What is memory caching? Memory caching (often simply referred to as caching) is a technique in which computer applications temporarily store data in a computer’s main memory (i.e., random access memory, or RAM) to enable fast retrievals of that data. The RAM that is used for the temporary storage is known as the cache.
Is cache memory RAM or ROM?
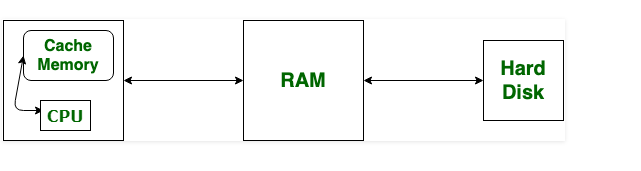
Two types of RAM are Static RAM, or (SRAM), and Dynamic RAM, or (DRAM). 2. Cache Memory : The cache is a smaller and fast memory component in the computer which is inserted between the CPU and the main memory.
Where is cache memory stored?
Cache Memory and Performance The cache memory is located very close to the CPU, either on the CPU chip itself or on the motherboard in the immediate vicinity of the CPU and connected by a dedicated data bus.
Is cache stored in RAM or CPU?
RAM is the main type of computer data storage that stores information and program processes. It’s farther away from the CPU than cache memory and isn’t as fast; cache is actually 100 times faster than standard RAM. If cache is so fast, why isn’t all data stored there?