Yes, KMS activation is illegal for Windows. If you activate through the KMS method then your copy of Windows would not be considered genuine by Windows.
Is KMS activation legal?
Activation servers (KMS) through an organization or educational institution is legal, and should be used for those intents and purposes.
Is activation through KMS server safe?
Microsoft’s Defender will find the KMS activater as a threat and other antivirus software will also do it. We have no information if this kind of tools have malware, we simply advise not to use it. If you do want to use illegal software please use it at your own risk.
Is KMS Msguides legal?
That is not legal. It is just another software piracy website.
Is KMS activation permanent?
KMS activations are valid for 180 days (the activation validity interval). KMS client computers must renew their activation by connecting to the KMS host at least once every 180 days. By default, KMS client computers attempt to renew their activation every 7 days.
Can KMS server control your PC?
AFIK the KMS Server has no other rights or privileges on your computer.
Is KMS genuine?
Yes, KMS activation is illegal for Windows. If you activate through the KMS method then your copy of Windows would not be considered genuine by Windows.
What is KMS license?
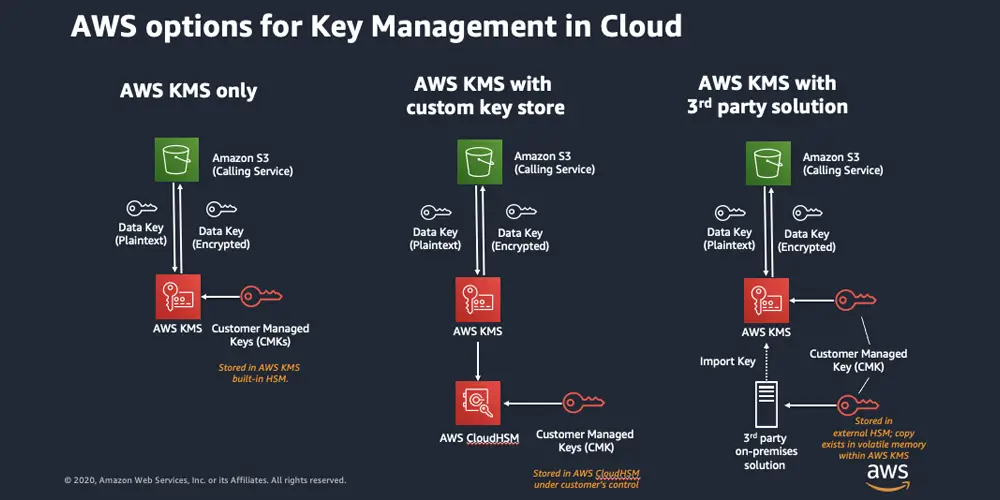
The Key Management Service (KMS) is an activation service that allows organizations to activate systems within their own network, eliminating the need for individual computers to connect to Microsoft for product activation.
What is online KMS activation?
KMS uses a client-server model to active clients and is used for volume activation. KMS clients connect to a KMS server, called the KMS host, for activation. The KMS host must reside on your local network. KMS hosts do not need to be dedicated servers, and KMS can be cohosted with other services.
Is KMS client key safe?
No, it isn’t safe to use either kms activation or any other activation software, specially if they use (as you said) unknown host server beacause this will provide them a kind of backdore to your system by which they might track your files or sensitive information.
Is KMS Msguides com safe?
Its safe. win 10 allows piracy and you’ll also get updates.
What does a KMS server do?
The KMS Server is the Key Management Server for Microsoft product activation, primarily OS activation. An organization can configure a KMS Server to service all activation requests in the enterprise.
Can I activate Windows 10 for free?
Microsoft allows anyone to download Windows 10 for free and install it without a product key. It’ll keep working for the foreseeable future, with only a few small cosmetic restrictions. And you can even pay to upgrade to a licensed copy of Windows 10 after you install it.
Is activating Windows 10 for free illegal?
Is Windows 10 Illegal Without Activation? No. Microsoft now allows users to use Windows 10 for free and without the need to activate your PC. Just that, there will be a watermark and some customization features will be disabled under the free version.
What is KMS activation?
The Key Management Service (KMS) is an activation service that allows organizations to activate systems within their own network, eliminating the need for individual computers to connect to Microsoft for product activation.
What is online KMS activation?
KMS uses a client-server model to active clients and is used for volume activation. KMS clients connect to a KMS server, called the KMS host, for activation. The KMS host must reside on your local network. KMS hosts do not need to be dedicated servers, and KMS can be cohosted with other services.
Is KMS Msguides com safe?
Its safe. win 10 allows piracy and you’ll also get updates.
What port does KMS activation use?
KMS TCP listening port – By default, the KMS host is listening on port 1688 (TCP). You can change the port if needed using this setting.
Is KMS activation safe Quora?
Nope, It’s not. But mostly security products recognize it as a Malware or Trojan, because it’s from a unknown publisher, make an entry in your system services and it’s behavior.
Does KMS server require Internet access?
The main advantages of KMS activation: KMS clients do not need to access the Internet or the phone to activate the product (only network access to the KMS server is required);
How does Windows find KMS server?
When a supported version of Windows or Office is installed, the computer will attempt to discover the KMS Server on the network. This is accomplished by checking for an SRV record in the DNS Zone of the computer.
How often does KMS client check?
To remain activated, KMS client computers must renew their activation by connecting to the KMS host at least once every 180 days. By default, KMS client computers attempt to renew their activation every 7 days. If KMS activation fails, the client computer retries every two hours.