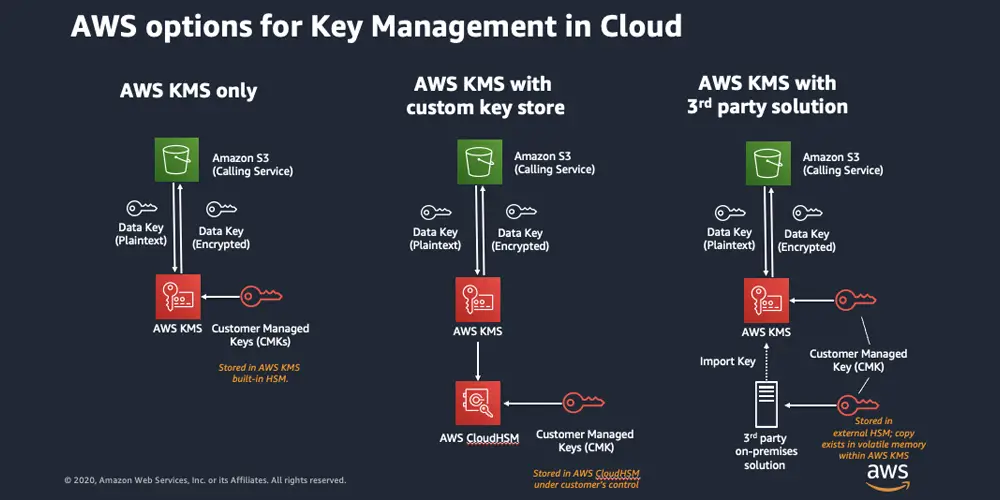
AWS KMS is responsible for the security of the master key. Master keys are stored and managed by AWS KMS and never leave the HSM unencrypted. Benefits of Envelope Encryption: Protecting data keys: The data keys are inherently protected by encrypting them with CMKs.
Can Amazon access my KMS keys?
AWS KMS is designed so that no one, including AWS employees, can retrieve your plaintext KMS keys from the service. AWS KMS uses hardware security modules (HSMs) that have been validated under FIPS 140-2, or are in the process of being validated, to protect the confidentiality and integrity of your keys.
Does AWS KMS store the keys?
AWS KMS generates, encrypts, and decrypts data keys. However, AWS KMS does not store, manage, or track your data keys, or perform cryptographic operations with data keys. You must use and manage data keys outside of AWS KMS. For help using the data keys securely, see the AWS Encryption SDK.
Is AWS KMS GDPR compliant?
We can confirm that all AWS services can be used in compliance with the GDPR. AWS offers a GDPR-compliant Data Processing Addendum (GDPR DPA), which enables customers to comply with GDPR contractual obligations.
Can Amazon access my KMS keys?
AWS KMS is designed so that no one, including AWS employees, can retrieve your plaintext KMS keys from the service. AWS KMS uses hardware security modules (HSMs) that have been validated under FIPS 140-2, or are in the process of being validated, to protect the confidentiality and integrity of your keys.
Does AWS have access to my data?
As a customer, you maintain ownership of your content, and you select which AWS services can process, store, and host your content. We do not access or use your content for any purpose without your agreement. We never use customer content or derive information from it for marketing or advertising.
Can KMS keys be automatically rotated?
You cannot automatically rotate asymmetric KMS keys, HMAC KMS keys, KMS keys with imported key material, or KMS keys in custom key stores. However, you can rotate them manually. Select or clear the Automatically rotate this KMS key every year check box.
What are the 3 types of KMS keys?
Choosing a KMS key type. AWS KMS supports several types of KMS keys: symmetric encryption keys, symmetric HMAC keys, asymmetric encryption keys, and asymmetric signing keys. KMS keys differ because they contain different cryptographic key material.
What is the difference between KMS and secrets manager?
AWS KMS returns a plaintext data key and a copy of that data key encrypted under the KMS key. Secrets Manager uses the plaintext data key and the Advanced Encryption Standard (AES) algorithm to encrypt the secret value outside of AWS KMS. It removes the plaintext key from memory as soon as possible after using it.
What is AWS KMS encryption?
AWS Key Management Service (AWS KMS) is a service that combines secure, highly available hardware and software to provide a key management system scaled for the cloud. Amazon S3 uses AWS KMS keys to encrypt your Amazon S3 objects. AWS KMS encrypts only the object data.
Is AWS a data processor under GDPR?
Is AWS a data processor or a data controller under the GDPR? AWS acts as both a data processor and a data controller under the GDPR. AWS as a data processor – When customers use AWS services to process personal data in the content they upload to the AWS services, AWS acts as a data processor.
Does GDPR require encryption at rest?
Although not mandatory under the GDPR, encryption of personal data helps companies to reduce the probability of a breach and thus avoid fines. Encryption can ensure protection for both data in motion and at rest.
How does Amazon Protect data?
We work to protect the security of your personal information during transmission by using encryption protocols and software. We follow the Payment Card Industry Data Security Standard (PCI DSS) when handling credit card data.
Does AWS automatically encrypt data?
All data flowing across AWS Regions over the AWS global network is automatically encrypted at the physical layer before it leaves AWS secured facilities. All traffic between AZs is encrypted. Additional layers of encryption, including those listed in this section, may provide additional protections.
Why do we use KMS?
You can use your KMS keys to encrypt small amounts of data (up to 4096 bytes). However, KMS keys are typically used to generate, encrypt, and decrypt the data keys that encrypt your data outside of AWS KMS. Unlike KMS keys, data keys can encrypt data of any size and format, including streamed data.
What is the difference between KMS and secrets manager?
AWS KMS returns a plaintext data key and a copy of that data key encrypted under the KMS key. Secrets Manager uses the plaintext data key and the Advanced Encryption Standard (AES) algorithm to encrypt the secret value outside of AWS KMS. It removes the plaintext key from memory as soon as possible after using it.
What is AWS KMS used for?
AWS Key Management Service (KMS) gives you centralized control over the cryptographic keys used to protect your data. The service is integrated with other AWS services making it easy to encrypt data you store in these services and control access to the keys that decrypt it.
Where are encryption keys stored?
The encryption key is created and stored on the key management server. The key manager creates the encryption key through the use of a cryptographically secure random bit generator and stores the key, along with all it’s attributes, into the key storage database.
Can Amazon access my KMS keys?
AWS KMS is designed so that no one, including AWS employees, can retrieve your plaintext KMS keys from the service. AWS KMS uses hardware security modules (HSMs) that have been validated under FIPS 140-2, or are in the process of being validated, to protect the confidentiality and integrity of your keys.
Is AWS encrypted?
The process of envelope encryption is used in all AWS services in which data is encrypted on a customer’s behalf (which is known as server-side encryption) to minimize performance degradation.
Who owns the data in the cloud?
The short answer is that you own the data you create, but the cloud service provider has ultimate control over it. This is reflected in many providers’ terms of service which state that they can hold on to the data to comply with legal regulations.
Where is Amazon data stored?
According to the “Amazon Atlas” document, Amazon operates in 38 facilities in Northern Virginia, eight in San Francisco, eight in Seattle, and seven in Oregon. In Europe it has seven data centers in Dublin, Ireland, four in Germany, and three in Luxembourg.