I completely remove AnyDesk from Windows 7?
Remove the related items of AnyDesk using Control-Panel Windows 7 Users Click “Start” (the windows logo at the bottom left corner of the desktop screen), select “Control Panel”. Locate the “Programs” and then followed by clicking on “Uninstall Program”
How to start and end a connection using AnyDesk?
All you need to do is to click on the “Accept” button. When it’s time to end the session, there are three ways you can end the connection: Click on the “Disconnect” button on the window of the other device. Close the tab of the remote device. Now you know how to start and end a connection using AnyDesk.
What is AnyDesk malware?
What is AnyDesk Malware? AnyDesk is genuine application that provides remote System control functionality. It provides remote access to personal computers running the host application which can be installed on Windows, MacOS, Linux and FreeBSD.
Can someone access my phone if I accidentally installed AnyDesk?
You said you accidentally install AnyDesk on your phone , then no one can remotely access your phone with that app because it it need unique code for remotely access. What happens if I uninstall AnyDesk?