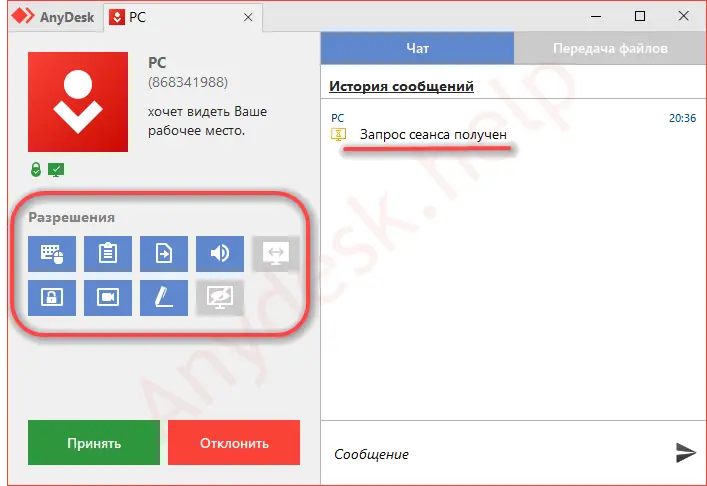
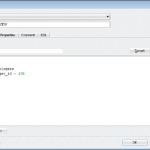
You can find the Access Control List in the security tab of the AnyDesk settings. In order to activate access control, the security tab has to be unlocked. Use the + button to add an entry. A text entry will appear at the bottom of the list.Create local firewall rules using Windows Firewall to block outgoing connections from AnyDesk.exe
Block the resolution of DNS records on the anydesk.com domain. If you run your own DNS server (such as an Active Directory server) then this is easy: Open your DNS …
Block anydesk. com in PiHole – this is another way to use DNS blocking to stop AnyDesk from connecting out via your network
How do I restrict access to AnyDesk?
You can find the Access Control List in the security tab of the AnyDesk settings. In order to activate access control, the security tab has to be unlocked. Use the + button to add an entry. A text entry will appear at the bottom of the list.
How do I make AnyDesk private?
First, set a password for Unattended Access in the security settings on the incoming side and allow Privacy Mode by ticking the corresponding box. Whenever you connect to the device via Unattended Access with Privacy Mode activated, the screens of your remote device will be black and mouse and keyboard will be locked.
Can anyone access my PC using AnyDesk?
To get started, open AnyDesk. The number you see on the left is your personal ID. People can use this number to access your device, and you need this number from the person you want to connect to.
How do I restrict access to AnyDesk?
You can find the Access Control List in the security tab of the AnyDesk settings. In order to activate access control, the security tab has to be unlocked. Use the + button to add an entry. A text entry will appear at the bottom of the list.
Can AnyDesk work without permission?
With this in mind, AnyDesk provides the ability to connect to a remote device using a password which bypasses the need for a user to accept the connection request. Note: While not required, it is highly recommended that AnyDesk is installed on the device where Unattended Access has been configured.
How do I activate Privacy Mode on remote screen AnyDesk?
Enabling privacy mode only takes a couple of clicks. Simply enable the permission on the remote side and activate Privacy Mode. A green icon will indicate if Privacy Mode is enabled.
How many users can connect to AnyDesk?
AnyDesk can be installed on multiple devices. It comes with: 3 concurrent users (additional users can be purchased), Unlimited concurrent sessions.
How secure is AnyDesk?
AnyDesk Remote Desktop Software comes with the highest security standards. From military-grade encryption to customizable security features, AnyDesk offers outstanding security that perfectly fits your needs.
What are the disadvantages of AnyDesk?
The Cons. It can be slightly intimidating for first-time users. It cannot work without an active internet connection. The free version doesn’t have the address book feature.prieš 6 dienas
How do I stop a file transfer on AnyDesk?
Disable File Transfer in for the profile you wish to disable it for in Settings > Security > Permissions > Permission Profile. The first option will disable clipboard sync in both directions for both text and files while the second will only disable file transfer using the clipboard.
How do I uninstall AnyDesk?
Method 2: Uninstall AnyDesk via Apps and Features/Programs and Features. Look for AnyDesk in the list and click on it. The next step is to click on uninstall, so you can initiate the uninstallation.
What is privacy mode on AnyDesk?
AnyDesk Privacy Mode allows you to blacken the screen of your remote device and still work on it as if you were sitting right in front of it. Nobody can view your screen and your data is safe.
How do I stop a file transfer on AnyDesk?
Disable File Transfer in for the profile you wish to disable it for in Settings > Security > Permissions > Permission Profile. The first option will disable clipboard sync in both directions for both text and files while the second will only disable file transfer using the clipboard.
Does AnyDesk require admin rights?
When AnyDesk, and by extension, the AnyDesk Service, is installed on the remote device, it can interact with any software that requires administrative privileges as well as UAC elevation requests.
How do I restrict access to AnyDesk?
You can find the Access Control List in the security tab of the AnyDesk settings. In order to activate access control, the security tab has to be unlocked. Use the + button to add an entry. A text entry will appear at the bottom of the list.
How does AnyDesk unattended remote access work?
To use Unattended Access, setting up a password on the remote device is required. This is done in the security settings. You only get access to the remote device, when you enter this password in a dialog window. The window appears after you requested a session.
Where is AnyDesk password stored?
To recover your password, go to my.anydesk.com and click “Forgot your password?”. This will send a password reset email to the one registered to your account.
What can a scammer do with remote access to your computer?
In a remote access scam, a scammer attempts to persuade you into giving them remote control over your personal computer, which allows the scammer to con money out of you and steal your private information.
How do I reset my AnyDesk settings?
There is a simple way to force a reset. Exit the running AnyDesk instance, then go to C:\ProgramData\Anydesk. Your ID and Alias is stored in the service. conf.
Does AnyDesk use camera?
He simply uses AnyDesk: Almost every laptop has a built-in webcam, and with AnyDesk, you can turn it on from anywhere and have a clear view of your room. That’s where you’ll find your kitties sleeping soundly. Be sure to use a strong password and disconnect the session afterwards.
What can be accessed through AnyDesk?
AnyDesk is a remote desktop application distributed by AnyDesk Software GmbH. The proprietary software program provides platform independent remote access to personal computers and other devices running the host application. It offers remote control, file transfer, and VPN functionality.
How do I set up access control in AnyDesk?
Setting up your whitelist You can find the Access Control List in the security tab of the AnyDesk settings. In order to activate access control, the security tab has to be unlocked. Use the + button to add an entry.
How do I block AnyDesk from running on Windows?
You can utilise Group Policy to deny AnyDesk.exe from running. To do this, create a new Software Restriction Policy with a Hash Rule for AnyDesk.exe. If you have a firewall with Deep Packet Exception, you can enable the in-built rules to block AnyDesk.
What is AnyDesk and how does it work?
Keep in mind that AnyDesk only works for authorized remote access, which naturally means that you can’t access just any computer. In other words, not only your computer needs to have AnyDesk installed, but devices that you want to access as well.
How do I set up my whitelist in AnyDesk?
Setting up your whitelist. You can find the Access Control List in the security tab of the AnyDesk settings. In order to activate access control, the security tab has to be unlocked. Use the + button to add an entry. A text entry will appear at the bottom of the list. Entries can be removed using the “-” button after they have been selected.