In dual-mode operation, there are two separate modes: monitor mode (also called ‘system mode’ and ‘kernel mode’) and user mode. In monitor mode, the CPU can use all instructions and access all areas of memory. In user mode, the CPU is restricted to unprivileged instructions and a specified area of memory.
How does dual mode achieve its purpose?
The dual-mode operations in the operating system protect the operating system from illegal users. We accomplish this defense by designating some of the system instructions as privileged instructions that can cause harm. The hardware only allows for the execution of privileged instructions in kernel mode.
How does dual mode provide protection?
The dual mode of operation provides us with the means for protecting the OS from errant users-and errant users from one another. If an attempt is made to execute a privileged instruction in user mode, the hardware does not execute the instruction but rather treats it as illegal and traps it to the OS.
What are the uses of having two modes of operation in CPU?
Multiple modes could be used to provide a finer-grained security policy. For example, rather than distinguishing between just user and kernel mode, you could distinguish between different types of user mode. Perhaps users belonging to the same group could execute each other’s code.
How a computer system switches from one mode to another?
The processor switches between the two modes depending on what type of code is running on the processor. Applications run in user mode, and core operating system components run in kernel mode.
How does dual mode achieve its purpose?
The dual-mode operations in the operating system protect the operating system from illegal users. We accomplish this defense by designating some of the system instructions as privileged instructions that can cause harm. The hardware only allows for the execution of privileged instructions in kernel mode.
How does dual mode provide protection?
The dual mode of operation provides us with the means for protecting the OS from errant users-and errant users from one another. If an attempt is made to execute a privileged instruction in user mode, the hardware does not execute the instruction but rather treats it as illegal and traps it to the OS.
How does the computer ensure CPU protection?
CPU protection is referred to as we can not give CPU to a process forever, it should be for some limited time otherwise other processes will not get the chance to execute the process. So for that, a timer is used to get over from this situation.
How does the CPU respond to system call?
The CPU reacts to this by looking in the Interrupt Descriptor Table to find the kernel’s handler for that interrupt. This handler is the entry point for system calls.
Does dual boot affect performance?
Essentially, dual booting does affect performance, and will slow down your computer or laptop. While a Linux OS may use the hardware more efficiently overall, as the secondary OS it is at a disadvantage.
What is dual mode and multi mode?
The concept of modes of operation in operating system can be extended beyond the dual mode. This is known as the multimode system. In those cases the more than 1 bit is used by the CPU to set and handle the mode. An example of the multimode system can be described by the systems that support virtualisation.
What is meant by CPU protection?
CPU protection protects the CPU of the node that it is configured on from a DOS attack by limiting the amount of traffic coming in from one of its ports and destined to the CPM (to be processed by its CPU) using a combination of the configurable limits.
Why are two modes user and kernel needed?
Why are two modes (user and kernel) needed? User mode prohibits the user from accessing certain areas of memory and executing certain instructions to protect the OS. Kernel mode gives full access to the OS to allow it to do what it needs to do.
What are the 2 modes of the operating system?
There are two modes of operation in the operating system to make sure it works correctly. These are user mode and kernel mode.
How many operations per second can a CPU do?
With every tick of the clock, the CPU fetches and executes one instruction. The clock speed is measured in cycles per second, and one cycle per second is known as 1 hertz. This means that a CPU with a clock speed of 2 gigahertz (GHz) can carry out two thousand million (or two billion) cycles per second.
What are the three types of switching modes?
There are three types of switching modes: Store-and-forward. Cut-through. Fragment-free.
Is CPU scheduling necessary?
If most of the running processes change their state from running to waiting then there may always be a possibility of deadlock in the system. Hence to reduce this overhead, the OS needs to schedule the jobs to get the optimal utilization of CPU and to avoid the possibility to deadlock.
What does dual mode mean?
Dual mode refers to mobile devices that function on two different bearer technologies, such as GSM and WCDMA, or 1x and WCDMA. Most 3G phones are dual-mode and tri- or quad- band to enable users to roam onto 2G networks when they are outside the 3G coverage area.
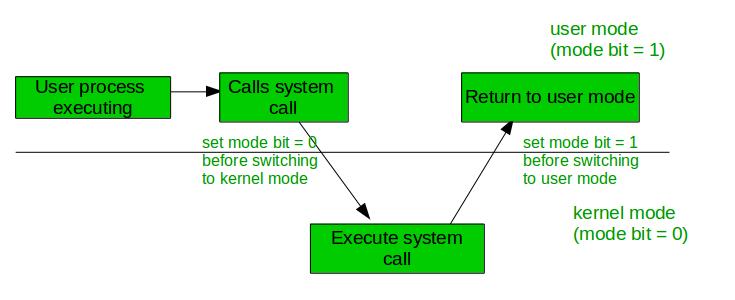
What is the purpose of mode bit?
A bit, called the mode bit, is added to the hardware of the computer to indicate the current mode: kernel(0) or user(1). With the mode bit, we are able to distinguish between a task that is executed on behalf of the operating system and one that is executed on behalf of the user.
What are the three main purposes of an operating system?
An operating system has three main functions: (1) manage the computer’s resources, such as the central processing unit, memory, disk drives, and printers, (2) establish a user interface, and (3) execute and provide services for applications software.
What are the two modes of operation for an operating system?
There are two modes of operation in the operating system to make sure it works correctly. These are user mode and kernel mode.
How does dual mode achieve its purpose?
The dual-mode operations in the operating system protect the operating system from illegal users. We accomplish this defense by designating some of the system instructions as privileged instructions that can cause harm. The hardware only allows for the execution of privileged instructions in kernel mode.