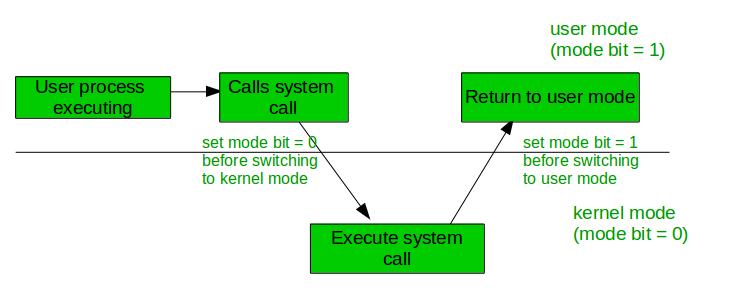
The dual-mode operations in the operating system protect the operating system from illegal users. We accomplish this defense by designating some of the system instructions as privileged instructions that can cause harm. The hardware only allows for the execution of privileged instructions in kernel mode.
How does dual mode provide protection?
The dual mode of operation provides us with the means for protecting the OS from errant users-and errant users from one another. If an attempt is made to execute a privileged instruction in user mode, the hardware does not execute the instruction but rather treats it as illegal and traps it to the OS.
What are the uses of having two modes of operation in CPU?
Multiple modes could be used to provide a finer-grained security policy. For example, rather than distinguishing between just user and kernel mode, you could distinguish between different types of user mode. Perhaps users belonging to the same group could execute each other’s code.
How does the computer ensure CPU protection?
CPU protection is referred to as we can not give CPU to a process forever, it should be for some limited time otherwise other processes will not get the chance to execute the process. So for that, a timer is used to get over from this situation.
How does dual mode provide protection?
The dual mode of operation provides us with the means for protecting the OS from errant users-and errant users from one another. If an attempt is made to execute a privileged instruction in user mode, the hardware does not execute the instruction but rather treats it as illegal and traps it to the OS.
What is the meaning of dual mode?
Dual mode refers to mobile devices that function on two different bearer technologies, such as GSM and WCDMA, or 1x and WCDMA. Most 3G phones are dual-mode and tri- or quad- band to enable users to roam onto 2G networks when they are outside the 3G coverage area.
What is the importance of protection in a multi user system?
Protection is especially important in a multiuser environment when multiple users use computer resources such as CPU, memory, etc. It is the operating system’s responsibility to offer a mechanism that protects each process from other processes.
How CPU and memory are protected by the operating system?
In Memory protection, we have to protect the operating system from user processes and which can be done by using a relocation register with a limit register. Here, the relocation register has the value of the smallest physical address whereas the limit register has the range of the logical addresses.
What is meant by CPU protection?
CPU protection protects the CPU of the node that it is configured on from a DOS attack by limiting the amount of traffic coming in from one of its ports and destined to the CPM (to be processed by its CPU) using a combination of the configurable limits.
Why are two modes user and kernel mode needed?
Why are two modes (user and kernel) needed? User mode prohibits the user from accessing certain areas of memory and executing certain instructions to protect the OS. Kernel mode gives full access to the OS to allow it to do what it needs to do.
What protection is needed for computer?
Safeguarding against malware The best way to guard against malware is to install antivirus software, such as Bitdefender, Norton, or Kaspersky. Antivirus software helps to prevent malware from being installed, and it can also remove malware from your computer.
What provides protection for the internal parts of the computer?
Case. The computer case encloses most of the components of the system. It provides mechanical support and protection for internal elements such as the motherboard, disk drives, and power supplies, and controls and directs the flow of cooling air over internal components.
Is dual boot secure?
Dual Booting Windows 10 and Linux Is Safe, With Precautions Ensuring your system is set up correctly is important and can help to mitigate or even avoid these issues. Backing up data on both partitions is wise, but this should be a precaution you take anyway.
What is dual mode wireless?
Now an emerging technology known as dual mode combines cellular and Wi-Fi radio communication in a single device.
What is dual mode and multi mode?
The concept of modes of operation in operating system can be extended beyond the dual mode. This is known as the multimode system. In those cases the more than 1 bit is used by the CPU to set and handle the mode. An example of the multimode system can be described by the systems that support virtualisation.
What is a dual device?
Dual-mode devices can operate on two different forms of data transmission or network. They have two types of cellular radios: code division multiple access (CDMA) and Global System for Mobile Communication (GSM) for voice and data transmission.
How does dual mode provide protection?
The dual mode of operation provides us with the means for protecting the OS from errant users-and errant users from one another. If an attempt is made to execute a privileged instruction in user mode, the hardware does not execute the instruction but rather treats it as illegal and traps it to the OS.
What is the meaning of dual use?
Dual-use items are goods, technology and software that can be used for both civil and military purposes. This includes all goods which can be used for both non-explosive uses and assisting in any way in the manufacture of nuclear weapons or other nuclear explosive devices.
What is dual mode and multi mode?
The concept of modes of operation in operating system can be extended beyond the dual mode. This is known as the multimode system. In those cases the more than 1 bit is used by the CPU to set and handle the mode. An example of the multimode system can be described by the systems that support virtualisation.
What is a dual device?
Dual-mode devices can operate on two different forms of data transmission or network. They have two types of cellular radios: code division multiple access (CDMA) and Global System for Mobile Communication (GSM) for voice and data transmission.
What is the purpose of protection?
Protection refers to keeping something or someone safe. Through protection, we shelter and defend things. Since protecting is to shelter from harm, protection is the act of doing so. Children are under the protection of their parents, who keep them safe.
Why is it important to protect the computer?
Malicious viruses or spyware could be deposited on your computer, slowing it down or destroying files. By using safety measures and good practices to protect your devices, you can protect your privacy and your family.